Business Overwatch Tasks
What are Business Overwatch Tasks?
Data Security Essentials Business Overwatch Tasks (BOTs) are configured to run regularly against the Data Security Essentials database to detect users’ unexpected behavior.
For example, BOTs can warn administrators when a user downloads hundreds of files or gains access to secure or sensitive information; they can also warn of hacking attacks when a user deletes important files, etc. When a BOT runs, it searches the database for a specified user activity and notifies administrators accordingly via email.
For BOTs to function properly, a Data Security Audit policy must exist that monitors your NAS Device and is configured to store users’ activity into the database.
How to access?
To access Business Overwatch Tasks configuration on the Start menu, navigate to Programs > Superna Data Security Essentials > Data Security Essentials BOT Configuration.
Defining or Editing a BOT
A BOT has the following main parameters:
- Definition
- Schedule
- Actions
- Notifications
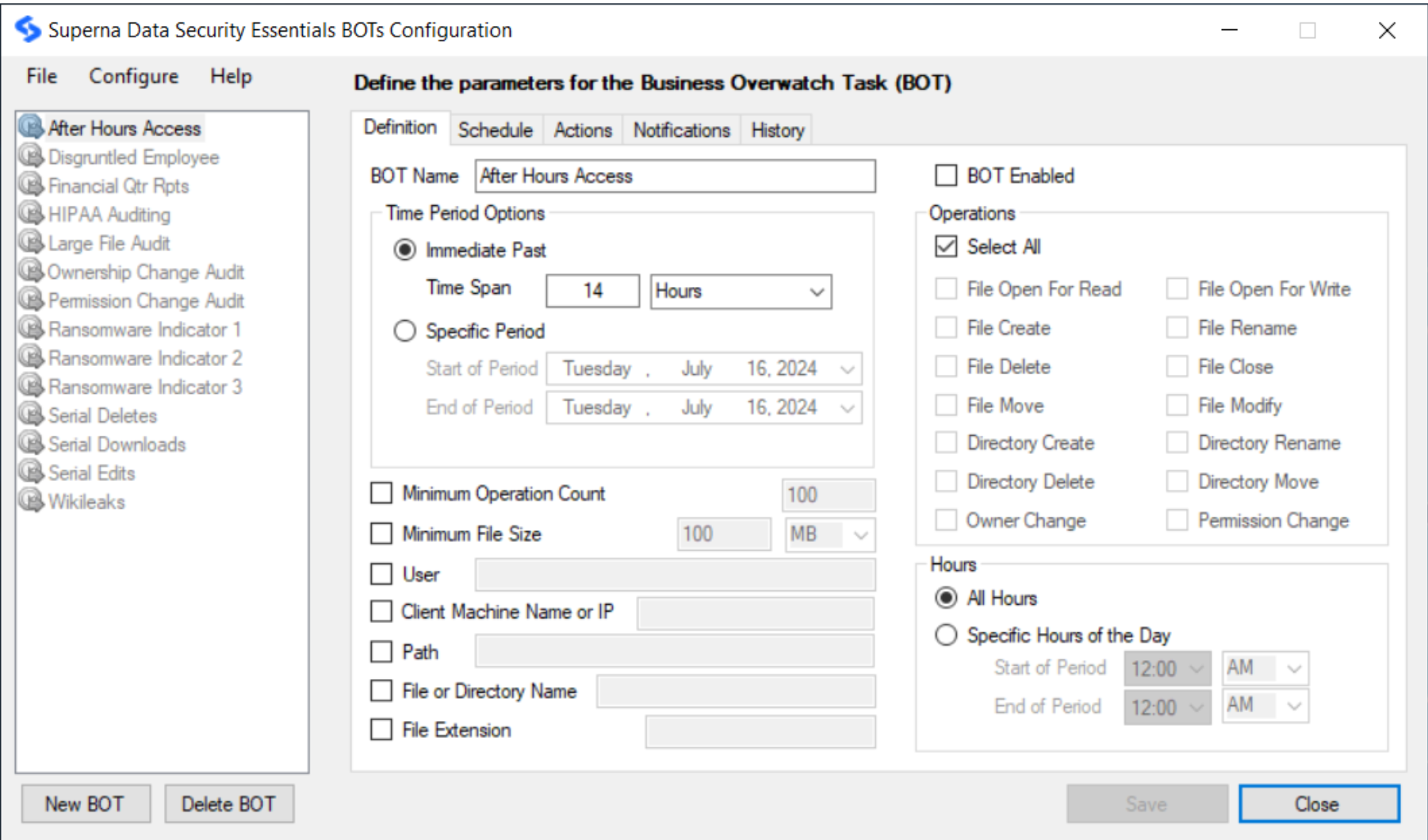
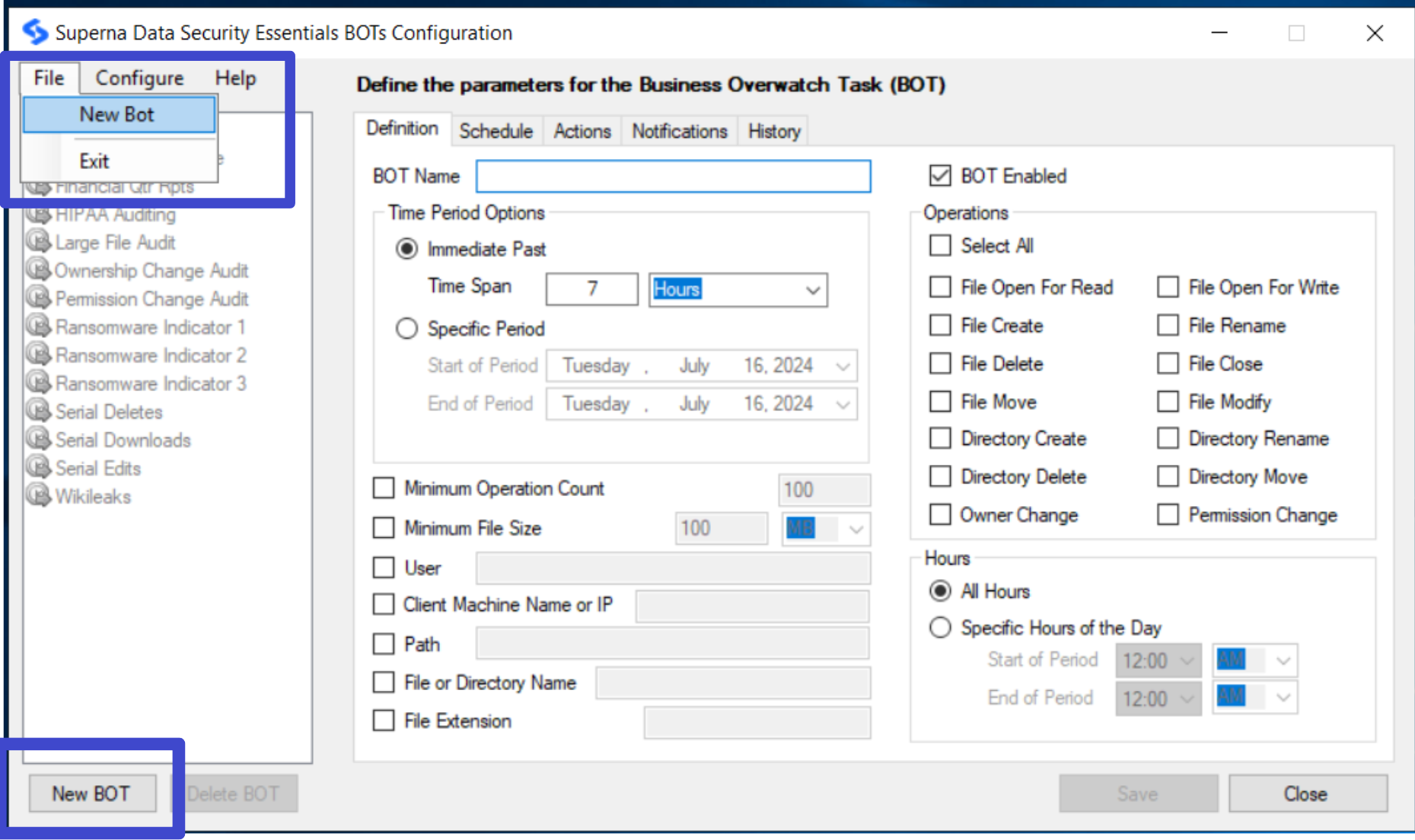
To define a new BOT or edit an existing one, please perform the following steps:
-
Access BOT Configuration
- Access Data Security Essentials BOT Configuration.
- Click the New BOT button OR File -> New BOT or select an existing BOT to edit from the list on the left panel.
-
Define BOT and Set Scanning Period
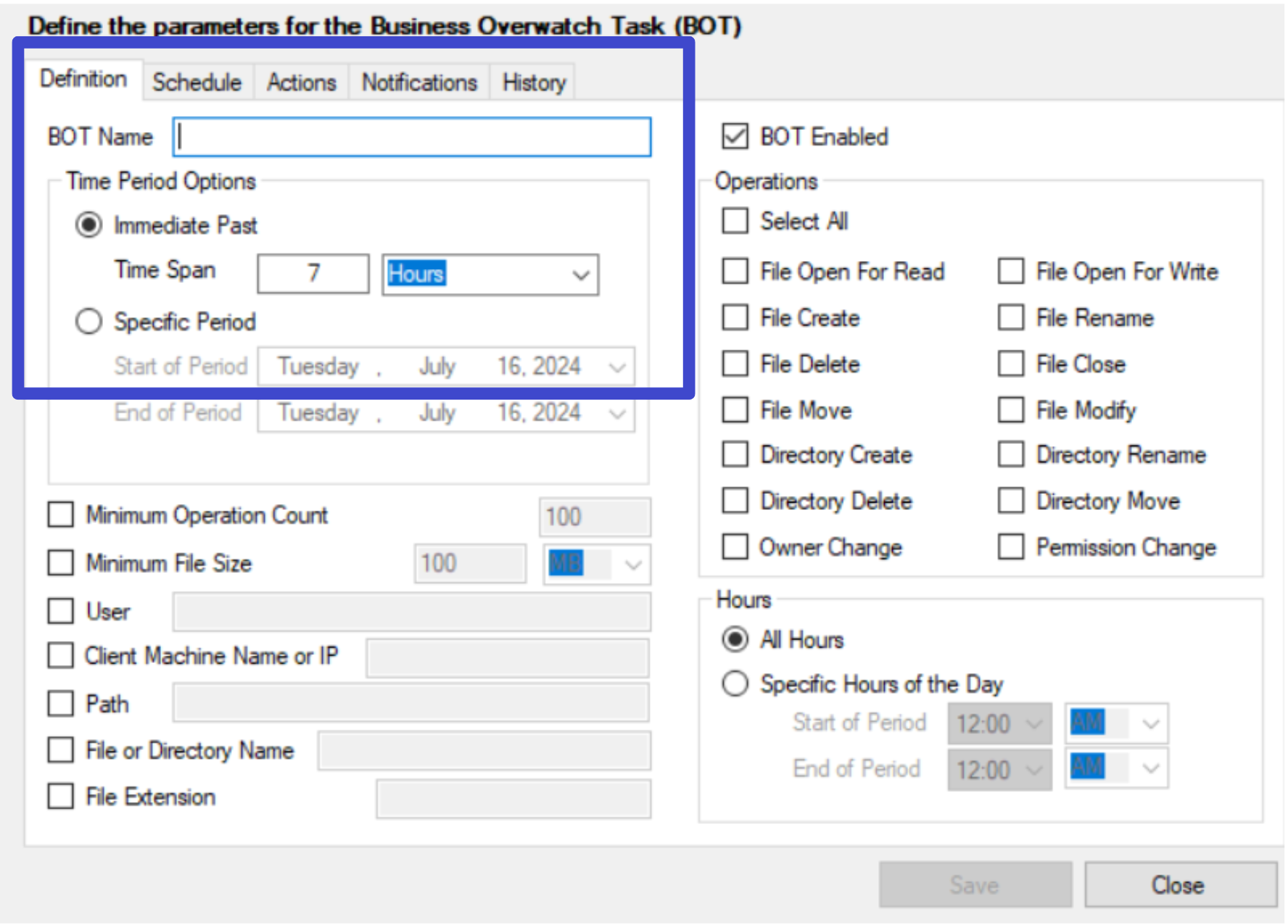
- On the Definition tab, specify the BOT name and use the Time Period Options to set the scanning period.
