How Threat Detection Works
The Threat Detection feature continuously monitors devices in your environment for suspicious activities, automatically categorizes threats by severity, and provides comprehensive investigation tools. You can view active threats requiring immediate attention, investigate them using detailed analysis tools, take response actions like user lockouts, and review closed threats for audit purposes.
Security Response Process
The system operates through a continuous process:
- Device Monitoring (Automatic) - Superna 5.x continuously monitors devices configured in your Inventory for suspicious activities
- Threat Detection (Automatic) - The system identifies potential security threats based on user behavior patterns and file operations (see Detection Types)
- Severity Classification (Automatic) - Detected threats are categorized by severity levels (Critical, High, Medium, Low) with color-coded indicators
- Threat Display (Automatic) - Active threats appear as open threats with comprehensive details including source IP, affected user, target device, and threat categories
- Investigation (Manual) - Click any threat to investigate using detailed analysis tools showing affected files, accessible assets, and chronological activity logs
- Response Actions (Manual) - Take immediate action through user lockouts, access restoration, or threat closure
- Audit Trail (Automatic) - Closed threats remain available for compliance reporting and incident analysis
For detailed step-by-step procedures on investigating and responding to threats, see Response Procedures.
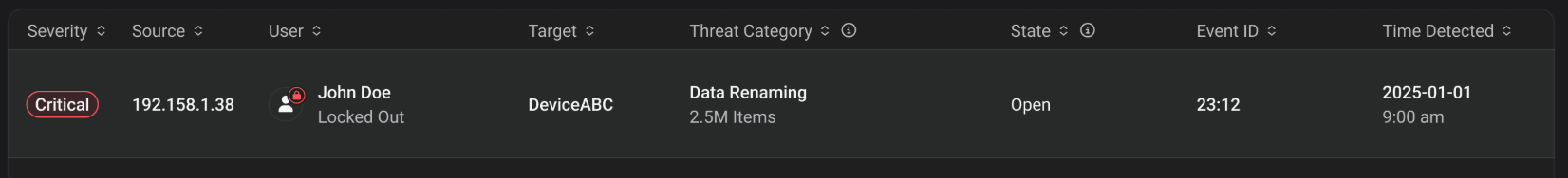
Understanding the Threat List
The threat detection interface displays comprehensive information about each detected threat:
Threat Severity Levels
| Severity | Color | Response Time (Recommended) | Description (Optional) |
|---|---|---|---|
| Critical | Red | Immediate | Immediate attention recommended for unusual activity patterns |
| High | Orange | Within 1 hour | Review within 1 hour for significant activity changes |
| Medium | Yellow | Within 24 hours | Address within 24 hours for moderate activity variations |
| Low | Blue | As convenient | Review during regular maintenance for minor activity changes |
Threat Information Columns
| Column | Description | Example |
|---|---|---|
| Source | IP address origin of suspicious activity | xx.150.xxx.64 |
| User | Account associated with the threat | AD\username |
| Target | Monitored device from Inventory | qumulo-109 |
| Threat Category | Classification and affected item count | Suspicious Extension (99 items) |
| State | Current processing status | Open, In Progress, Closed |
| Time Detected | Discovery timestamp | Jun 18, 25 at 4:48 pm |
| Event ID | Unique tracking identifier | 30 |
Click Reload Data to update the threat list with the latest information from your environment.
Detection Types
Superna 5.x identifies various threat categories, from ransomware to data loss prevention. For a complete list of detection types and their descriptions, see the Reference.
Open Threats
The default view displays unresolved threats. Each entry shows event details and available actions.
