Reports
Data Security Essentials provides report generation to analyze and document your security data. Use reports to monitor user activities, track file operations, verify policy compliance, and maintain audit trails.
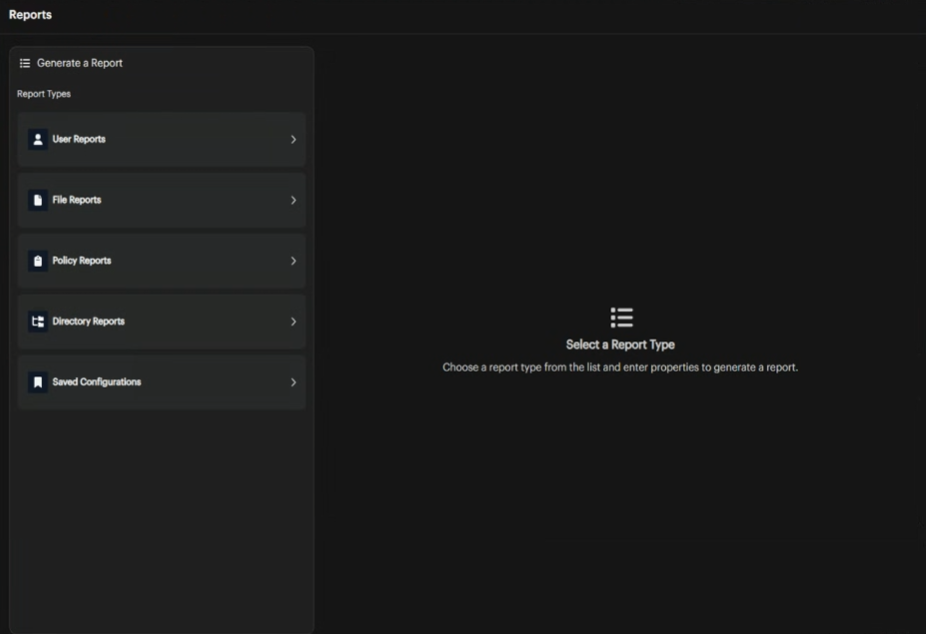
Generate Reports
You can generate reports from the Reports section. When you select a report type, the interface displays different input fields based on your selection.
Report Generation Process
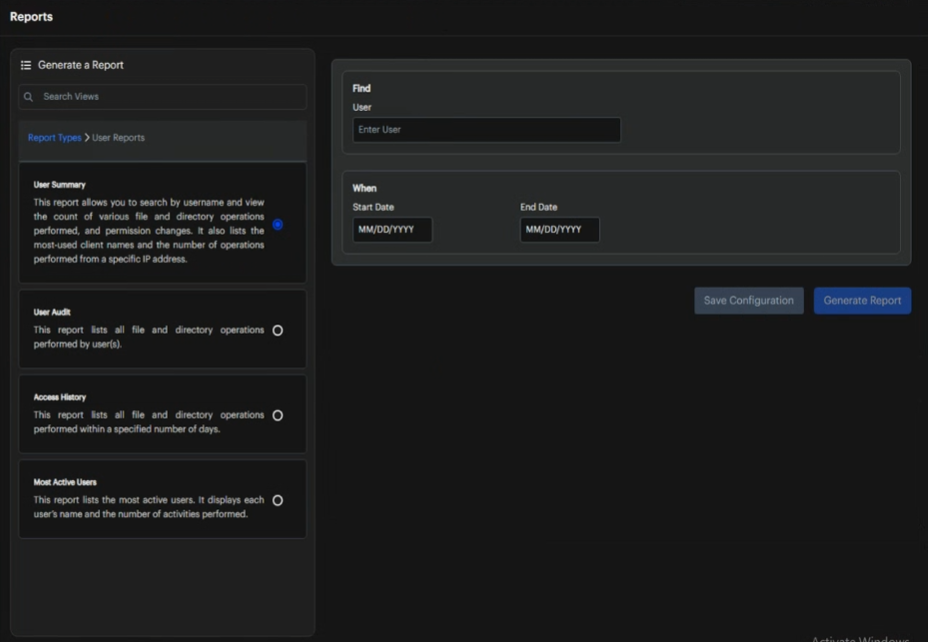
-
Fill Required Information
Complete the input fields specific to your selected report type.Username FormatEnter the user name in the format of fqdn\account.