 info
infoSet the Time Period to ‘Immediate Past’ if you wish to notify the user of all the matching operations that occurred in a past period. Set the Time Period to ‘Specific Period’ if you wish to notify the user of all the matching operations that occurred within a specific time period, ignoring any operations that occurred at any other time.
-
Select Operations to Monitor
- Use the Operations section to check the operations you want the BOT to monitor. You can either check all operations or select individual operations to monitor. You can also enable/disable the BOT by checking/unchecking the Enabled checkbox. A disabled BOT will not send notification emails or generate history.
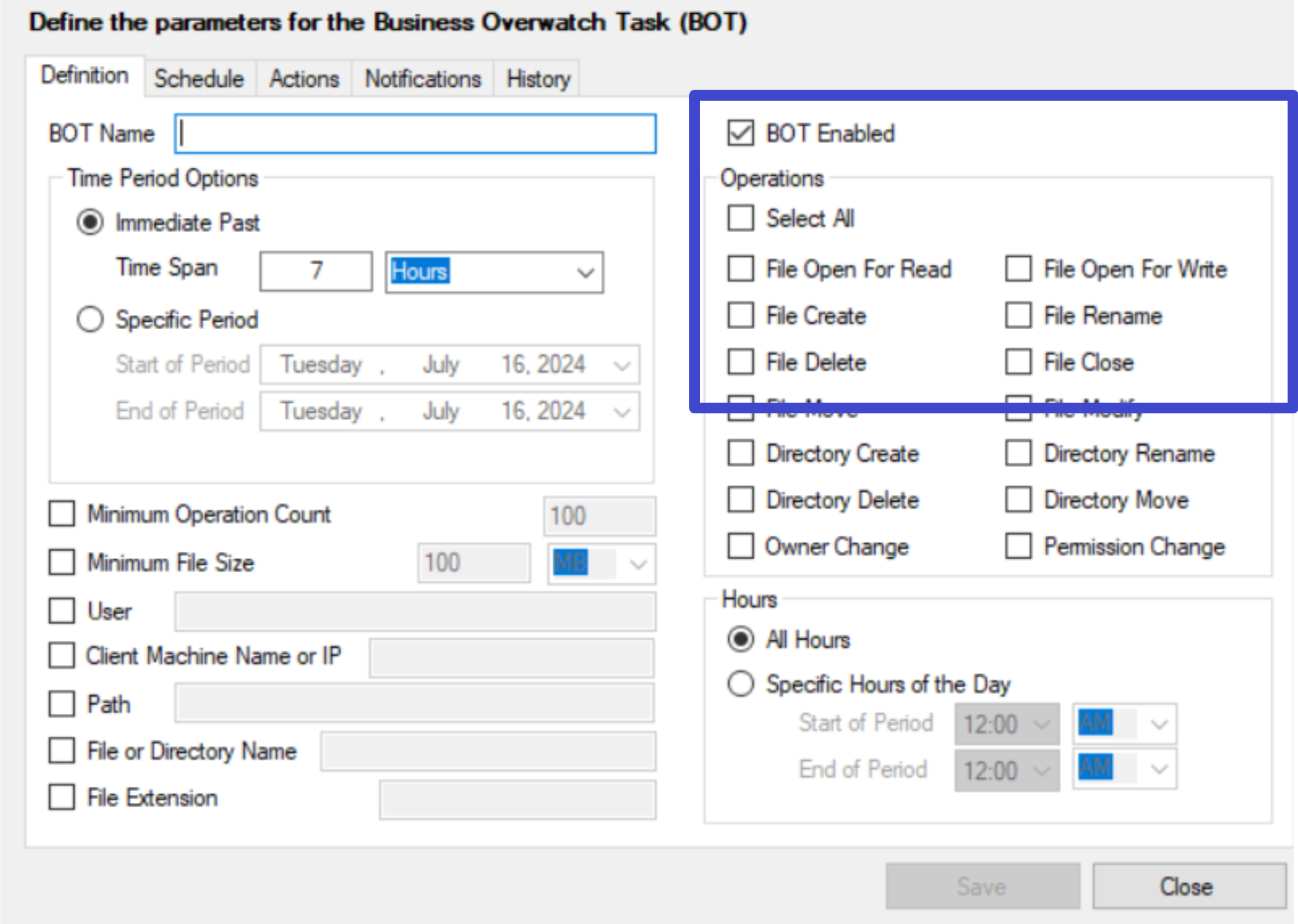
-
Specify Scanning Time
- Use the Hours section to specify the exact scanning time.