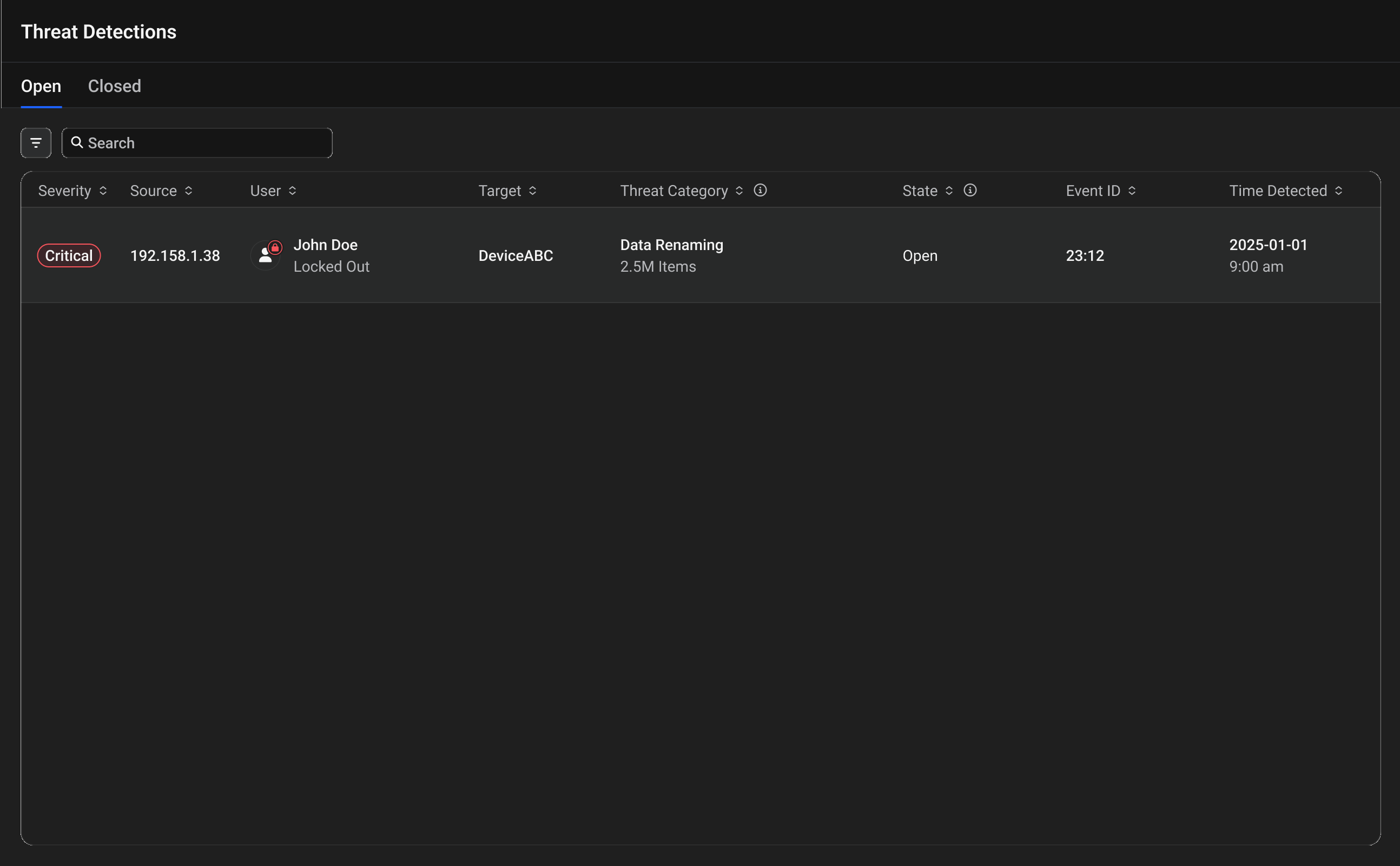
Viewing Threat Details
-
Click Any Threat
Click a threat entry in the list to open the threat details sidebar panel on the right side of the screen. -
Review Threat Information
The sidebar displays comprehensive threat details:- User Status - Current access state (for example, "Access Restored")
- Threat Categories - Detailed descriptions of detected threats
- Affected Devices - Number of impacted devices
- Items Affected - Count of affected files
- Device Details - Specific device information and type
- Recovery Summary - Percentage and count of unrecoverable items
- Details Section - Complete threat information including severity, IP address, timestamps, and event ID
-
Choose Your Response
At the bottom of the sidebar, you find two action buttons:- Investigate - Opens the detailed investigation interface with three analysis tabs
- Take an Action - Provides immediate response options (Restore User Access or Close Threat)
For detailed guidance on using these options, see the Response Procedures guide.
Closed Threats
Select the Closed tab to review resolved threats for compliance and learning purposes. All closed threats can be seen here. Click any entry to review:
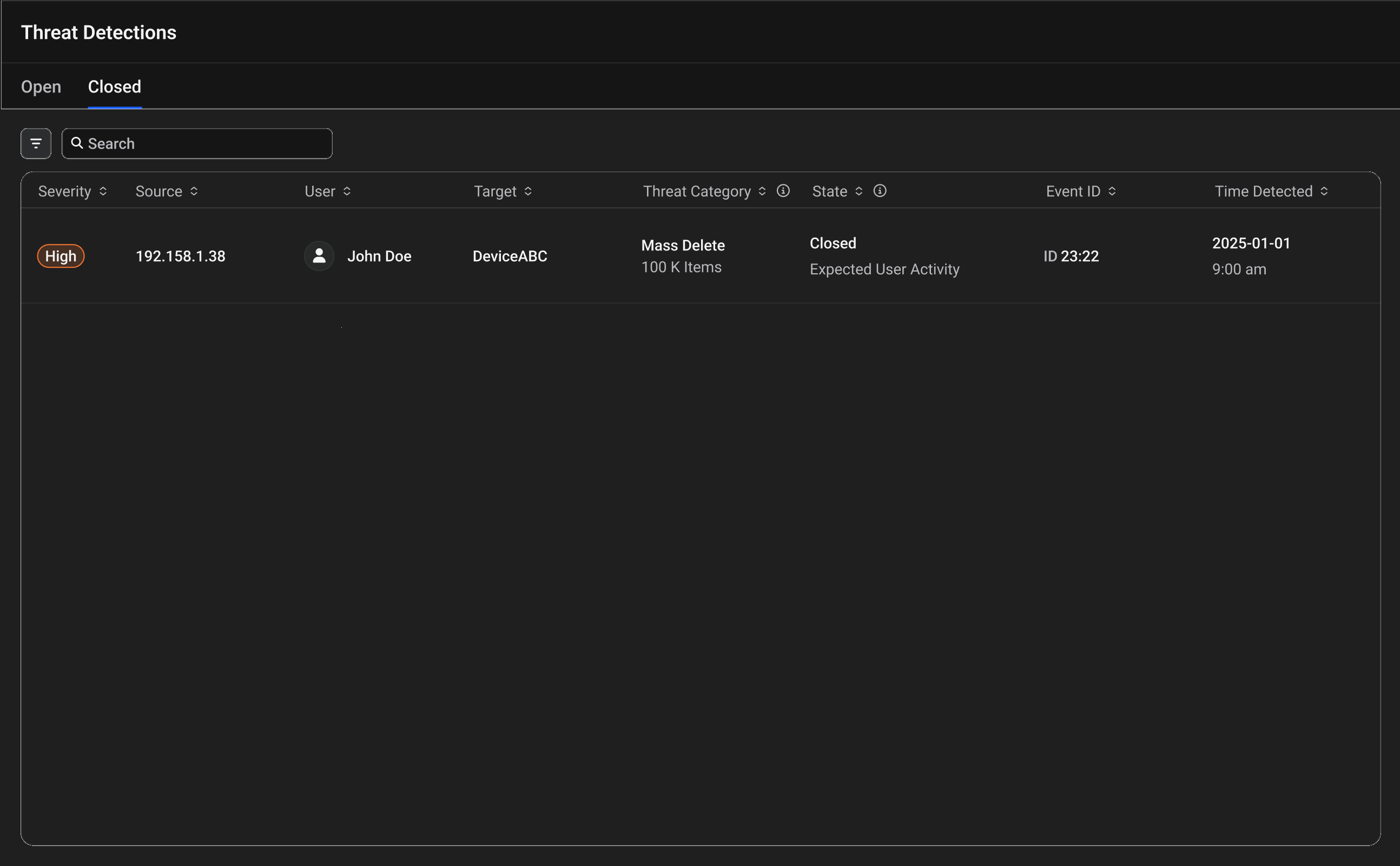
Viewing Closed Threat Details
-
Access Closed Threats
Navigate to the Threat Detection page and click on the Closed tab. -
View Closed Threat List
The page displays all closed threats with their original severity indicators:- Red - Critical severity
- Orange - High severity
- Yellow - Medium severity
- Blue - Low severity
-
Open the Closed Threat Details Sidebar
Click any closed threat in the list to open a detailed sidebar panel on the right side of the screen.
- User Status - Final access state (for example, "Access Restored" or "Access Locked")
- Threat Categories - Detailed descriptions of the original detected threats
- Affected Devices - Number of impacted devices
- Items Affected - Count of affected files
- Device Details - Specific device information and type
- Recovery Summary - Percentage and count of unrecoverable items
