Rapid7 InsightIDR
Overview
Superna Security Edition + Rapid7 InsightIDR enables real-time Zero Trust alert forwarding from your storage layer directly into InsightIDR. This integration provides native ingestion and automatic incident creation within Rapid7, helping SOC teams respond faster to ransomware and insider threats.
We’ll install and validate this integration at no charge so you can see value fast.
Next step: use Book a setup call at the top of this page.
What You Get
- Native InsightIDR ingestion via your on-prem Data Collector.
- Fully parsed JSON events preserving usernames, IPs, file paths, and severities.
- Critical incidents auto-created using Log Pattern Detection rules.
- Simple architecture—no middleware or cloud relay required.
Demo Video
How It Works
- Detect – Superna Data Security Edition identifies a threat event (e.g., ransomware, insider access).
- Translate – A lightweight Python Flask app on the Eyeglass VM converts the webhook payload into a syslog message format.
- Send – The app sends the message to your Rapid7 Data Collector (UDP port, e.g., 6675).
- Ingest – InsightIDR parses JSON key/value pairs and logs the event.
- Trigger – (Optional) Create a Log Pattern Detection Rule in InsightIDR to automatically generate incidents for CRITICAL events.
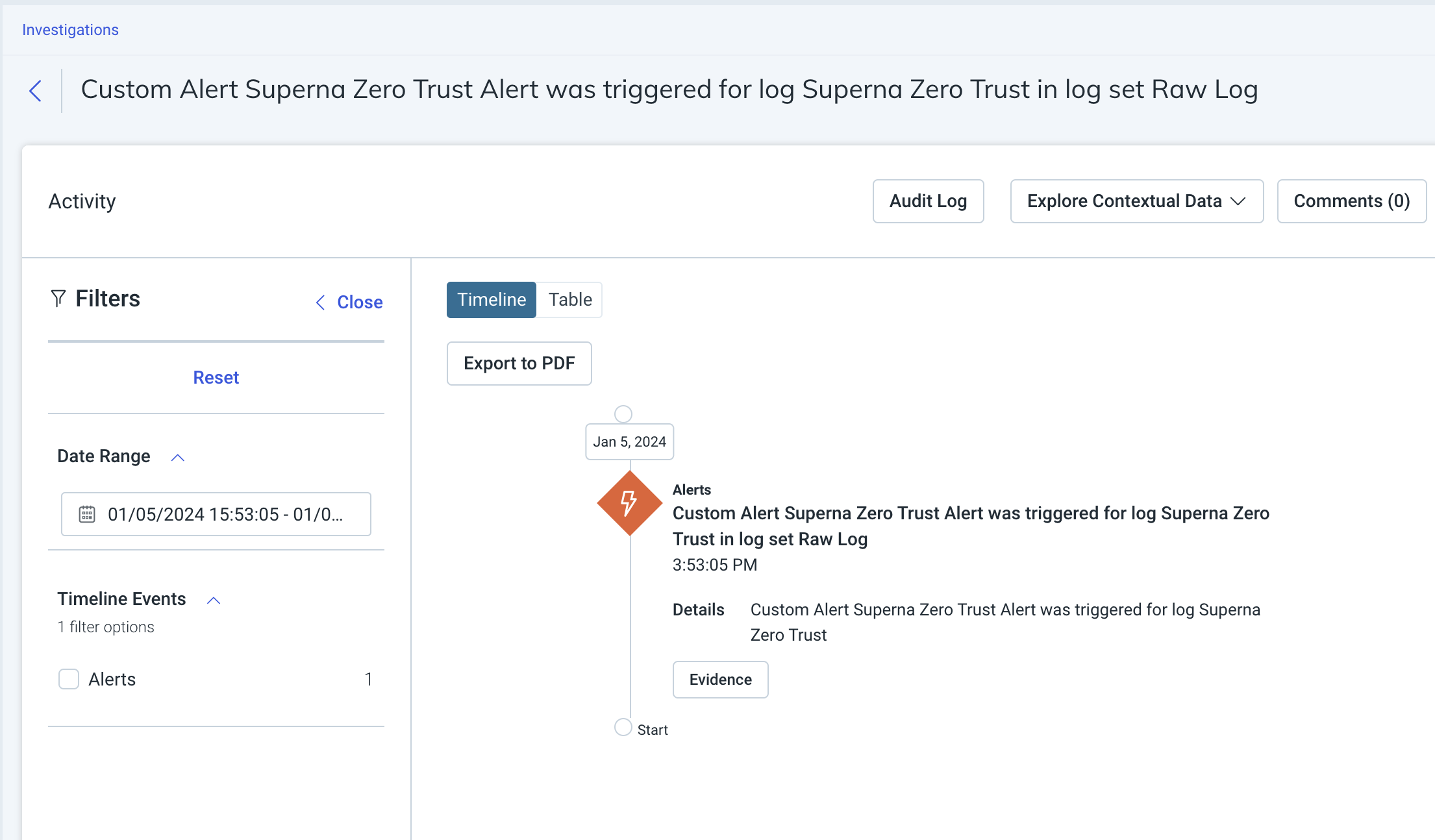
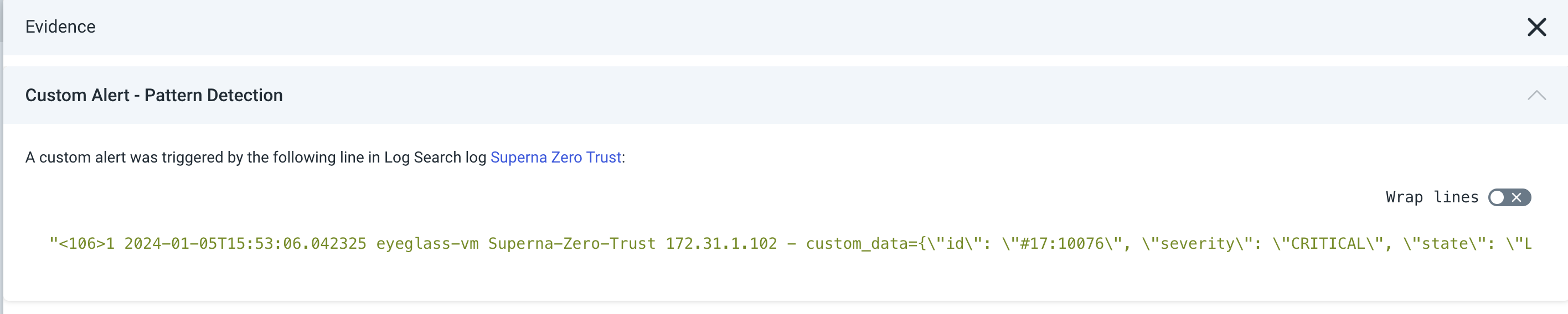
Architecture / Flow
Components
- Superna Security Edition – Emits Zero Trust webhooks on critical or major events.
- Integration Service – Python app on SCA (Eyeglass) VM formats and sends syslog data to InsightIDR Data Collector.
- Rapid7 InsightIDR – Ingests logs via Data Collector, applies parsing rules, and triggers detection rules.
FAQs
How does this connect to Rapid7 InsightIDR?
The integration sends JSON syslog messages over UDP (default port 6675) to your on-prem Rapid7 Data Collector configured with a Raw Logs Custom Event Type.
Can InsightIDR automatically create incidents?
Yes — you can configure a Log Pattern Detection Rule in InsightIDR to trigger incidents when CRITICAL severity events are received.
What events should I forward?
We recommend forwarding only Critical and Major severity alerts to minimize noise and focus on meaningful detections.