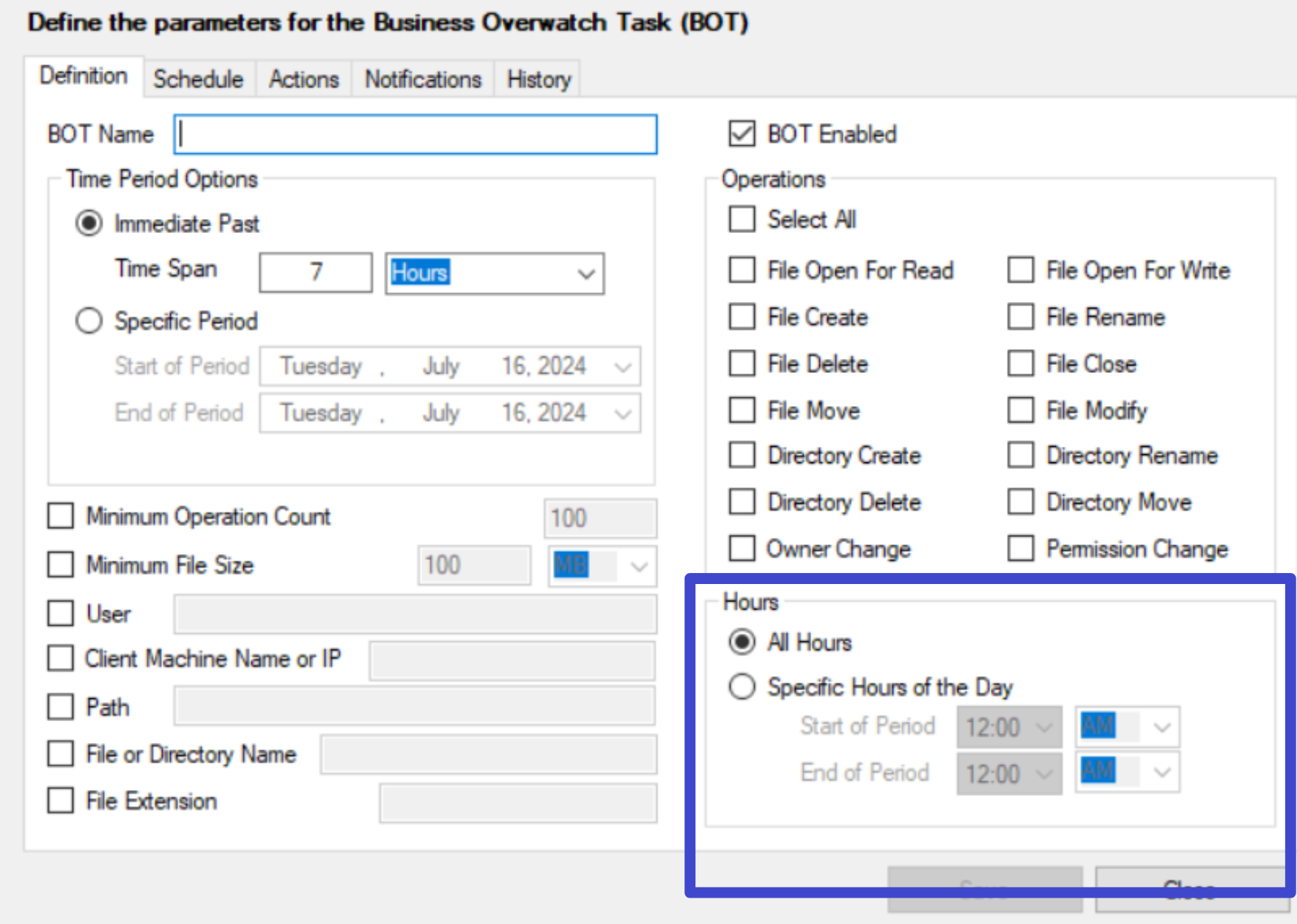
-
Set Additional Criteria
- You can specify additional criteria for other operations details such as file extensions, the user who performed the operation, etc.
