What’s New in Cyberstorage?
Would you like to receive notices about releases for Superna Cyberstorage?
We've created the What's New? feed to keep you up to date on releases and technical advisories. Subscribe using RSS or Atom.
What's New?
This release of Cyberstorage for VAST and Qumulo introduces expanded platform support, updated capabilities for Disaster Recovery and Data Security, and a set of fixes that address issues from previous versions.
Features
Active Auditor for Qumulo
Active Auditing is now supported on Qumulo, enabling enhanced visibility and proactive data protection. This includes support for Mass Delete and Custom Real-Time Audit Triggers:
-
Mass Delete Protection Trigger
A pre-built trigger designed to detect and alert on high-volume delete operations by users. This helps identify unusual behaviors such as mass deletions or high-rate copy/delete workflows that may impact cluster stability or signal malicious activity.
-
Custom Audit Triggers
Build powerful, real-time audit policies using flexible logic. Combine audit fields with AND/OR rules, set thresholds, and define time windows to monitor precisely the behavior that matters to your organization.
These features enhance your ability to monitor user activity, detect risky patterns, and respond to threats in real time.
IP-Based Security Guard for Qumulo
Security Guard for Qumulo now supports using the IP address associated with the Security Guard share by specifying a Data Access IP and Tenant Name. Previously, Security Guard used the fixed IP provided by the Qumulo Network Element (NE) to run simulations. With this update, if a Data Access IP is provided, Eyeglass will use that IP instead of the NE IP. Tenant name is required to create the share under the correct Tenant.
This allows Security Guard to run against the intended share IP used for mapping and simulating activity. If no Data Access IP is specified, the system will continue to use the NE IP as a fallback. This change enables support for both fixed and floating IP configurations when setting up Security Guard on Qumulo.
VIP Failover for VAST
Superna Disaster Recovery now supports failover at the VIP Pool level for VAST environments.
With this update, VIP Pools can now be selected as independent failover targets. This enables users to initiate failover for a specific VIP Pool and its associated protected paths without failing over the entire Tenant.
Seamless Failover now supports NFS, and is available as a supported option for VIP Pool failovers.
Replication Failover Enhancement (Multi-Tenancy Support) for Qumulo
During failover, Eyeglass previously used the single IP that was used to register the Qumulo cluster, funneling all replication traffic through one IP.
In 4.1.0:
-
If Floating IPs exist on the network(s) that are assigned to a Tenant and that Tenant has Replication Protocol enabled, Eyeglass assigns them to failed-over relationships in a round-robin fashion. This preserves load balancing.
-
If no Floating IPs are available, Eyeglass automatically falls back to the Persistent IPs, and then to the Cluster IP if needed.
No extra setup is required. As long as the Replication Protocol is enabled at the Tenant level, Eyeglass will use any available IPs on that network (floating or persistent) after failover.
Cluster Version Support
Qumulo
Added support for Qumulo version 7.3.2.1 and 7.4.1
Platform Support
Nutanix Support
Cyberstorage can now be deployed on Nutanix AHV. This adds support for running the appliance in environments using Nutanix as a hypervisor, alongside existing options.
SUSE Enterprise Support
Cyberstorage now supports SUSE Linux Enterprise Server (SLES) 15 SP6 as an operating system for the appliance.
An upgrade path is available for systems currently running openSUSE Leap 15.6, for customers who have or plan to license SLES. The SUSE Upgrade Guide included with this release provides detailed instructions.
Improvements
Updated Minimum Permissions
We've updated the Minimum Permissions required for VAST and Qumulo.
Existing customers upgrading from 4.0.0 to 4.1.0 need to add the following permissions:
Qumulo
For Qumulo, SSH into the cluster with the admin username and password. Run the following command to add the necessary permission:
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_FS_ATTRIBUTES_READ
For a full list of permissions, see the following articles:
In customer environments, we have observed that the following additional privilege may be required to successfully run config replication during Disaster Recovery (DR):
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_FILE_FULL_ACCESS
Be sure to verify this in your specific deployment scenario.
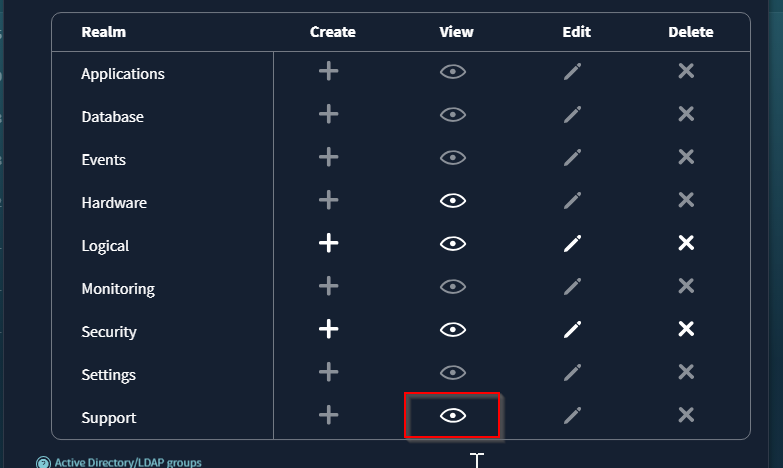
VAST
For VAST
- In the VAST Web UI, go to Administrators > Roles.
