Security Guard
Introduction
The Security Guard feature is an automated self-test tool designed to simulate a ransomware attack on a cluster to validate that all security components function correctly. It ensures that Ransomware Defender effectively monitors, detects, and responds to suspicious user behavior and potential ransomware threats.
The system can run these simulations on a scheduled basis, typically once a day, or they can be initiated manually, on-demand.
Configure Security Guard
Requirements
Before you begin, ensure you have the following:
- A Security Guard share with auditing enabled.
- An Active Directory (AD) user with appropriate access.
Configuration Steps
-
Open the Ransomware Defender application
Launch Ransomware Defender, select the Security Guard tab, and scroll to the Job Settings section.
-
Select the network element and configure access
- VAST
- Qumulo
Select your VAST cluster from the list of available network elements. In the IP Address field, enter an IP from a protocols VIP pool.
noteUse a data interface IP when configuring the VAST system. The management IP does not provide access to the Security Guard share.
noteThis IP is used to map the SMB share during simulation. Update the value if the IP address changes.
Select your Qumulo cluster from the list of available network elements.
In the Data Access IP field, enter one of the following:
- A fixed IP address owned by the cluster, or
- A floating IP address
noteFloating IPs are commonly used for SMB/NFS access and may move between nodes. Update the field if the IP changes.
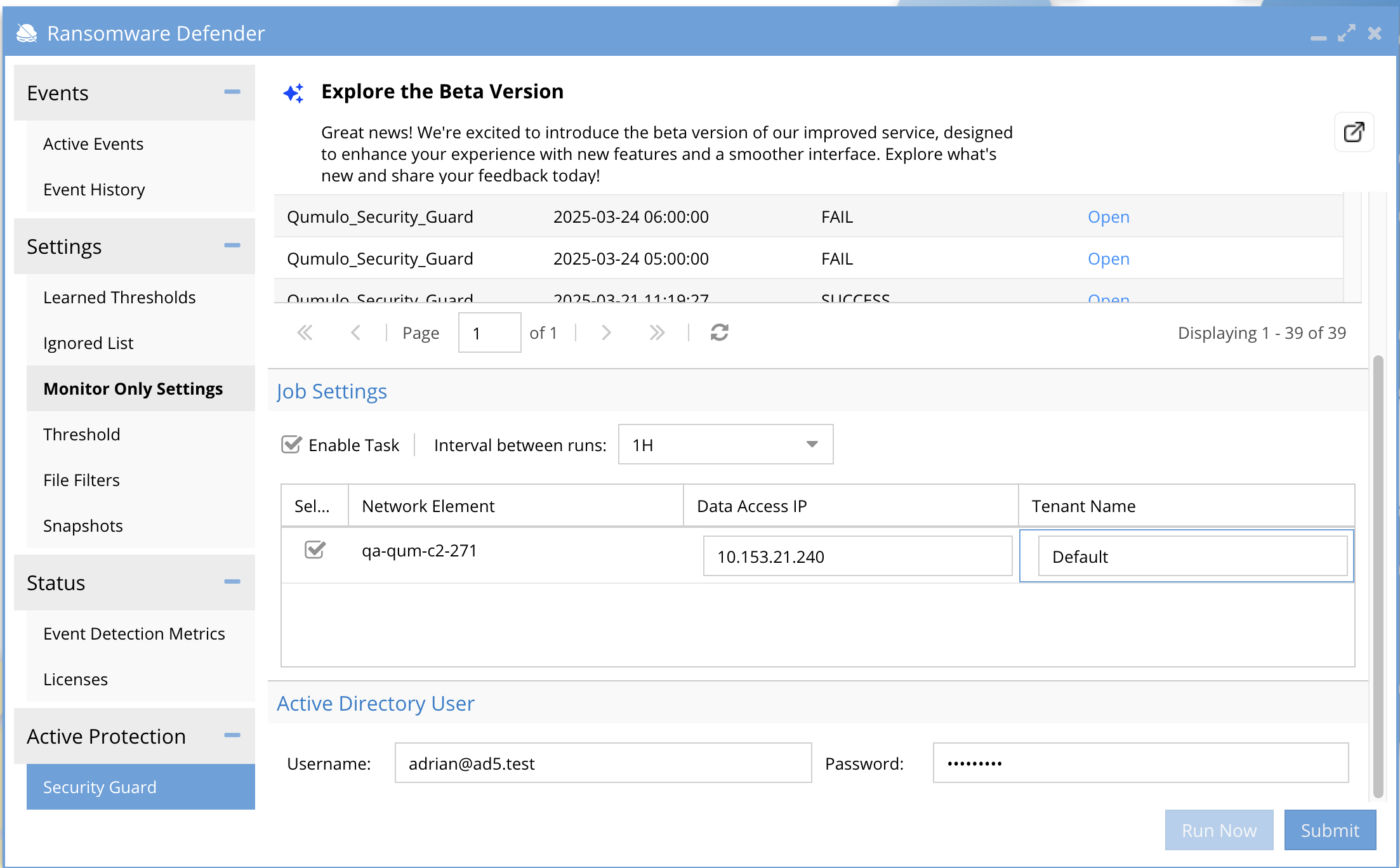
In the Tenant Name field,
- For multi-tenant environments, enter the name of the tenant where the Security Guard files will be copied.