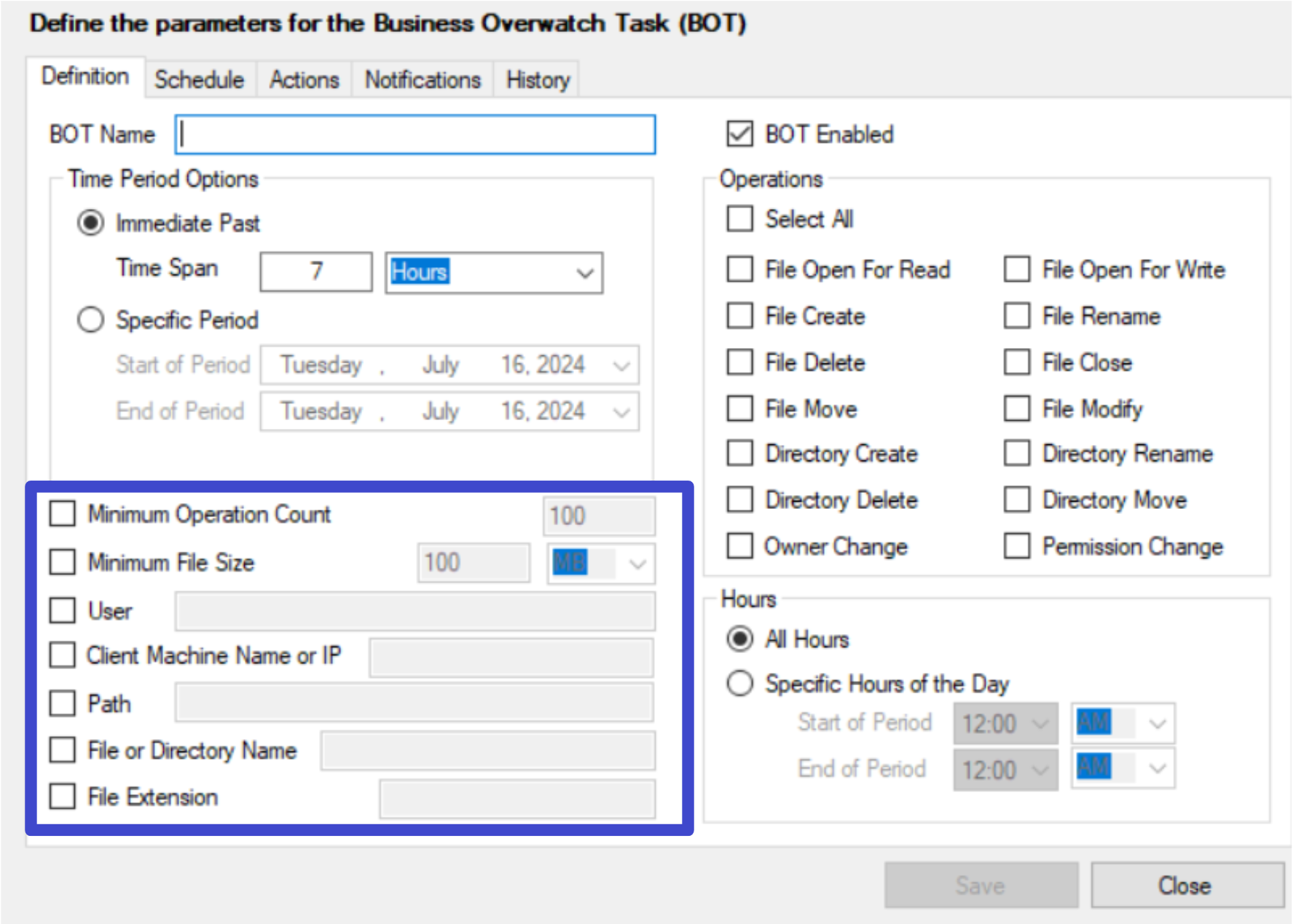 info
info-
The ‘Minimum Operation Count’ defines the minimum number of operations that should match for the BOT to notify the user.
-
The ‘Minimum File Size’ defines the minimum file size that counts as an operation for the BOT.
-
The ‘User’ defines the full name of the user a BOT monitors.
- Leave this field blank if you wish to search for all operations done by all users. This field does not accept account names and does not accept group names, only full names are accepted. Wildcards ("" and "?") can be used (e.g., you can enter “Mark”, which will match all users whose first name is Mark).
-
The ‘Client System name or IP’ defines the computer name/IP a BOT monitors.
- Leave this field blank to monitor access from all computers. This field accepts only one computer name or one IP. Wildcards are used.
- Examples:
- To match a range of IPs, the IP can be entered as “10.20.2.*”, this will match any IP in the range 10.20.2.0 to 10.20.2.255.
- To match only the range of IPs from 10.20.2.1 to 10.20.2.9, the filter “10.20.2.?” is used.
- Examples:
- Leave this field blank to monitor access from all computers. This field accepts only one computer name or one IP. Wildcards are used.
-
The ‘Path’ defines the path the BOT monitors. The BOT will only monitor operations on files or directories that reside on the specified path. Only one path is supported for each BOT. Wildcards are supported (e.g., “\vol\vol0\Users*” will match with any subdirectory of Users).
-
The ‘File or Directory Name’ defines a certain file or directory name to match. Only one file or directory name is allowed. Wildcards are supported (e.g., “Sales” will match all folders/files that contain the word Sales within it.)
-
The ‘Extension’ defines the extension the BOT monitors. The BOT will monitor operations on files with the specified extension. Only one extension is allowed. Wildcards are supported (e.g., “mp?” will match with file extensions as mp3 or mp4).
-
Supported wildcards are ‘*’: Zero or more characters, ‘?’: Exactly one character.
-
Configure BOT Schedule
- On the Schedule tab, select whether the BOT is to run only once or recurrently and select the BOT start time. If you selected the BOT to be recurring, select how often it should run. When the BOT runs, it will notify the administrator about any behavior that matches the BOT that occurred during the specified time period. The minimum recurring time is 5 minutes.
