Response Procedures
This section covers the procedures for responding to detected threats, including investigation workflows and available actions.
Understanding Open vs Closed Threats
Open Threats are newly detected security events that require investigation and action. Taking any action on an open threat moves it to the Closed Threats tab, where you can view the threat log, handling details, and comments. Actions can no longer be taken on closed threats.
Taking Action
How to Take Action on a Threat
-
Locate the Action Button
Find the "Take an Action" button in either the threat details panel or investigation page.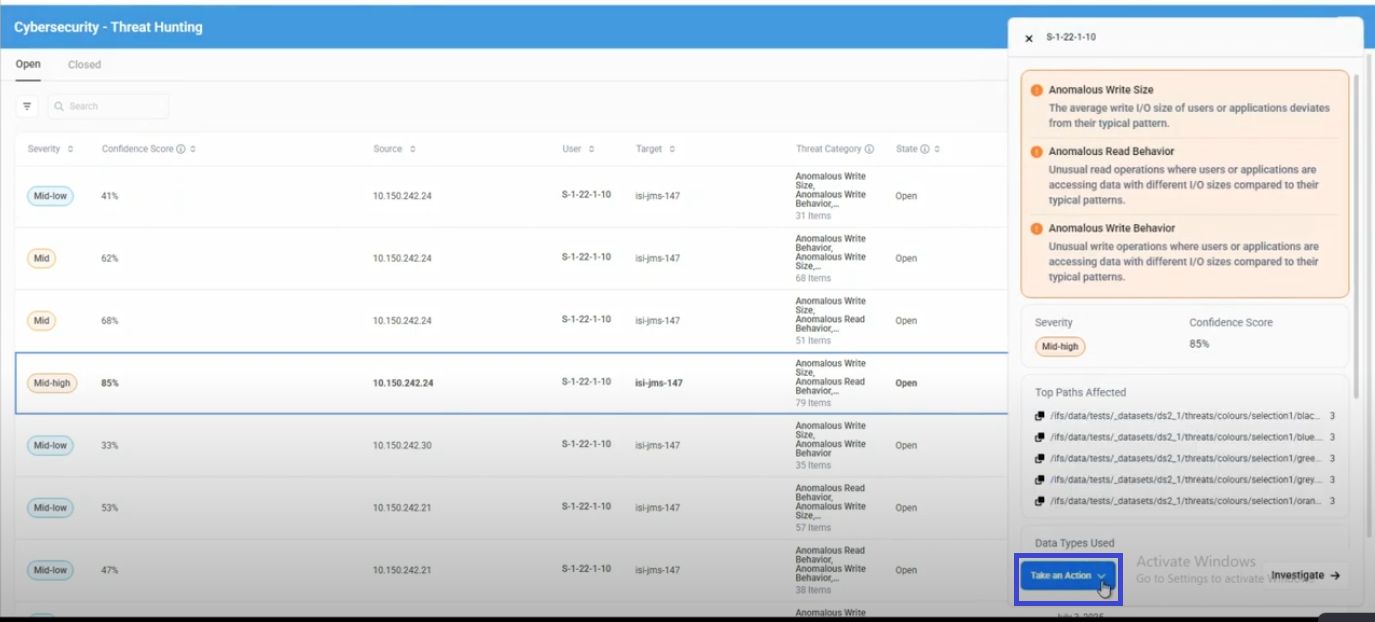
-
Click Take an Action
Click the button to open the action selection dialog. -
Choose Your Response
Select one of two closure options based on your analysis:- Close as Expected Behavior - If this is normal activity for your environment
- Close as Anomaly Confirmed - If this is genuinely suspicious or malicious activity
-
Add Comments (Optional)
Provide additional context or notes about your decision for audit purposes. -
Confirm Your Selection
Click the confirmation button to close the threat. -
Threat Moves to Closed Tab
After confirming your selection, the threat automatically moves to the Closed Threats tab where you can view the threat log, handling details, and comments. The AI learns from this experience to improve future threat detection.
The "Take an Action" button is available in two locations for open threats:
- Threat Details Panel: When you click on a threat from the main threat list
- Investigation Page: When you're conducting detailed analysis of a threat
Close as Expected Behavior
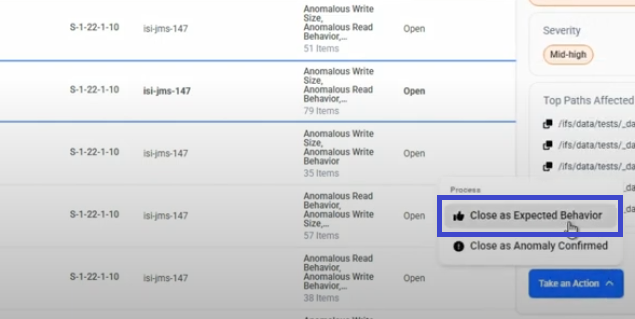
Use this option when the detected activity is normal business operation that should NOT trigger future alerts.
This indicates the detected anomaly is actually normal behavior for this user or application.
The system uses this feedback to retrain the AI for improved accuracy, helping it learn normal patterns in your specific environment and reducing future false positives for similar activities. This helps tune the machine learning algorithms to your environment's unique patterns, reducing alert fatigue for security teams. Your selection will help the system provide more accurate confidence scores for similar activities in the future.
- Developer performing bulk file operations during deployment
- Automated backup systems creating large numbers of files
- Database administrators running maintenance scripts
Close as Anomaly Confirmed
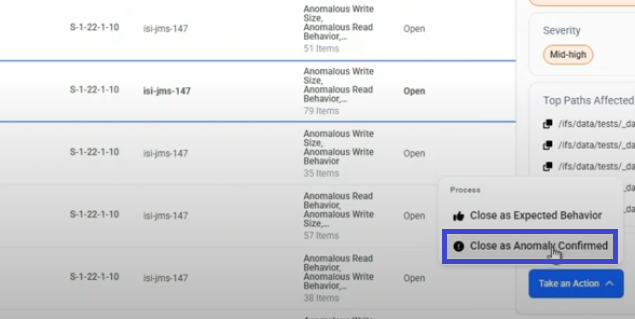
Use this option when you've verified the activity is genuinely suspicious or represents a security concern.
This confirms the anomaly as genuinely suspicious or malicious activity.
Since the AI performed correctly, it does NOT retrain the system. Instead, it confirms the threat detection was accurate and creates a record of an actual security incident for your audit trail. This creates detailed records for compliance and investigation purposes while maintaining the system's sensitivity for detecting similar attack patterns in the future. Your selection validates the system's confidence score accuracy for this type of threat.
- Unauthorized access attempts to sensitive files
- Data exfiltration patterns (unusual large downloads)
- Ransomware-like behavior (mass file encryption/modification)
See Also
- Viewing Threat Details - How to view and examine threat details
- Detection Types - Complete list of threat detection types and descriptions
- Threat Hunting Configuration - How to configure threat hunting settings