- For single-tenant environments, enter the default tenant name.
-
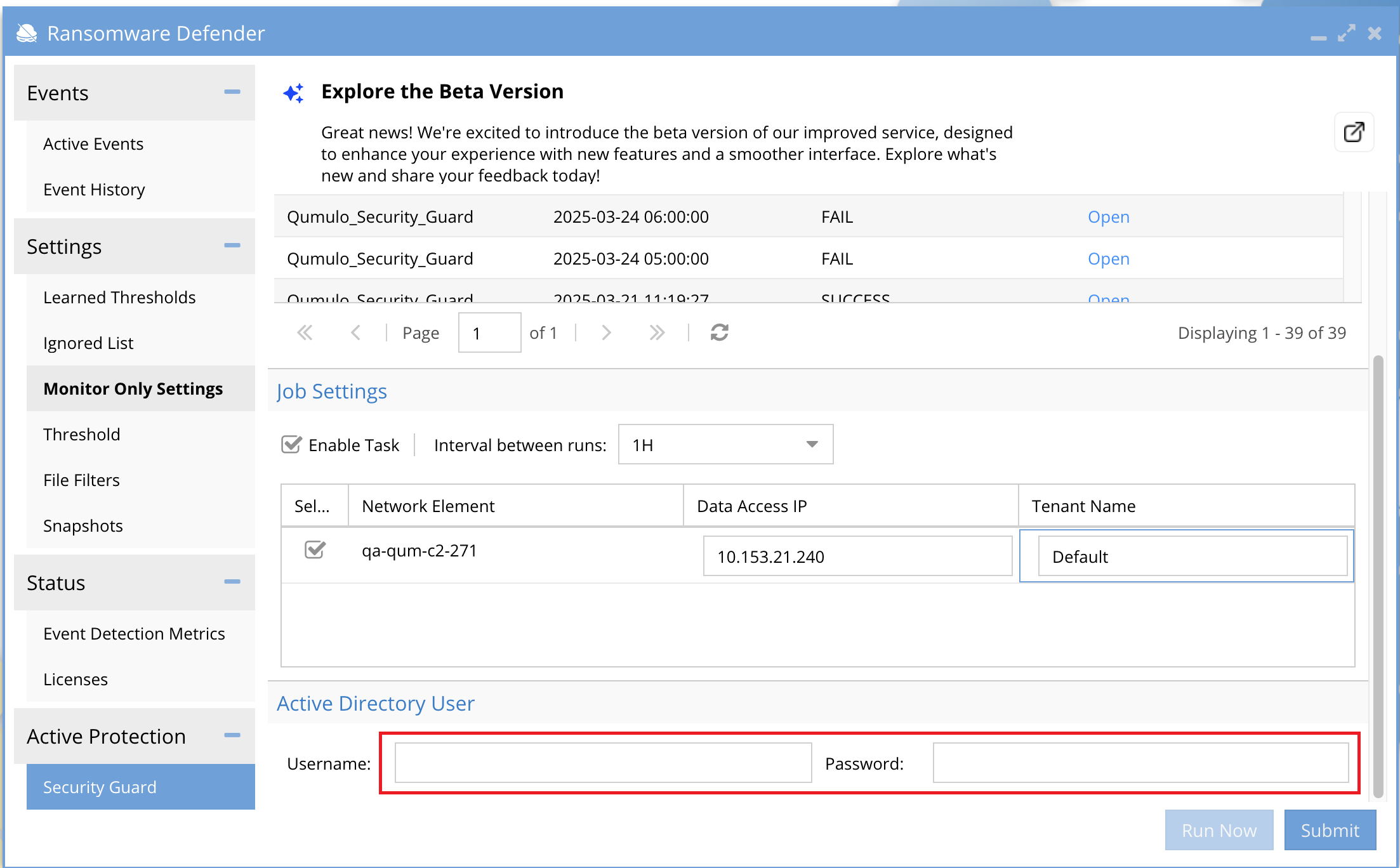
Configure the Active Directory user
In the Active Directory User section, type the username and password of the user who will trigger the simulation.