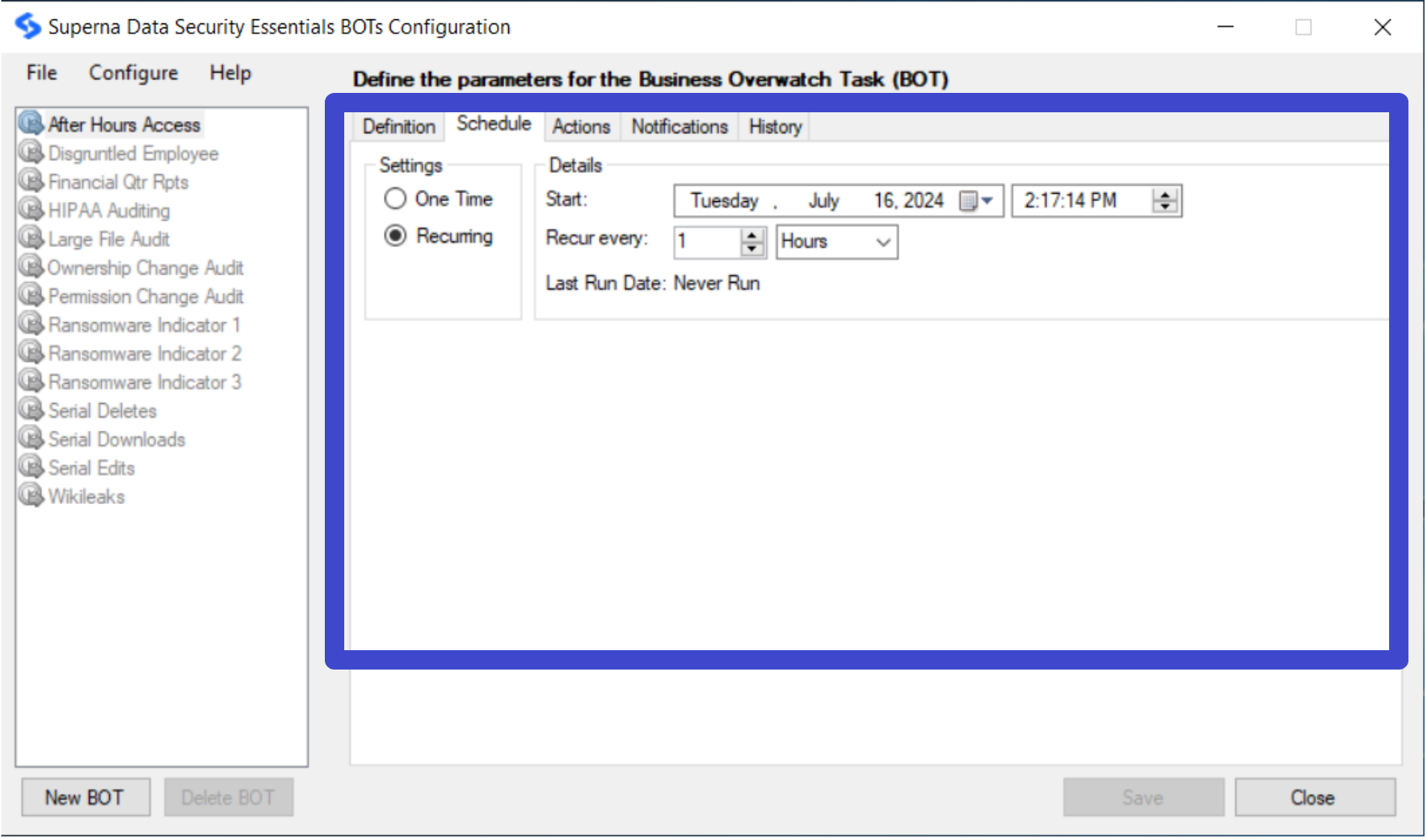
-
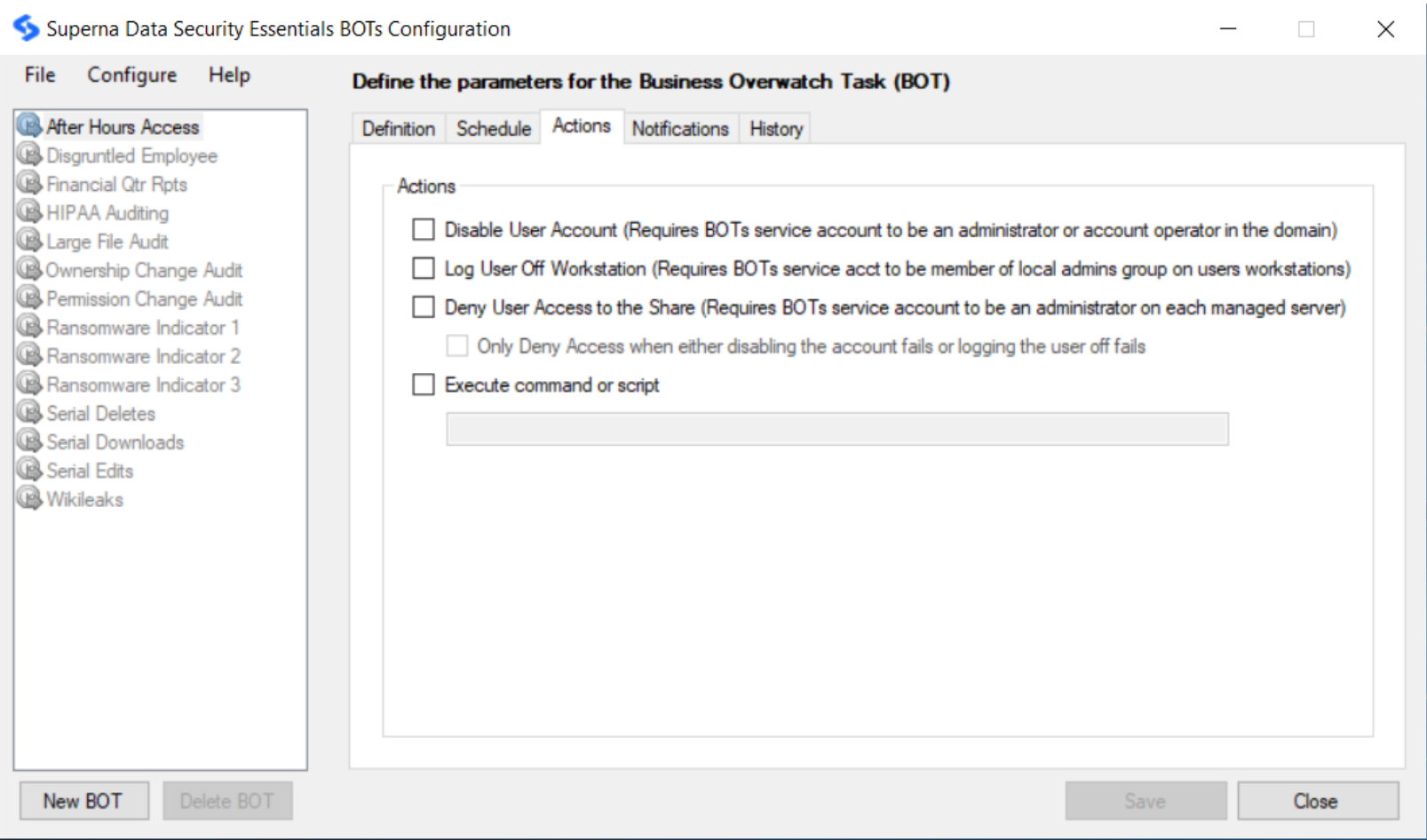
Define Actions for BOT Violations
- From the Actions tab, you can determine which action(s) will be taken if a BOT violation is detected. You may select multiple actions if desired.