-
Choose Your Action
- Save Configuration: Save the report configuration to regenerate it later
- Generate Report: Generate the report with current settings
-
View Report Results (Example)
After you click Generate Report, the interface displays your report results.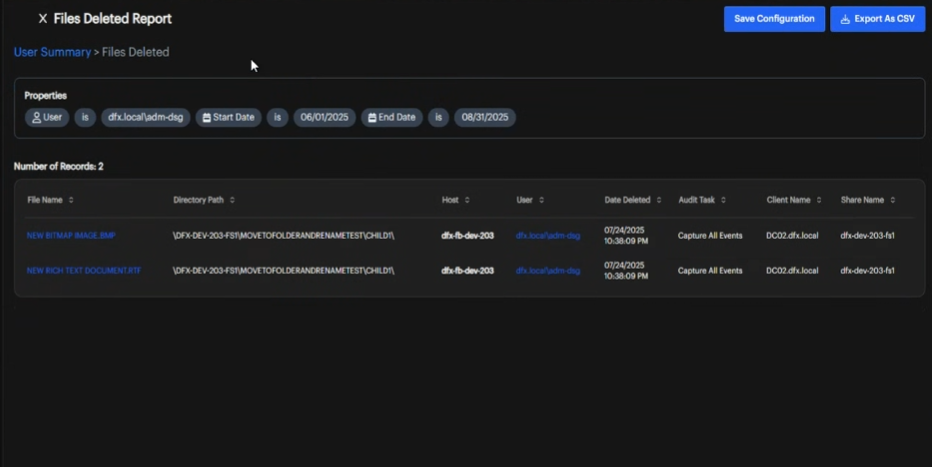
Report Results Interface
The interface displays your generated report data in an organized format with properties and data grids.
Each report's results interface will be different depending on the results and configuration. The interface adapts to show relevant data based on your selected report type and parameters.
Access History Report Example:
Properties Section:
- User name
- Access type (e.g., FILE_OPEN_FOR_READ +12)
- Item name (name of accessed item)
- Time period (e.g., last 20 days)
Data Grid: The report shows the number of records in a spreadsheet format with columns:
-
User: Username who performed the action
-
Item Name: Name of the file or directory accessed
-
Directory Path: Full path to the accessed item
-
Access Type: Type of operation performed
- File Open for Write
- File Close
- Permission Change
- File Open for Read
-
Access Date: When the action occurred
-
Audit Task: Associated audit task
-
Client Name: Name of the client machine
-
Share Name: Network share name
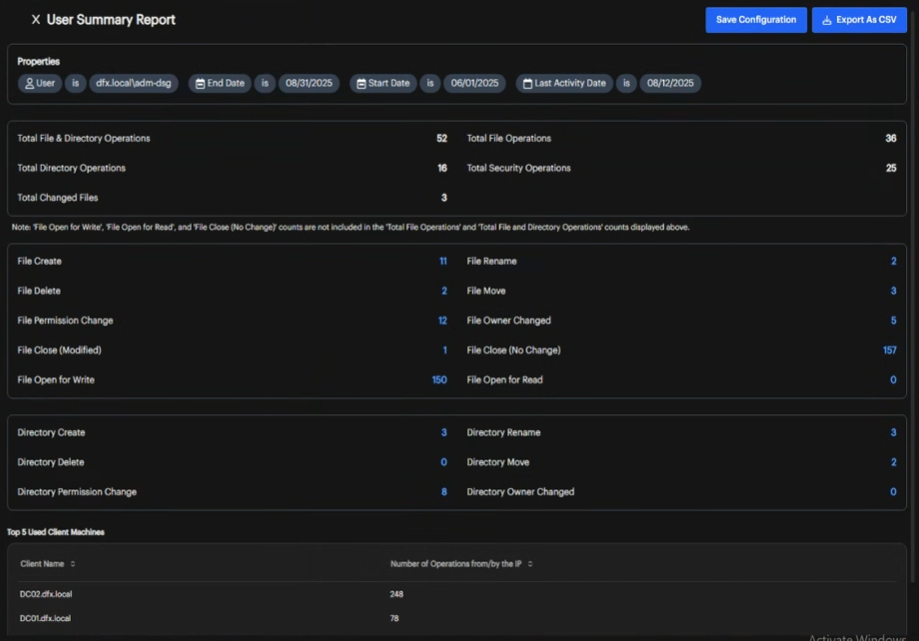
The report data helps you identify security patterns, track user behavior, and investigate potential threats. Use this information to monitor file access trends, detect unusual activities, verify compliance with security policies, and create audit trails for regulatory requirements.
