Threat Hunting Integrations
With our webhooks, you can forward both threat detection and threat hunting events to your security solution. Filters allow you to choose which events are sent to which third-party solution.
For example, you might forward:
- Threat detections to solution A
- Threat hunting events to solution B
- Both to solution C
The configuration shown below is an example for forwarding threat hunting events.
Through integration with your security stack, you can forward anomaly alerts directly to your SIEM or SOAR platform, enabling your Security Operation Center to respond faster and more efficiently. These alerts can enrich existing security incidents with file access context, correlate user behavior anomalies with broader threat intelligence, and trigger automated response workflows so you can react before the damage is done.
Setting Up Webhook Integration
Follow these steps to configure webhook integration for threat hunting alerts:
-
Navigate to Integrations
Click on Integrations in the Eyeglass menu.
-
Access Webhooks Section
Navigate to the Webhooks section. -
Add New Webhook
Click the blue + icon to add a new webhook.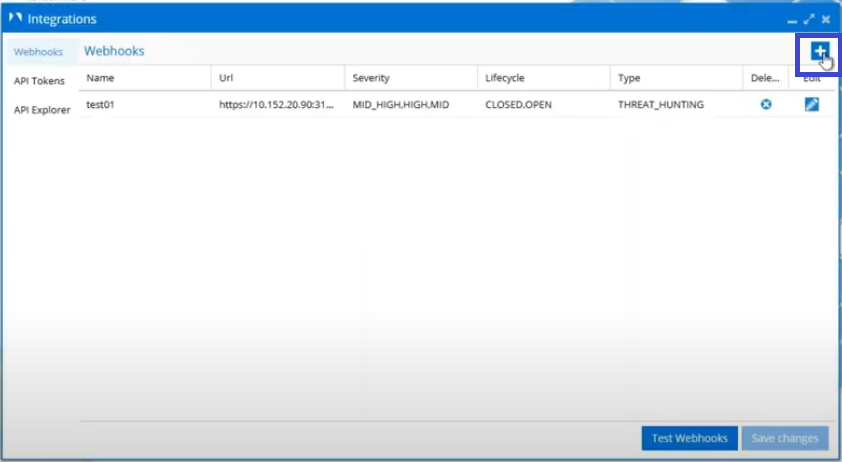
-
Fill in Webhook Information
Complete the following webhook configuration fields: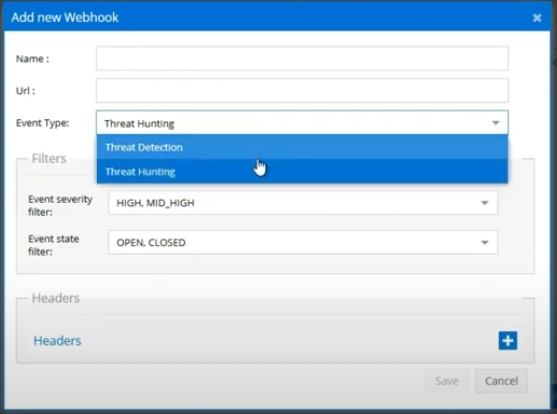
Field Description Options/Example Name Descriptive name for your webhook e.g., "SOC-SIEM-Integration" URL Target endpoint URL for webhook delivery e.g., "https://your-siem.company.com/webhook"Event Type Select Threat Hunting Threat Hunting Event Severity Filter Decide which events to forward/send over High, Mid-High, Mid, Mid-Low, Low Event State Filter Decide which states to forward/send over Open Headers Add any required HTTP headers for authentication or routing e.g., "Authorization: Bearer token123" -
Save Configuration
Click on Save and then Save Changes in the integrations UI to begin receiving threat hunting alerts at your specified endpoint.