- Resolution Information - How the threat was closed and by whom
- Details Section - Complete threat information including:
- Original severity level
- Source IP address
- Target device
- Items Affected count
- Threat Category types
- Final State (Closed)
- Time Detected
- Time Closed
- Event ID
- Closing reason and comments
One action button is available at the bottom:
- Investigate - Opens the detailed investigation interface for review purposes
Investigating Closed Threats
When you click the Investigate button from the closed threat sidebar panel, the system takes you to a detailed investigation interface. This interface provides the same three tabs as open threats but for review purposes only:
- Items Affected - View historical file information, threat types, and affected items (no action buttons available)
- Assets Affected - Review the user's accessible resources at the time of the threat
- Activity Log - Access the complete chronological timeline of all events and actions taken
You can view all threat information and add comments, but cannot execute response actions like lockout, restore, or close since the threat is no longer active.
Searching and Filtering
Find specific threats using search and filtering capabilities:
How to Search
-
Access Search Bar
Use the search bar above the threats list. -
Enter Terms
Type any value (username, IP address, threat type). -
View Results
Results update automatically as you type.
How to Filter
-
Open Filters
Click the filter icon next to the search bar. -
Select Options
Choose from these categories:- Severity: Critical, High, Medium, or Low
- Threat Category: Specific threat types (see Detection Types)
- User: Specific users
- Target: Affected devices
-
Manage Active Filters
After applying filters:- View Active Filters: Active filters appear as tags at the top
- Check Count: Counter shows applied filters (e.g., "+2")
- Reset Filters: Click "Reset" to clear all filters
See Also
- Dashboard - Monitor active threats and system health
- Response Procedures - Learn how to respond to detected threats
- Jobs - View threat response and lockout jobs