Onboarding Mode
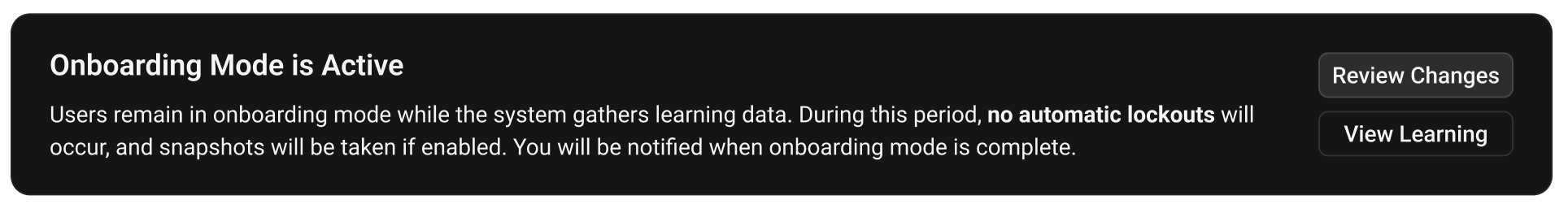
Onboarding Mode is a learning phase that activates when you first install Superna 5.x. During this period, the system monitors your environment's normal activity patterns to establish accurate baseline behavior. It restricts certain security features while learning, then guides you through a transition to full protection when you collect sufficient data.
How Onboarding Mode Works
 This provides configuration options for event expiry, snapshot settings, and other parameters.
This provides configuration options for event expiry, snapshot settings, and other parameters.
You can access and manage Onboarding Mode from the Settings section by selecting the Onboarding Mode tab.
-
Automatic Start
Onboarding Mode activates when you install Superna 5.x. -
Data Collection
The system records events and builds learned thresholds from your environment's activity patterns. -
Fixed Settings
During Onboarding Mode:- User lockouts remain disabled
- Auto-learning stays enabled
-
Adjustable Options
You can modify:- Event expiry times
- Snapshot settings
- Advanced severity levels
-
Completion Requirements
Stay in Onboarding Mode until detections drop below 2 per day over a 3-day period.infoThe system determines when you collect enough data to establish accurate thresholds.
-
Exit Notification
You receive this alert: "You're ready to exit Onboarding Mode. The system collected enough data to transition to severity-based settings with active user lockouts for enhanced security." -
Manual Exit Process
You must manually review and accept changes to exit.warningYou cannot reverse exiting Onboarding Mode. Once you transition to Regular Mode, the system applies your configured settings immediately.
-
Regular Mode Transition
After exit, you can enable lockouts and customize detection thresholds for your security needs. See Exiting Onboarding Mode for details about Regular Mode.
See Also
- Exiting Onboarding Mode - Steps to transition from Onboarding Mode to Regular Mode
- Onboarding Mode Settings - Configure event expiry, snapshots, and advanced options
- Dashboard - Monitor system status and event counts during onboarding
- Threat Detection Introduction - Understanding how detection works after onboarding
- Learned Thresholds - Manage detection thresholds created during onboarding