Threat Review
Data Security Essentials monitors your file systems and alerts you if it detects suspicious access behavior. Check the sections below to investigate threats, restore user access, or close alerts.
When Data Security Essentials detects suspicious behavior, it takes two key actions:
- It blocks the offending user based on the response settings in the policy triggers.
- It alerts the storage team if you configure notification settings for these policy triggers.
Access The Main UI To See Alerts
-
Open Data Security Essentials
Start the application to access its main interface. -
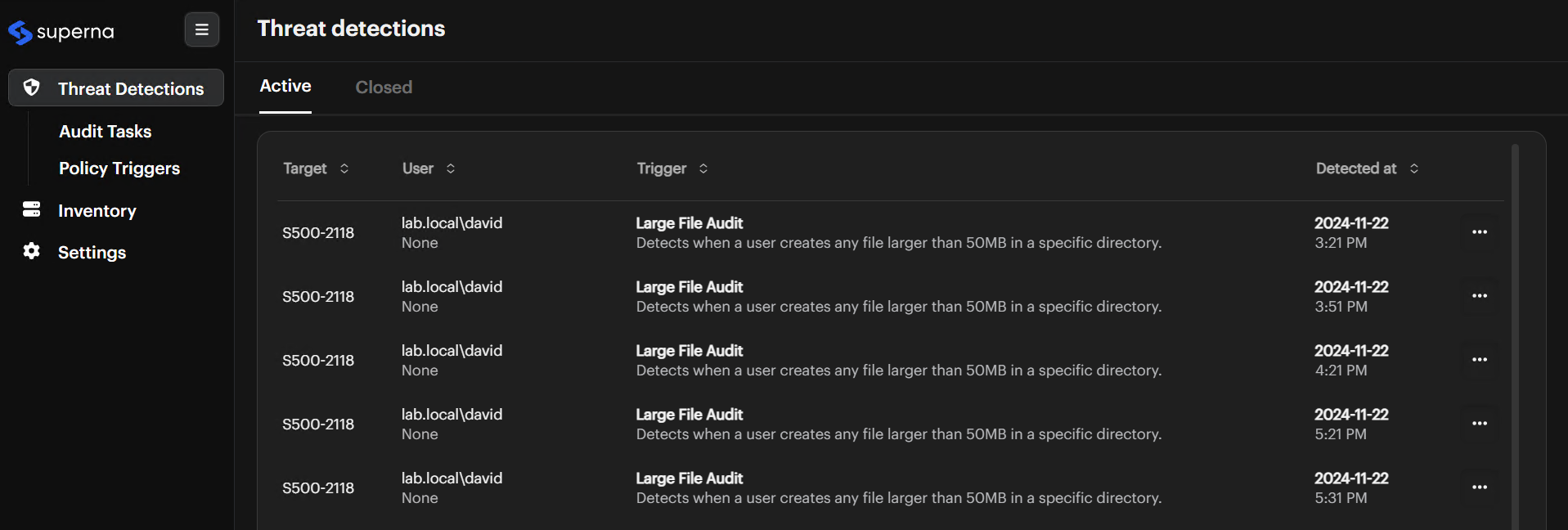
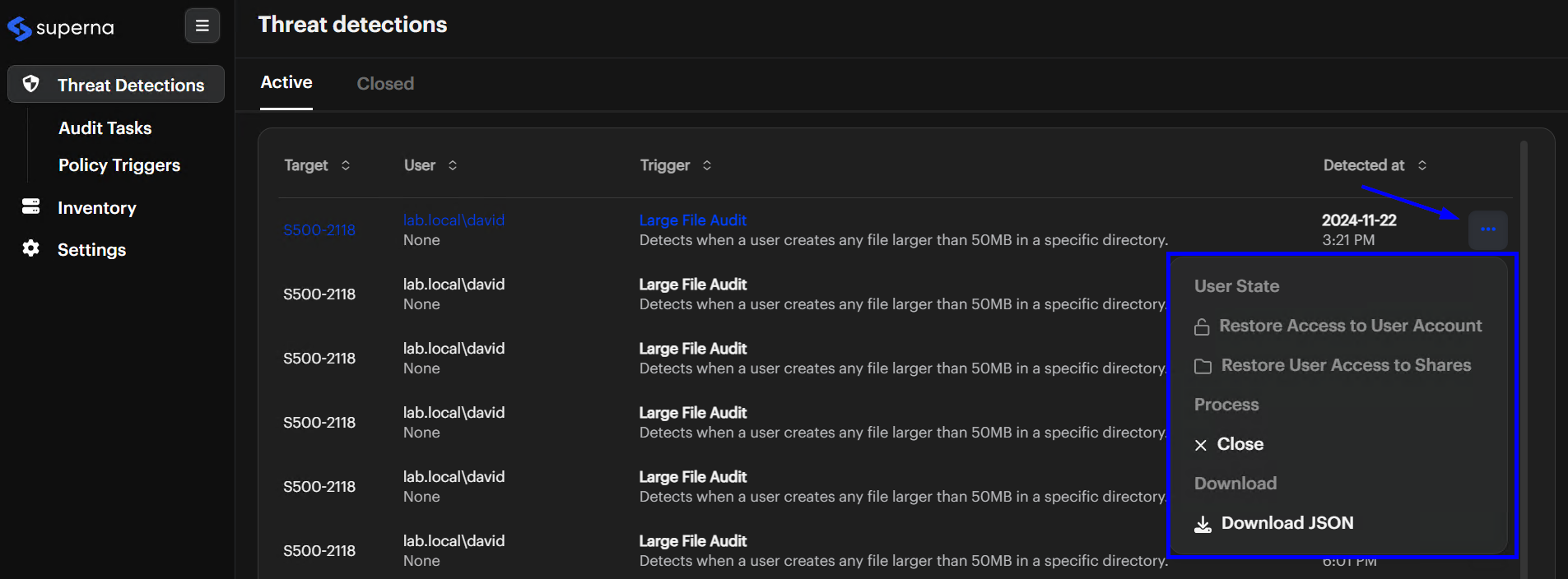
Select Threat Detections
Choose Threat Detections from the left navigation menu. You see active and closed alerts, plus forensic data detailing who accessed which files, when, and what actions occurred.
Review Ongoing Threats
-
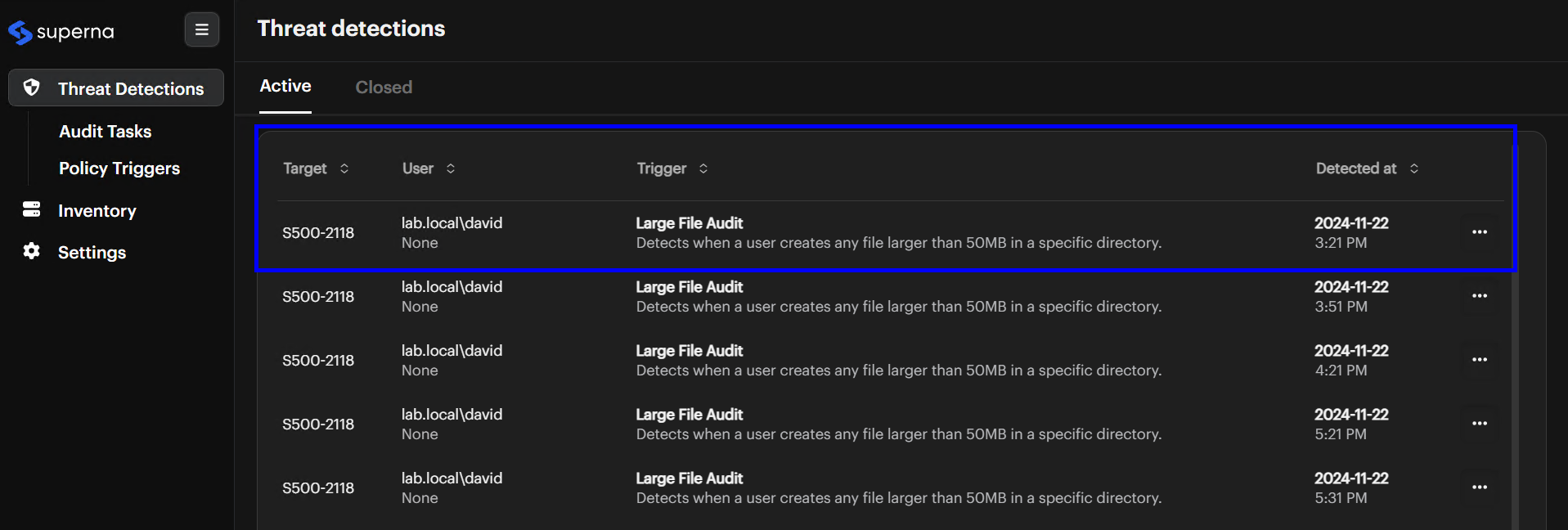
Go To The Active Tab
Click the Active tab to see a list of current threats. -
Check Key Columns
Look at the Target, User, Trigger, and Detected At columns to find the alert you want to investigate.