Export and Save Options
In the top right of the report results interface, you have two options:
- Save Configuration: Save the current report settings for future use
- Export as CSV: Download the report data for later review
Report Features and Functionality
Field Configuration
Each report type provides different input fields based on its purpose. Understanding these fields helps you configure reports that meet your specific security analysis needs.
- Default Fields: Available across all report types
- Specific Fields: Unique to each report type based on its purpose
- Required Fields: Must be completed before you can generate the report
- Optional Fields: Provide additional filtering and customization
Date Range Selection
All reports include date range functionality to help you focus your analysis on specific time periods. This feature connects directly with the Report Generation Process when you fill in required information.
- Specify start and end dates for the report period
- Filter data to focus on specific timeframes
Report Types
User Reports
Generate reports about user activities and access patterns. These reports help you monitor user behavior and identify potential security risks.
| Report Type | Description |
|---|---|
| User Summary | Search by username and view the count of file and directory operations and permission changes. Lists the most used client names and the number of operations from specific IP addresses. |
| User Audit | Lists all file and directory operations users performed within a specific number of days. |
| Access History | Provides access history for user activities. |
| Most Active Users | Lists the most active users, displaying each user's name and the number of activities performed. |
File Reports
Generate reports about file access and operations. These reports help you track file activities and maintain security compliance.
| Report Type | Description |
|---|---|
| File Summary | Provides the total count of all updated files with a breakdown of statistics: renamed, created, and changed files. Click a count to show a list of the specified file statistics. |
| File Audit | Lists all operations performed on a file. |
| Files Created | Lists all created files. |
| Files Renamed | Lists all renamed files. |
| Files Deleted | Lists all deleted files. |
| Files Moved | Lists all moved files. |
| Files Changed | Lists all changed files. |
| Deletion Compliance | Lists the files deleted within a specified timeframe and displays the deleted files within the given criteria. |
| File Owner Changed | Lists files with owner changes. |
| File Permission Changed | Lists files with permission modifications. |
Policy Reports
Generate reports about policy configurations and violations. These reports help you verify policy compliance and track configuration changes.
| Report Type | Description |
|---|---|
| Policy by Date | Lists policy details within a specific date range and/or policy name. |
Directory Reports
Generate reports about directory structures and permissions. These reports help you monitor directory activities and maintain proper access controls.
| Report Type | Description |
|---|---|
| Directory Summary | Provides the total count of all audited directories, with a breakdown of deleted, renamed, and created directories. Click a count to show a list of the specified directory operation. |
| Directory Audit | Lists all operations performed on a directory. |
| Directories Created | Lists all created directories. |
| Directories Renamed | Lists all renamed directories. |
| Directories Deleted | Lists all deleted directories. |
| Directory Moved | Lists all moved directories. |
| Deleted Files by Directory | Lists all deleted files grouped by directory. |
| Deleted Files Count by Directory | Lists the number of deleted files within a directory. |
| Most Accessed Directories | Lists the most accessed directories. |
| Directory Owner Changed | Lists directories with ownership changes, displaying the previous and new owners. |
| Directory Permission Changed | Lists directories with permission changes. |
Saved Configurations
Save your current report configurations for future use. When you configure a report with specific settings and click the Save Configuration button, you can assign a custom name to that configuration.