- Select the role used for Eyeglass (or create a new one if needed).
- Edit the role and add the View permission for the Support realm.
- Click Save.
For a full list of permissions, see the following articles:
Event Types More User Friendly
Event types in the Report Query Builder within Easy Auditor now display helpful descriptions directly next to each item in the dropdown menu. This update makes it easier for users to understand the purpose of each event type.
Threshold Defaults
The default threshold values in the Data Security web UI have been updated to align with the latest deployment recommendations from Support. These changes ensure that new deployments start with optimal, recommended settings out of the box.
Login/Logout Information for Easy Auditor
The Easy Auditor report now includes a "Status" column for LOGON and LOGOFF events, displaying whether each event was successful or failed. This enhancement provides clearer visibility into user login and logoff activity.
What's Fixed?
Fixes
Disaster Recovery
-
CYBER-152: Cluster Editing Status Issue
Cluster status now correctly updates after editing from the inventory. Previously, the status could remain stuck on "Updating" even after the operation was complete.
-
CYBER-155: AD User Authentication Issue
Active Directory (AD) users with spaces in their usernames can now be added to User Roles. Previously, these users could not be added successfully.
-
CYBER-156: AD Group Resolution Issue
Active Directory (AD) group resolution is now supported when using the Down-Level Logon Name (DLLn) format. Groups must be added using the
domain\group_nameformat. Group additions using this format are now processed successfully. -
CYBER-159: About/Contact Window Error for AD Users
After logging in with an Active Directory (AD) user, selecting About/Contact now works as expected. Previously, this action opened an empty window and prevented logout due to an uncaught type error.
-
DIS-1105/CYBER-207: Qumulo Multitenancy Audit Failure
A previous issue where Qumulo audit failures in multi-tenancy environments caused a Warning status in Eyeglass Configuration Replication has been resolved.
Data Security
-
CYBER-163: Security Guard Logs Copy Issue
Fixed the issue where the Copy to Clipboard button did not work for Security Guard logs when using only RWD licenses.
-
CYBER-164: SQL Database Settings Not Preserved After Upgrade
SQL Database settings are now properly retained after upgrading Eyeglass.
-
CYBER-165: VAST NFS v4 Folder Deletes and Renames in WDMFG
Folder delete and rename operations on NFS v4 mounts now appear under the Folders category in Where Did My Data Go. Previously, these actions were incorrectly listed under Files.
-
CYBER-170: TD11 Lockout Not Triggered in Advanced/Enforcement Mode
TD11 events now correctly trigger an automatic lockout when using "Enforcement + Critical On" or "Enforcement + Critical Off" modes. Previously, these events generated only a WARNING severity.
-
DS-1539: Query on root path is not returning any results
An issue where queries on the root path in VAST did not return any results has been resolved. Previously, a workaround was required by adjusting the path formatting (removing one /). This is no longer necessary.
-
CYBER-160: Missing Locked-Out Policies for VAST S3 Events
Ransomware Defender (RWD) events originating from VAST S3 now display correctly in the Shares section when events are locked out. Previously, this section appeared empty for such events.
-
DS-1725/CYBER-95: Restore job for NFS does not remove a row in Host Access that was added during lockout
Restore jobs for Qumulo NFS exports now correctly remove Host Access rules added during lockout. Previously, if an export was locked out without a specific IP defined for read access, the access restriction remained after restore.
-
DS-1720/CYBER-94: Lockout job tries to lock out access on an Export that was removed
Lockout jobs for Qumulo no longer attempt to apply access restrictions to exports that have been removed. Previously, the job would attempt to lock out access on deleted exports.
-
DS-969/CYBER-89: Monitor Only List - RSW events from added paths are received as warning/major/critical if the path is entered in the format 'tenant:/path/to/object'
Ransomware Defender no longer raises warning, major, or critical events for paths added to the Monitor Only List using the 'tenant:/path/to/object' format. Previously, events from these paths were incorrectly flagged despite being in Monitor Only mode.
-
DS-2131/CYBER-98: Qumulo-only environment the SMB user displayed as SID
In Qumulo-only environments, SMB users now display correctly by username in Active Events. Previously, the system would display the user's SID instead.
Release Notes
The release notes provide detailed information on fixes, known issues, and limitations introduced or identified in this version.
Refer to this document for visibility into the state of the release,
What's New in Docs?
Improvements
We have improved the organization and usability of documentation for VAST and Qumulo.
PowerScale and ECS content is now found in a section dedicated to Cyberstorage for Dell, and we've built the Multiplatform Cyberstorage documentation with the specific needs of your VAST and Qumulo environments in mind.
4.1.0 Feature Documentation
VIP Failover for VAST
Active Auditor for Qumulo
Documentation is now available for Active Auditor on Qumulo. It covers how to configure custom real-time audit triggers and mass delete detection.
Nutanix Support
A deployment guide is available for running Superna appliances on Nutanix AHV. The documentation includes configuration steps and prerequisites.
SUSE Upgrade Guide
An upgrade guide is available for moving from openSUSE Leap 15.6 to SUSE Linux Enterprise Server (SLES) 15 SP6. This is for customers who have or plan to license SLES.