Threat Review
Data Security Essentials monitors your file systems and alerts you if it detects suspicious access behavior. Check the sections below to investigate threats, restore user access, or close alerts.
When Data Security Essentials detects suspicious behavior, it takes two key actions:
- It blocks the offending user based on the response settings in the policy triggers.
- It alerts the storage team if you configure notification settings for these policy triggers.
Access the Threat Detections UI to See the Alerts
-
Open Data Security Essentials
Start the application to access its main interface. -
Select Threat Detections
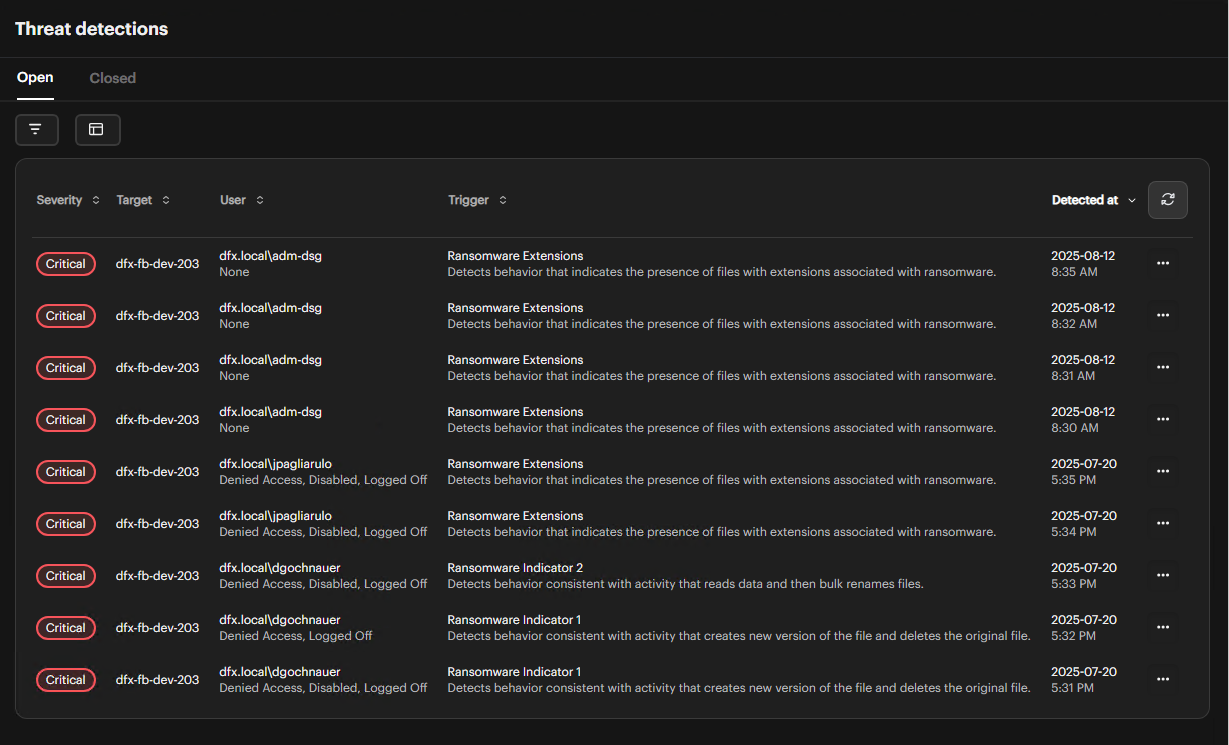
Choose Threat Detections from the left navigation menu. You see active and closed alerts, plus forensic data detailing who accessed which files, when, and what actions occurred.
Review Ongoing Threats
-
Go to the Active Tab
Click the Active tab to see a list of current threats. -
Check Key Columns
Look at the Target, User, Trigger, Severity, and Detected At columns to find the alert you want to investigate.The Severity column displays the priority level of each alert:
- Warning: Lower-priority issues
- Major: Issues needing prompt action
- Critical: Issues requiring immediate response (all ransomware alerts are Critical)
Group Threats by User
You can organize threats by user to review all threats associated with specific users.
-
Enable User Grouping
Select the group by users option in the threat detection interface.
