Threat Hunting
This section provides an overview of the threat detection interface and how to work with detected threats in your environment.
First Access
Access the threat hunting interface through Eyeglass:
-
Navigate to Ransomware Defender
Go to the Ransomware Defender section in the Eyeglass menu.
-
Click the Threat Hunting tab In the Events section, select the Threat Hunting tab to open the separate threat hunting UI.
-
Authenticate if prompted
Enter your Eyeglass credentials when requested.
The threat hunting interface opens in a separate window for dedicated threat analysis and response.
Understanding the Threat List
The threat detection interface displays comprehensive information about each detected threat:
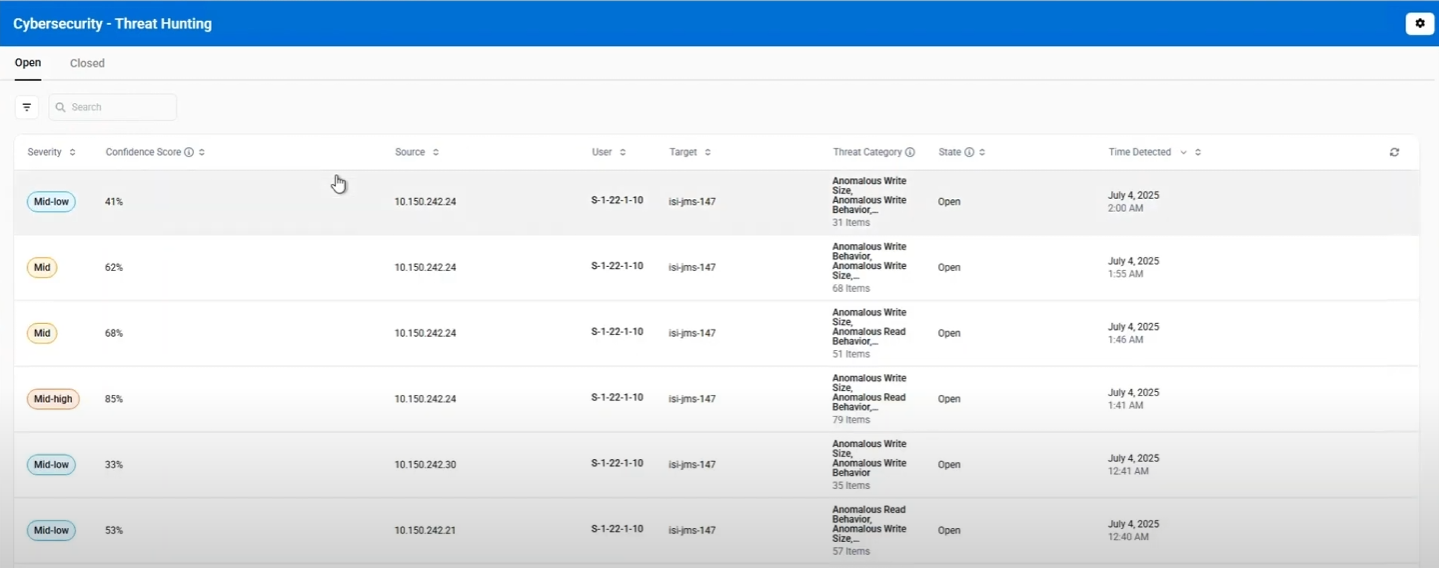
Threat Information Columns
| Column | Description | Example |
|---|---|---|
| Severity | Threat severity level (5 levels) | HIGH, MID_HIGH, MID, MID_LOW, LOW |
| Confidence Score | ML model confidence percentage in threat detection | 88.7%, 95.2%, 75.0% |
| Source | Client IP address where anomalous activity originated | 192.168.1.xx, 10.0.0.xx |
| User | Account associated with the anomalous activity | DOMAIN\\jsmith, local\\admin |
| Target | Storage device being monitored | powerscale-cluster, isilon-prod |
| Threat Category | Type of anomalous behavior detected (see Detection Types) | Various anomaly types based on detected patterns |
| State | Current threat processing status | Open, Closed |
| Time Detected | When the anomaly was first detected | Jun 18, 2025 at 4:48 pm |
Detection Types
Dell Cyber data security identifies various threat categories, from ransomware to data loss prevention. For a complete list of detection types and their descriptions, see the Detection Types Reference.
Threat Severity Levels
Threat Hunting uses 5 severity levels to categorize threat types:
| Severity | Description |
|---|---|
| HIGH | Highly anomalous behavior patterns indicating potential active threats |
| MID_HIGH (med_high) | Significant deviations from normal user activity requiring prompt review |
| MID | Moderate anomalies that may indicate early threat reconnaissance |
| MID_LOW (low_med) | Minor deviations requiring attention |
| LOW | Minimal deviations from baseline behavior patterns |
Confidence Score and Severity Relationship
Threat Hunting uses two independent metrics: Severity Levels categorize the threat type (HIGH, MID_HIGH, MID, MID_LOW, LOW) while Confidence Score represents the machine learning system's certainty percentage (0-100%) that it's a real threat.
A LOW severity event could have a 95% confidence score, while a HIGH severity event could have a 60% confidence score. This independence allows for nuanced threat evaluation and decision-making.
Searching and Filtering
Find specific threats using search and filtering capabilities:
How to Search
-
Access Search Bar
Use the search bar above the threats list. -
Enter Terms
Type any value (username, IP address, threat type). -
View Results
Results update automatically as you type.
How to Filter
-
Open Filters
Click the filter icon next to the search bar. -
Select Options
Choose from these categories:- Severity: HIGH, MID_HIGH, MID, MID_LOW, or LOW
- Confidence Score: Filter by confidence percentage threshold
- Category: Specific threat types (see Detection Types)
- User: Specific user accounts or identities
-
Manage Active Filters
After applying filters:- View Active Filters: Active filters appear as tags at the top
- Check Count: Counter shows applied filters (e.g., "+2")
- Reset Filters: Click "Reset" to clear all filters
Next Steps
Now that you understand the threat hunting interface, explore these operational procedures:
Integrations
Configure webhook integrations with your security stack to forward alerts to SIEM or SOAR platforms
Viewing Threat Details
Learn how to examine detailed information for both open and closed threats
Response Procedures
Understand how to investigate threats and take appropriate actions
See Also
- Threat Hunting Operations - Overview of threat hunting operations
- Threat Hunting Installation - How to install and set up threat hunting
- Detection Types - Complete list of threat detection types and descriptions