Investigate An Alert
Gather details about a specific alert.
-
Click The Alert
Select the alert you want to investigate. -
Review Alert Fields
Check the User, Response, Trigger, and Trigger Description. For example, the user might belab.local\david, the response might beNone, and the trigger could be Large File Audit. -
Check Detected At Timestamp
Note when the alert occurred. -
Locate Suspicious Files
In the table, examine the Device, Share, Path, and File Name columns.
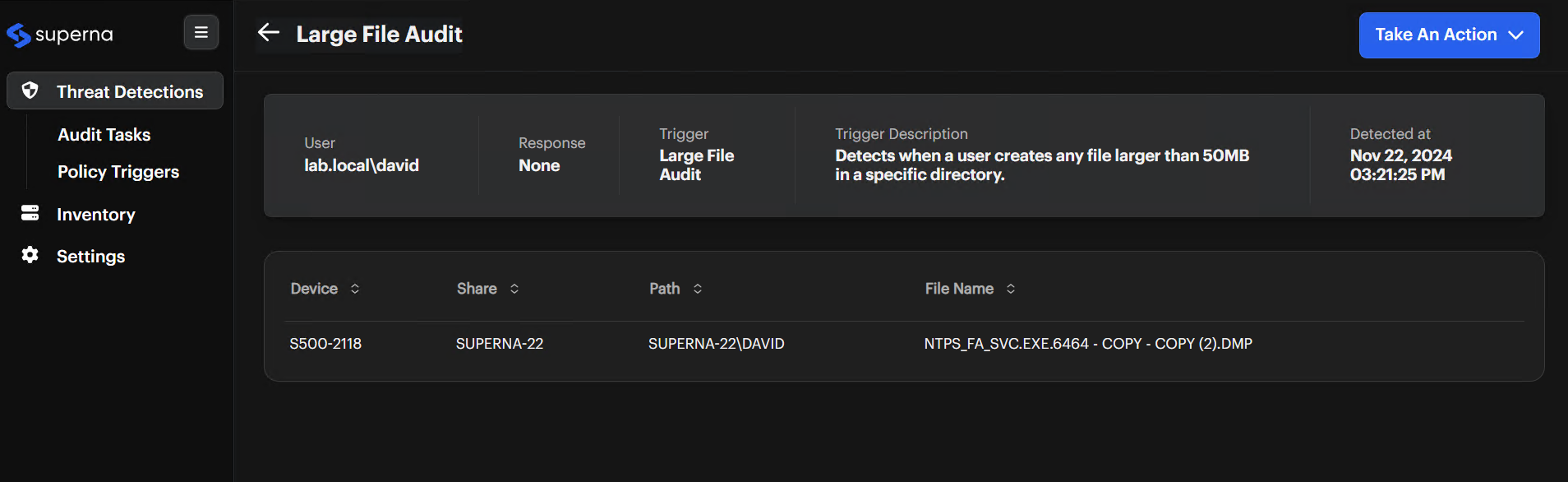
Take An Action
Respond to the alert.