-
View Grouped Results
The interface changes to display threats organized by user. The User column disappears from the main grid, and threats appear in separate grids for each user.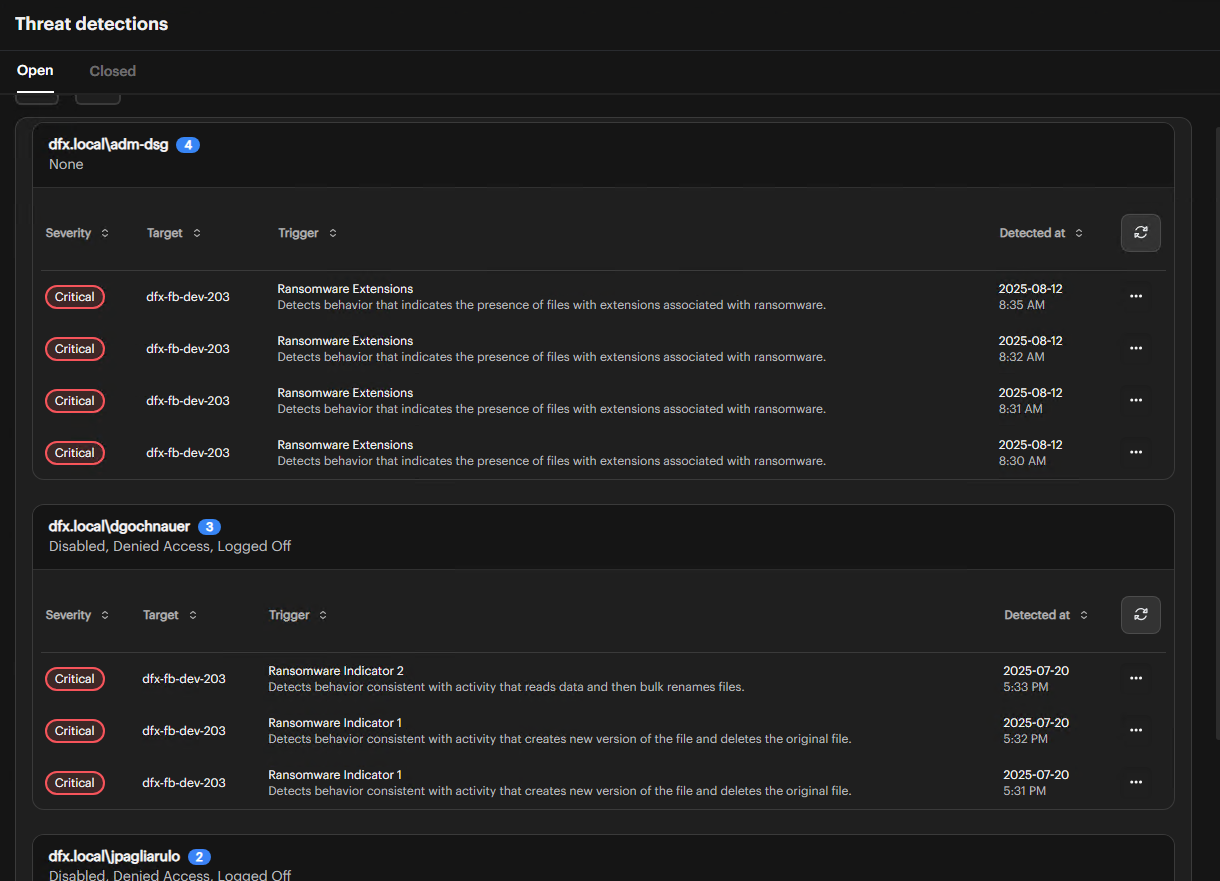
When grouping by users, each user's threats display in their own dedicated grid, making it easier to review all security events associated with specific individuals.