This user must have access to the Security Guard share.
-
Set the schedule and run the test
In the Interval field, define how often the simulation runs:
Use
Hfor hours orDfor days.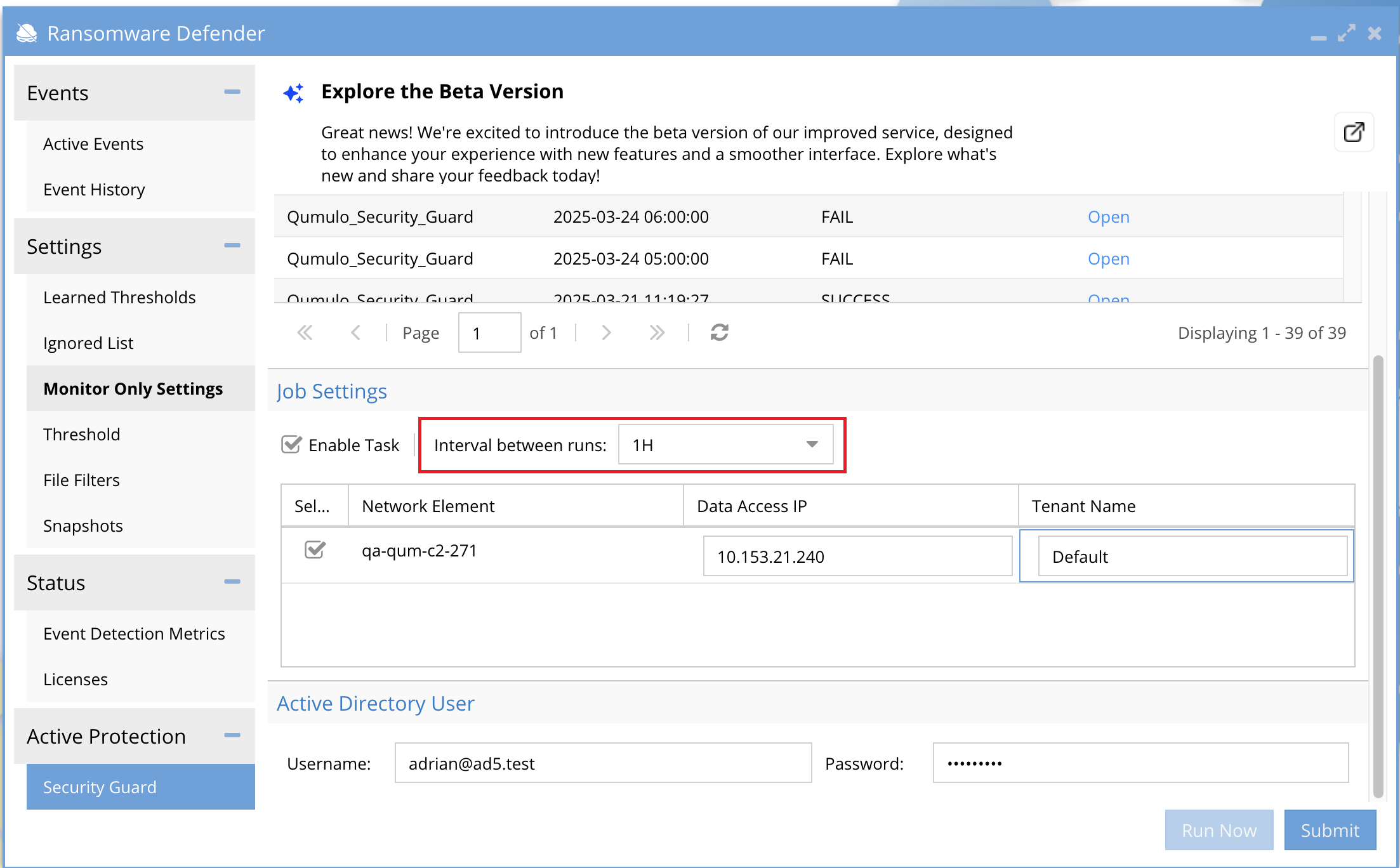
(Optional) To run the test immediately, select Run Now.
Select Submit to save and activate the job.
Manually Run Security Guard
To run a simulation outside of the configured schedule:
- Go to the Security Guard tab in the Ransomware Defender application.
- Scroll to the Job Settings section.
- Select Run Now to initiate the test immediately.
This action triggers a simulated ransomware attack and validates that alerting and response mechanisms are functioning as expected.