-
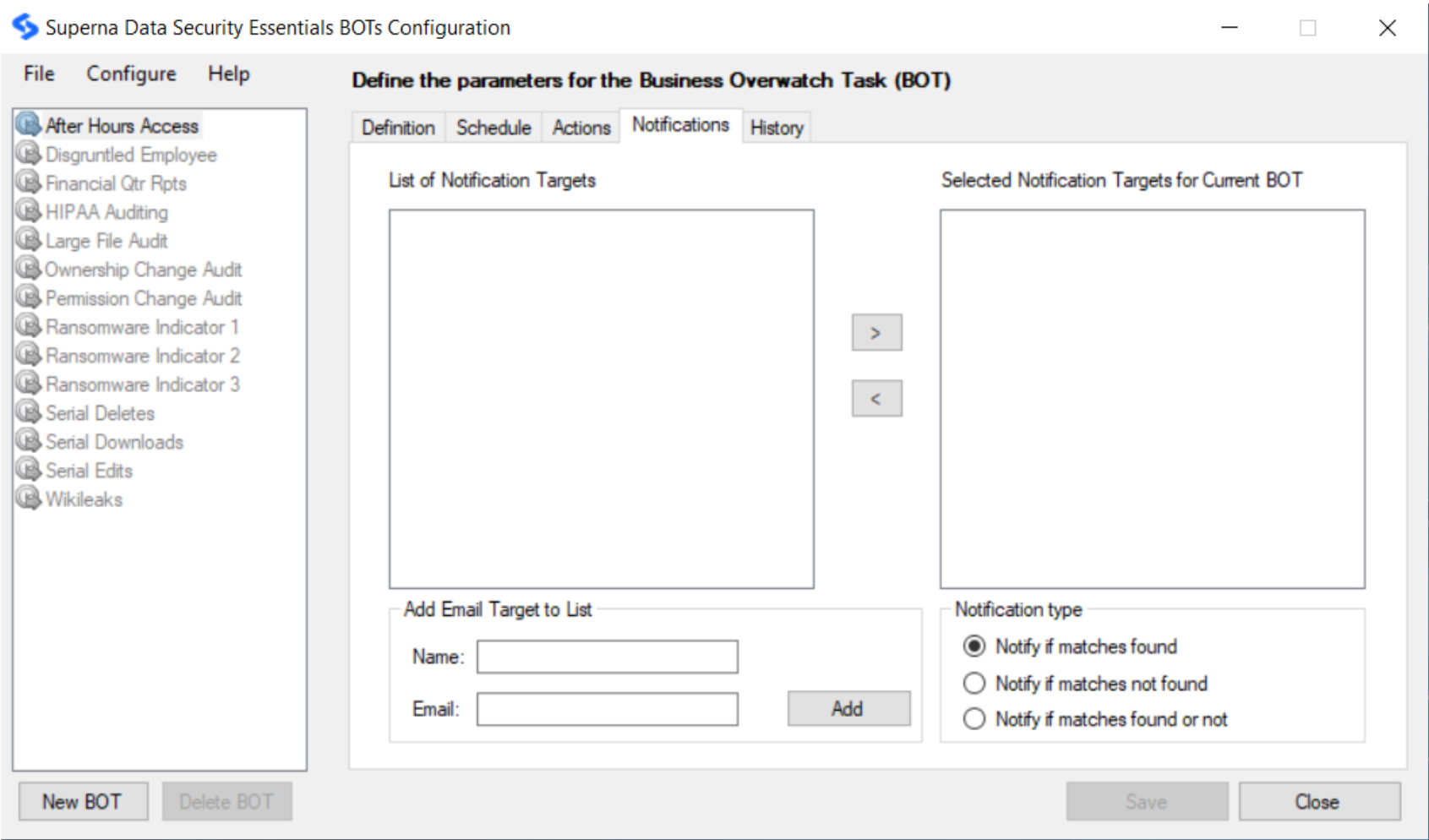
Set Notification Preferences
-
From the Notifications tab, specify the email accounts to receive notifications when the BOT runs. The Selected Notifications Targets lists the recipients of notifications. The Notification Targets lists the available email accounts from which you can select. If you move an email from the Notification Targets list to the Selected Notification Targets list, the BOT will notify these users. You may add email accounts from the Add Email Target panel and specify when notifications should be sent by providing the target name and the email address and filling out the notification type section. Click the Add button.
-
Save changes You must save the changes before selecting another BOT from the existing BOTs list otherwise you will lose your changes. You may choose to close at any time.