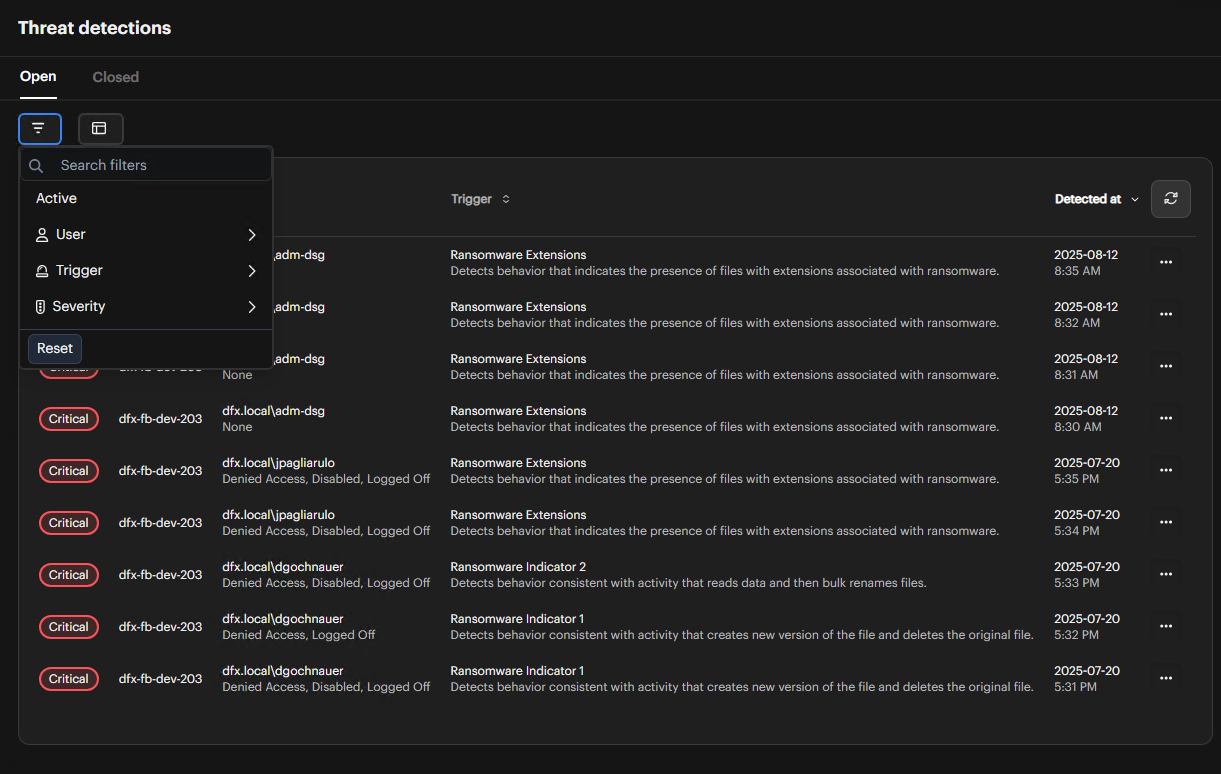
Filter Threats
You can filter the threat detection results to focus on specific security events and patterns.
-
Access Filter Options
Use the filter controls in the threat detection interface to narrow down the displayed threats. -
Apply Filters
Filter threats by the following criteria:- User: Filter to show threats from specific users or user groups
- Trigger: Filter by trigger type (e.g., ransomware, bulk operations, suspicious access patterns)
- Severity: Filter by severity level:
- Critical: Immediate response required
- Major: Prompt action needed
- Warning: Lower-priority issues
-
Combine Filters
Apply multiple filters simultaneously to refine your search and identify specific threat patterns.
Use filters to quickly identify high-priority threats or investigate specific user activities. Combining user and severity filters helps prioritize your incident response efforts.
Investigate an Alert
Gather details about a specific alert.