All configurations you save appear when you select the Saved Configurations report type. This report auto-populates with all configurations you saved, displaying them with the names you assigned. This feature helps you reuse report settings without reconfiguring the same parameters.
Saved configurations connect with the Export and Save Options feature, allowing you to build a library of commonly used report settings.
Report Drill-Down
Reports provide interactive drill-down functionality specifically for users and objects (files and directories). When viewing report results, you can click on user names or object links to access more detailed information pages.
User Drill-Down
-
Click User Name Link
In any report displaying user information, click on the username link to navigate to a detailed page about that specific user. -
View Detailed User Information
The detailed page displays comprehensive activity logs, access patterns, and behavioral analytics for the selected user.
Object Drill-Down
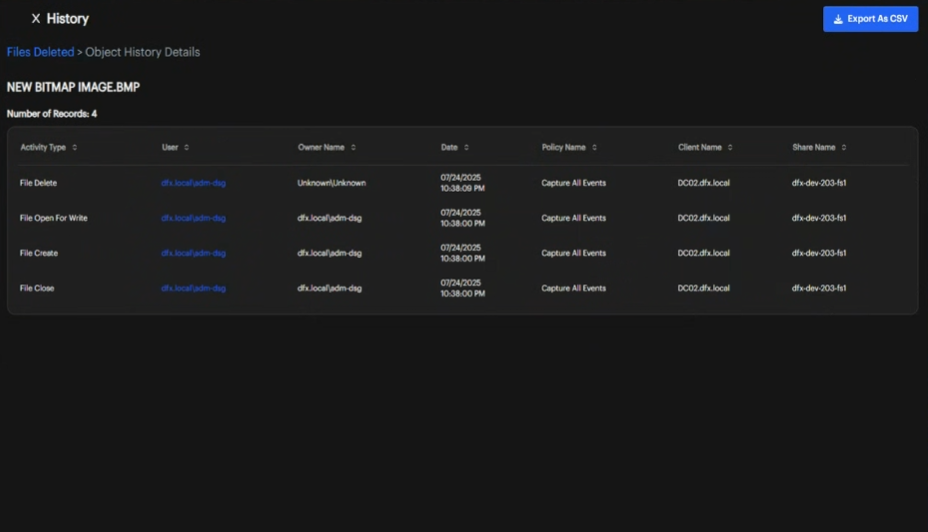
-
Click Object Link
In reports displaying files or directories, click on the object name link to navigate to its detailed page. -
View Detailed Object Information
The detailed page shows complete operation history, access logs, and permission changes for the selected file or directory.
Directory Permissions Details
When viewing permission-related reports, you can access detailed permission information for directories and files.
-
Click Permission Details
Click on permission entries in reports to view the detailed permissions page. -
View Permission Information
The detailed page displays:- User: The user whose permissions are being tracked
- Directory Name: The directory or file path
- Permissions Table: A comprehensive table showing:
- Attribute: The specific permission type (read, write, execute, delete, etc.)
- Previous: The permission status the user had before the change
- Current: The current permission status showing if the user still has the permission
-
Export Permission Data
Click Export as CSV to download the permission details for further analysis or compliance documentation.
The Previous and Current columns help you track permission changes over time, making it easy to identify when permissions were granted or revoked and understand the current access state.
Drill-down functionality is available for:
- Users: Click on username links to view detailed user activity
- Objects: Click on file or directory name links to view detailed object history
- Permissions: Click on permission entries to view detailed permission changes
Other report elements (such as dates, access types, or client names) do not have drill-down capabilities.
Full Log History
View the complete log history of files, users, and other entities. This provides forensic detail for investigations and compliance audits.
Use drill-down capabilities to investigate specific security events or user activities. This feature helps you navigate from summary data to forensic information for thorough analysis.