Viewing Threat Details
This section covers how to view and examine threat details for both open and closed threats in the threat hunting interface.
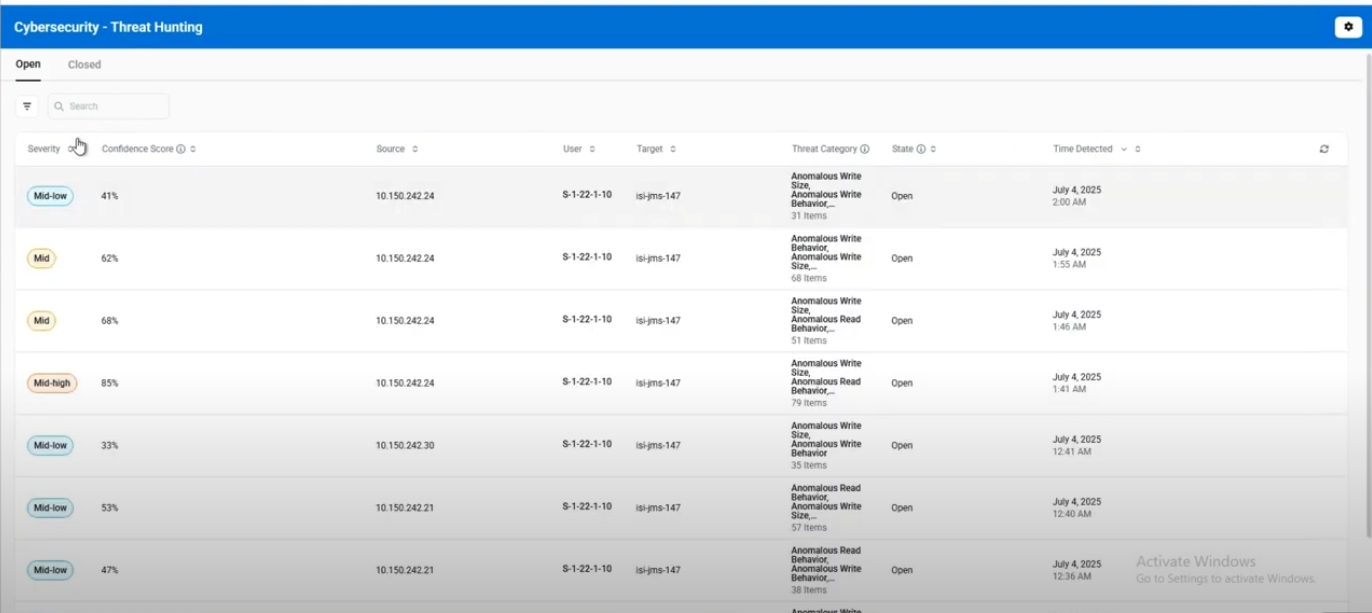
Viewing Open Threats
Open Threats are newly detected security events that require investigation and action. Click any open threat from the list to open the details panel on the right side.
Open Threat Details Panel
-
Header Information
- Event ID: Unique identifier for the threat hunting event
- Detection Date/Time: When the anomaly was detected
- Close button (X): Closes the slide-out panel
-
Threat Categories Section Lists detected anomaly types with descriptions of the unusual behavior patterns detected. For more details, see Detection Types.
-
Key Metrics
- Severity: Threat level (LOW, MID_LOW, MID, MID_HIGH, or HIGH)
- Confidence Score: Percentage value (examples: 75%, 88.5%, 95%)
-
Items Affected Section
- File Paths: Specific files and folders affected
- File Types: Types of files involved in the anomaly
- Extensions: File extensions, including any new extensions added
- Search Capability: Search within the affected items list
-
Data Types Used Shows file extensions and types involved in the anomalous activity (example: txt, docx, pdf)
-
Details Section Expandable section with comprehensive threat information:
- Severity: Threat level classification
- Source: Client IP address where activity originated
- Target: Storage device being monitored
- Items Affected Count: Number of files involved
- Threat Categories: Types of anomalous behavior detected
- State: Current processing status (Open)
- Time Detected: When the anomaly was first identified
- Event ID: Unique identifier for the threat event
-
Action Buttons
- "Take an Action": Close as expected behavior or confirmed anomaly (see Response Procedures)
- "Investigate →": Navigate to detailed investigation page that displays the same information but allows you to get a closer look and search through files for deeper threat analysis (see Investigating Threats)
Viewing Closed Threats
Closed threats are security events where an action has been taken, moving them from the Open Threats tab to the Closed Threats tab. Navigate to the Closed tab to view all completed threat investigations.
Closed Threat Details Panel
Click any closed threat to open the details panel showing the same information as open threats, but in read-only mode:
-
Header Information
- Event ID: Unique identifier for the threat hunting event
- Detection Date/Time: When the anomaly was originally detected
- Close button (X): Closes the slide-out panel
-
Threat Categories Section Lists the original anomaly types detected with behavior pattern descriptions. For more details, see Detection Types.
-
Key Metrics
- Severity: Original threat level (LOW, MID_LOW, MID, MID_HIGH, or HIGH)
- Confidence Score: Original ML confidence percentage (examples: 75%, 88.5%, 95%)
-
Items Affected Section
- File Paths: Original files and folders that were affected
- File Types: Types of files involved in the original anomaly
- Extensions: File extensions, including any new extensions that were added
- Search Capability: Search within the original affected items list
-
Data Types Used Shows the original file extensions and types involved in the anomalous activity (example: txt, docx, pdf)
-
Details Section Expandable section with the original comprehensive threat information:
- Severity: Original threat level classification
- Source: Client IP address where activity originated
- Target: Storage device that was monitored
- Items Affected Count: Number of files involved
- Threat Categories: Types of anomalous behavior detected
- State: Current processing status (Closed)
- Time Detected: When the anomaly was first identified
- Event ID: Unique identifier for the threat event
-
Resolution Information
- Closure Method: How the threat was closed (Expected Behavior or Anomaly Confirmed)
- Closure Timestamp: When the action was taken
- User: Who took the closing action
- Comments: Any comments added during closure
-
Investigation Button
- "Investigate →": Navigate to detailed investigation page for historical review and analysis of the closed threat (see Investigating Threats)
Investigating Threats
When you click the Investigate button, the system opens a dedicated investigation page showing the same threat information as the details panel but with enhanced search capabilities.
Use the investigation page to search through affected files, filter data, analyze patterns, and add comments before taking action. This deeper analysis helps you make the correct classification decision.
Unlike open threats, closed threats cannot be reopened or have their status changed. You can investigate for historical review and add comments for audit purposes, but cannot take new actions.
See Also
- Response Procedures - Procedures for responding to detected threats
- Detection Types - Complete list of threat detection types and descriptions
- Threat Hunting Configuration - How to configure threat hunting settings