-
Click the Alert
Select the alert you want to investigate.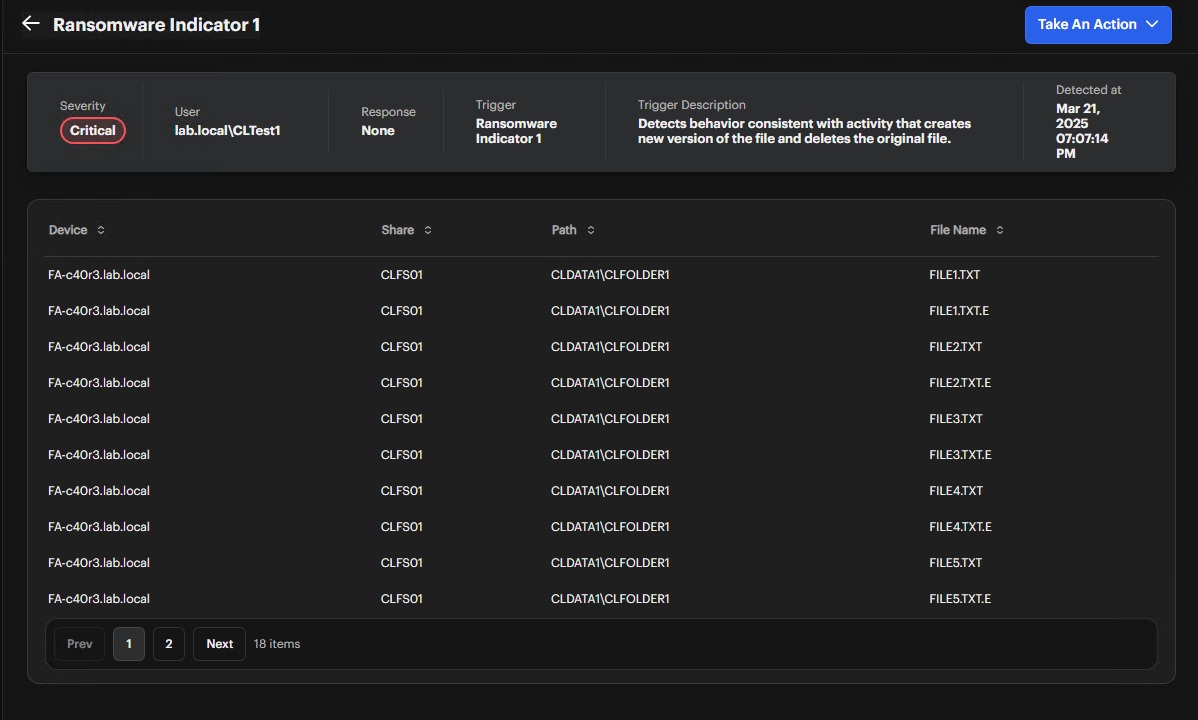
-
Review Alert Fields
Check the User, Response, Trigger, Severity, and Trigger Description fields. -
Check Detected At Timestamp
Note when the alert occurred. -
Locate Suspicious Files
In the table, examine the Device, Share, Path, and File Name columns.
Ransomware alerts are always marked with Critical severity and include specific details about the detected activities.
Take Action
Respond to alerts with appropriate actions.
-
Open the Actions Menu
Click the Take Action button or the ellipsis (...) icon in the Threat Detections list.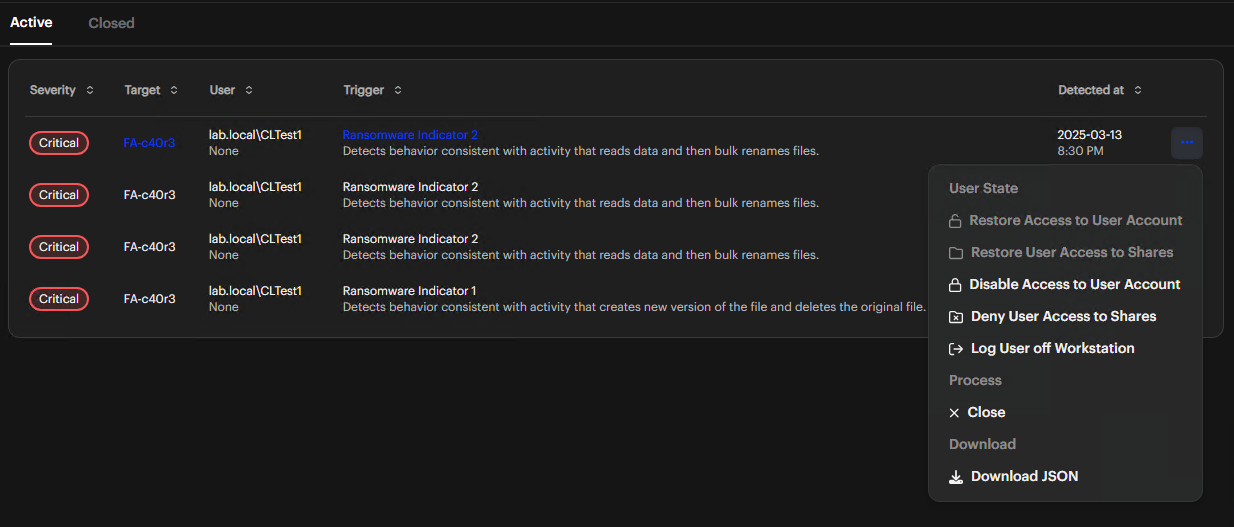
-
Select an Action
- Restore Access to User Account: Re-enable an AD account you disabled
- Restore User Access to Shares: Restore access to shares you blocked
- Disable Access to User Account: Disable an Active Directory account
- Deny User Access to Shares: Block access to network shares
- Log off User Workstation: End the current user session
- Close Threat: Mark a threat as resolved
- Download JSON: Export data for your offline analysis
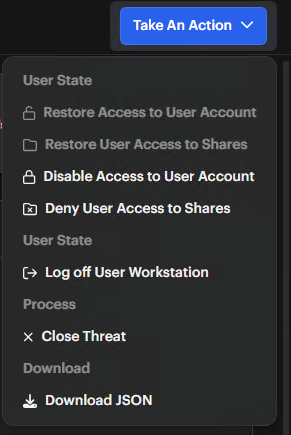 note
noteRansomware policy triggers enable all security action options by default. You can modify these settings as needed.
