Setting up PowerScale OneFS
Introduction
This document outlines the minimum permissions needed for Easy Auditor and Ransomware Defense, and provides setup instructions for PowerScale OneFS.
Minimum Permissions
| Permissions for Easy Auditor | Permissions for Ransomware Defender |
|---|---|
| EASY_AUDITOR_VIEW: View existing reports, queries, and wiretaps. | RANSOMWARE_DEFENDER: View and configure Ransomware Defender. |
| EASY_AUDITOR_MODIFY: Add and update reports, queries, schedules, and wiretaps. | RANSOMWARE_READONLY: Read-only view for Ransomware Defender. |
Please ensure to check the User Roles documentation, which provides instructions on how to assign permissions to users and groups.
Setting up the PowerScale OneFS for Auditing
The Eyeglass Easy Auditor solution allows customers to set policies for both real-time policies and scheduled searches to alert on file actions. Static reports can also be scheduled for more complex, longer-running analytics.
The Easy Auditor solution for PowerScale OneFS requires existing Eyeglass DR cluster licenses for each PowerScale OneFS cluster plus an Eyeglass clustered agent license.
-
Admin User Permissions
- The admin user does not have audit permissions by default. However, the administrator role in the Users Roles icon can be used to add audit permissions to the admin user.
-
Auditor User Setup
- The auditor user is a new user ID that allows separation of duties between DR and non-security audit functions in Eyeglass.
- Separation of Duties is required for compliance with most industry regulations, including HIPAA and PCI.
- Login as the auditor user.
- Change the auditor password.
-
Configure Email Reporting for Audit Administrators
- Login to Eyeglass as an admin user.
- Open the Notification Center at the Eyeglass Main Menu.
- Select the Manage Recipients tab.
- Add a new email recipient and select auditor-only reports from the list.
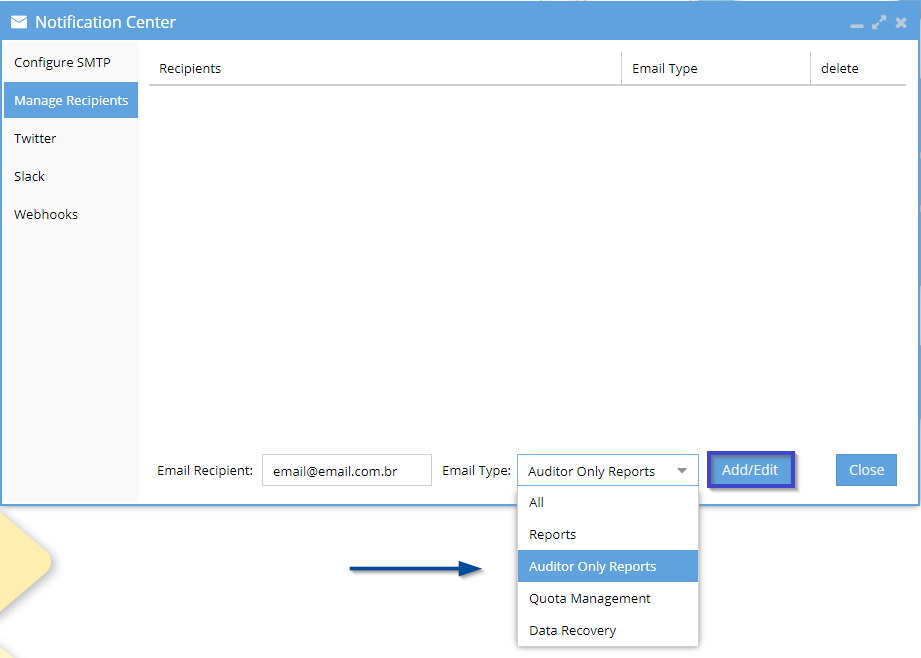
- Select Add/Edit
Setting up the PowerScale OneFS for Ransomware Defense
This section explains how to set up Ransomware Defender. The solution is deployed in a 3-VM cluster, which processes PowerScale OneFS and ECS audit files. Its active-active design maximizes availability, ensuring the system remains operational even during hardware or software failures.
Ransomware Defender actively monitors user behaviors for malicious actions that match ransomware encryption techniques targeting customer files. Network-attached SMB mounts on user workstations expose critical PowerScale OneFS data, and the solution also protects object storage on Dell ECS.
The system provides three levels of detection: Warning, Major, and Critical. As the detection level increases, automated defense options become more robust, allowing for a proactive response to potential threats.
Requirements
ECA Installation Requirement
The Superna Eyeglass Clustered Agent (ECA) vAPP is used by Ransomware Defender. Therefore, a single host for ECA VMs or multiple hosts for high availability is required.
Licensing Requirement
Registered PowerScale OneFS or Dell ECS clusters licensed for Eyeglass DR qualify to be licensed with Ransomware Defender. Each writable cluster requires an agent license and agent maintenance.
The license manager is used to assign licenses.
A system alarm will be triggered if there are insufficient licenses when more writable clusters are detected in audit event messages.
A cluster can be monitored by the ECA without a license if it is a cold or DR cluster.
Additional Requirements
- Eyeglass VM installed.
- Cluster discovery licenses per node or per cluster that need to be managed by the Eyeglass instance.
- Ransomware feature license and a Ransomware agent license for all writable clusters protected by Ransomware Defender.
- CPU limits applied to the ECA cluster object in vCenter.
- Hardware recommendation
User Setup
A built-in role and user account exist to separate the management of Ransomware settings and event monitoring.
- The role Ransomware Defender is assigned with the ability to manage and monitor the Ransomware Defender product.
See User Roles Guide for more details
How to Login
- Login to the Eyeglass appliance using either the admin or rwdefend user account with the default password.
- Click on the Ransomware Defender icon to access the management interface.