-
-
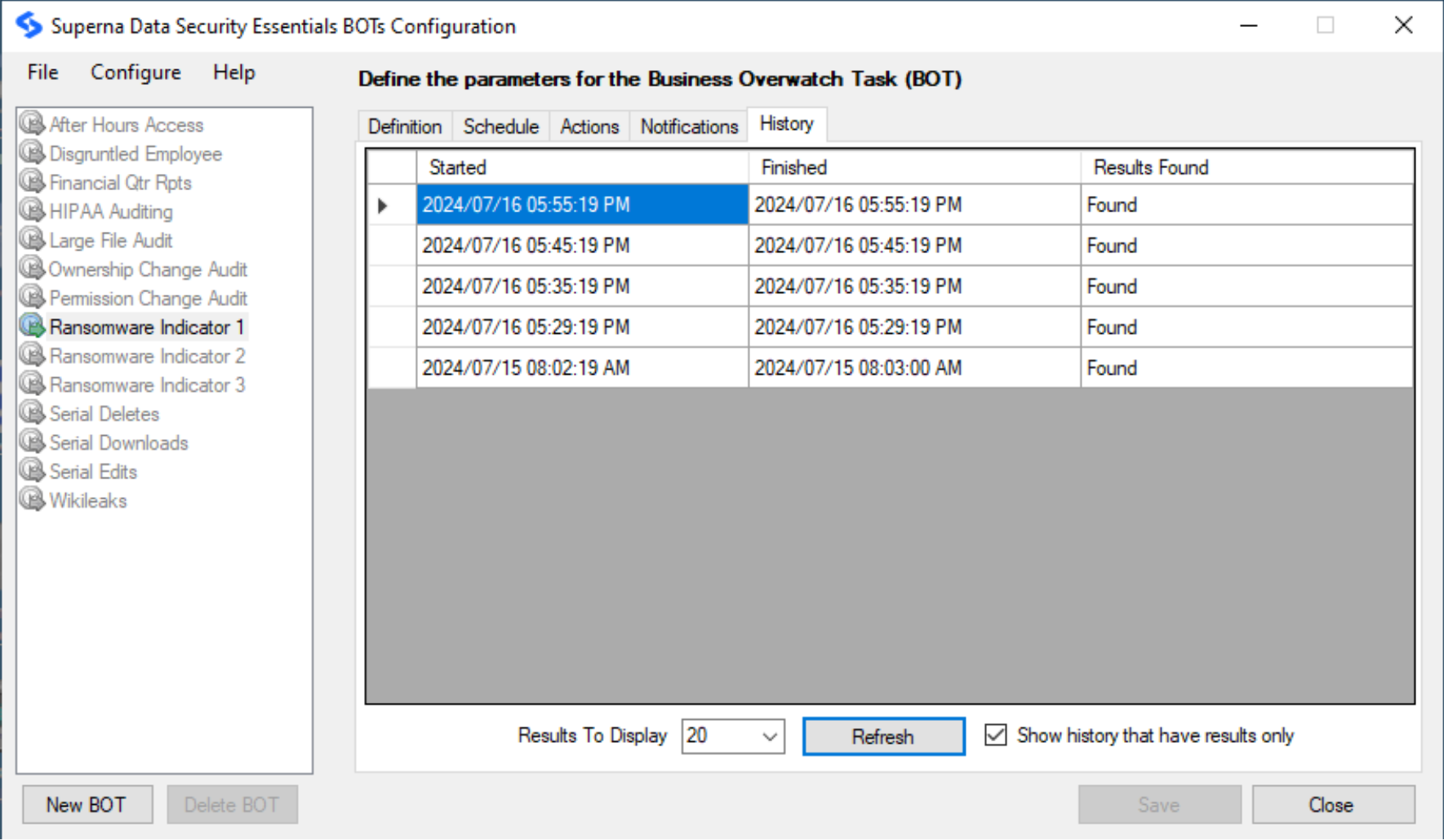
Review BOT History
- Use the History tab to check the scans done along with the matches that the BOT found with the Data Security Essentials database, if any.
 info
infoThe ‘Notify if matches found’ sends an email notification only if the criteria defined in BOT definition is met. The ‘Notify if matches not found’ sends an email notification only if the criteria defined in BOT Definition is not met. The ‘Notify if matches found or not’ sends an email notification every time the BOT executes.
Default BOTs
Data Security Essentials BOTs ship with a set of default BOTs; they provide examples of how Data Security Essentials BOTs are used. The user can also edit the default BOTs to satisfy their needs.
Example BOTs
| BOT Name | Description |
|---|---|
| After Hours Access | This BOT is used to discover any operations done after hours. It runs every day (by default at 8 am) and analyzes the data of the previous 14 hours to see if someone performed any operations. |
| Disgruntled Employee | This BOT discovers whether any user has deleted a large number of files in the last hour. |
| Financial Qtr Rpts | This BOT is used for financial quarterly reports to discover all modifications done to the financial reports directory by any user in the last quarter. |
| HIPAA Auditing | This BOT discovers any suspicious behavior done to the folder that contains health information, ensuring compliance with HIPAA. |
| Large File Audit | This BOT notifies you when a user creates any file larger than 500MB in a specific directory. |
| Ownership Change Audit | This BOT notifies you when a user takes ownership of a file or changes the owner of a file. |
| Permission Change Audit | This BOT notifies you when a user changes the security of a file or a directory. |
| Ransomware Indicators | There are three BOTs that search for ransomware-associated behavior and issue warnings when detected. |
| Serial Deletes | This BOT discovers whether any user has deleted many files in the last hour. |
| Serial Downloads | This BOT discovers whether any user has downloaded many files in the last hour. |
| Serial Edits | This BOT discovers whether any user has edited many files in the last hour. |
| Wikileaks | This BOT discovers problems similar to the Wikileaks problem by detecting whether any user has performed a large number of file copies/downloads in the last 30 minutes. |