Restore User Access
Restore access when you need to reinstate permissions that were revoked.
-
Check the User State View the Response field in the alert details. With ransomware threats, you may see Disabled Account or Logged Out.
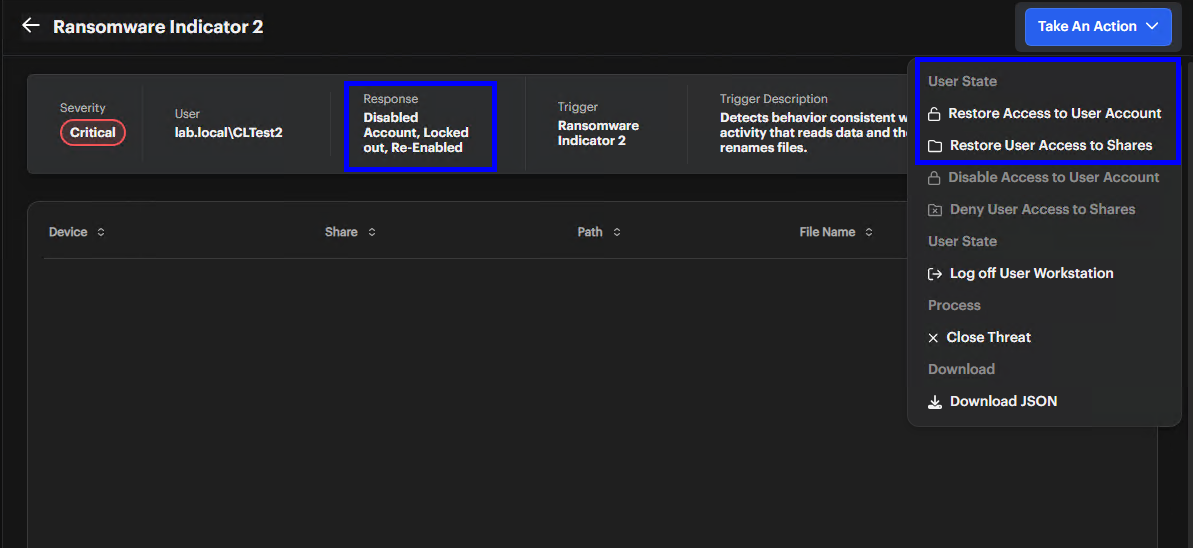
-
Open the Actions Menu Click Take Action. The actions menu opens on the right.
-
Apply the Restoration
- Restore Access to User Account: Re-enables an account you disabled
- Restore User Access to Shares: Restores access to shares you blocked
- Log Off Workstation: After using this action, users must log in again
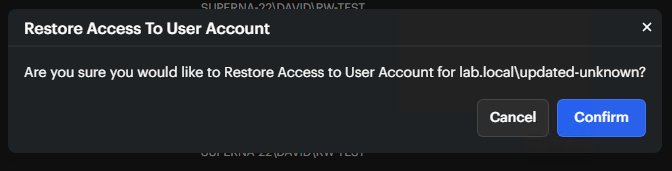
When you select Restore Access to User Account, click Confirm in the dialog to complete your action.