-
Open Actions Menu
Click Take An Action (or the ellipsis ... on the Threat Detections list).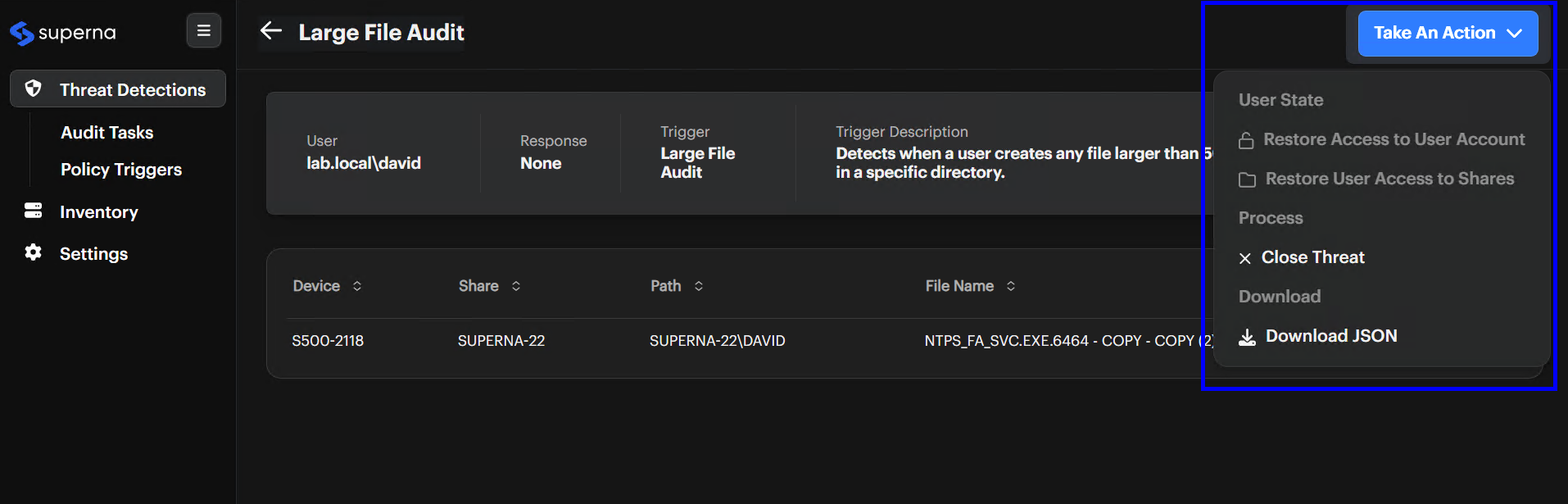
-
Choose An Option
- Restore Access to User Account or Restore User Access to Shares if the user is locked out.
- Close Threat if the threat is resolved.
- Download JSON for offline analysis.
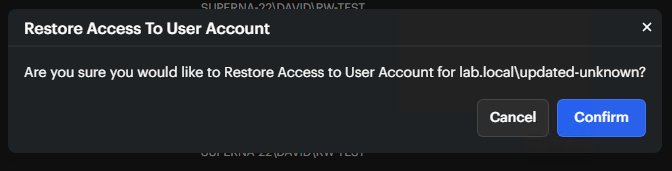
Restore User Access
Reinstate a user's access if they were locked out, disabled, or logged off by the trigger actions.
-
Identify The User State Check the Response field in the alert details. For ransomware threats, you might see Disabled Account or Logged Out.
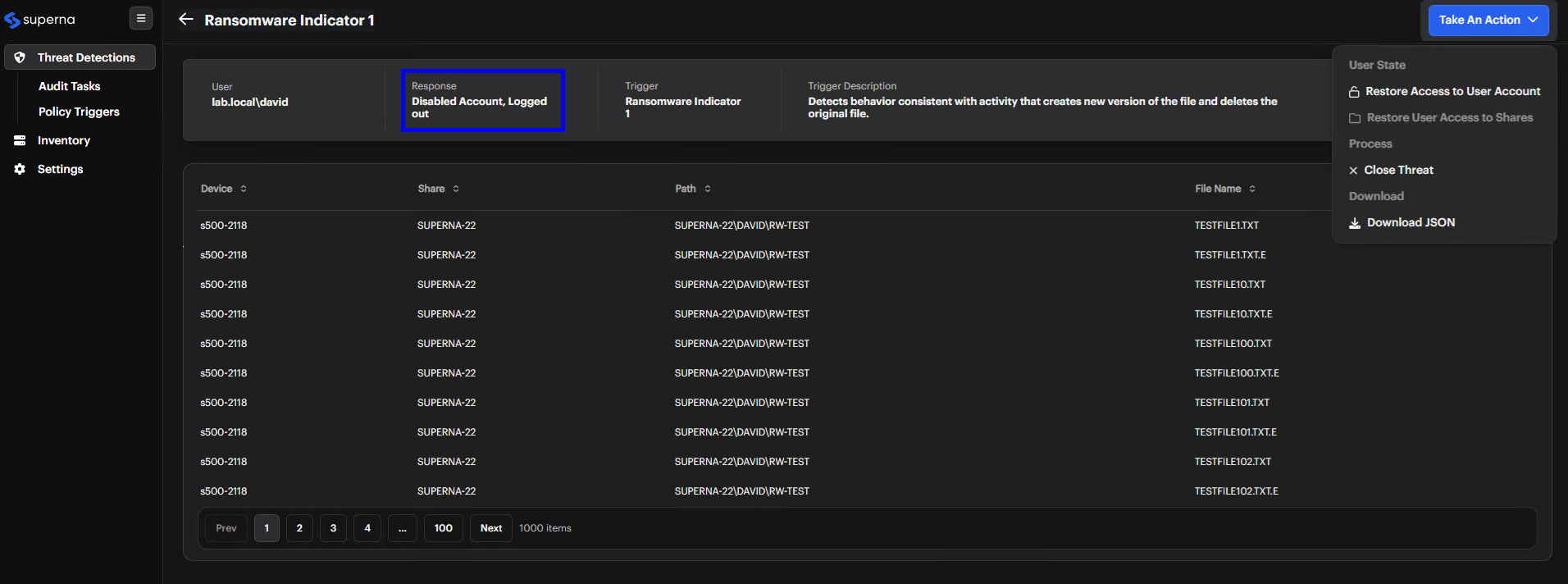
-
Open Actions Menu Click Take An Action. The actions menu appears on the right.
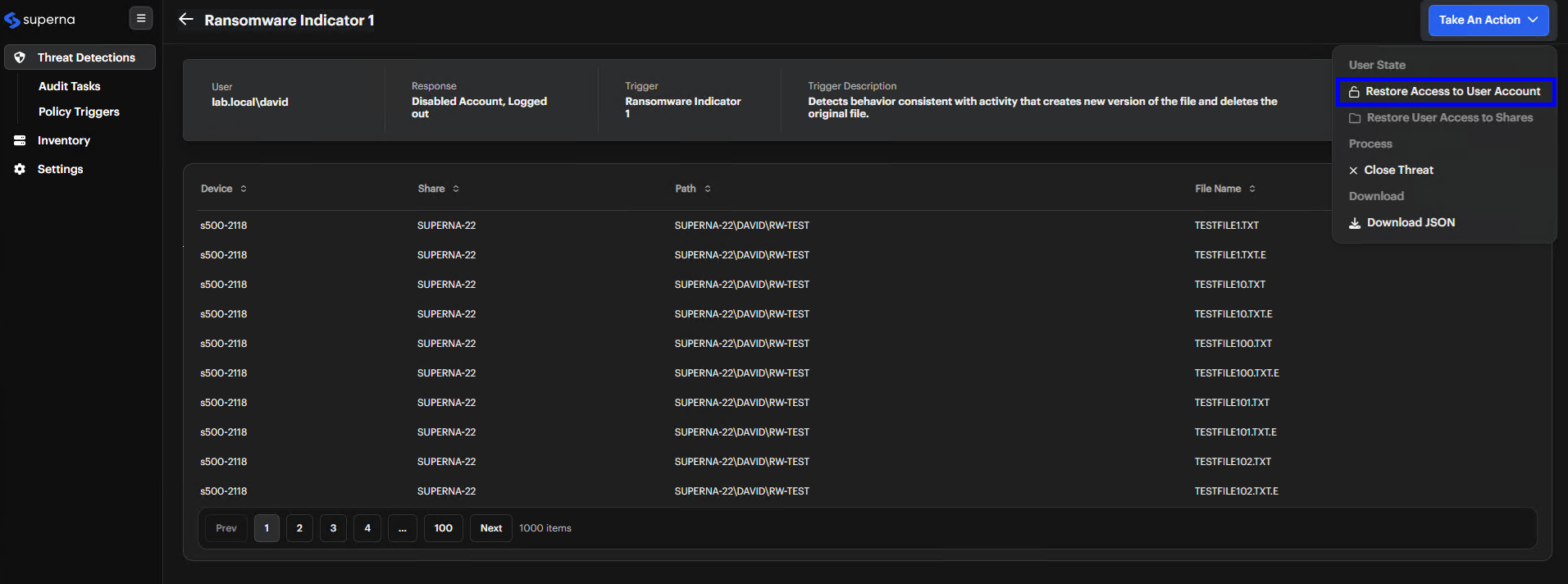
-
Confirm Restoration
- Restore Access To User Account: Appears when a user’s AD account is disabled. Click it to re-enable the account.
- Restore User Access To Shares: Appears when the user is locked out of shared resources. Click it to restore share access.
- Log Off Workstation: If a user is logged off, no restore option appears. The user must log in again.
When you select Restore Access To User Account, a confirmation dialog appears. Click Confirm to complete the action.