Qumulo Installation Guide
System requirements
Ensure you have the following:
-
Valid licenses for Superna solutions.
-
Add a Qumulo user account named "superna" with the permissions defined below.
Permissions Table
Permissions category Permissions name Description Users AD_USE Required to use Active Directory objects. Required for the user lockout and restore user access operations. AD_READ Required to correctly display information about the user when an event is raised in Data Security. LOCAL_USER_READ Grants permission to read local user information on a specific machine. Required for the user lockout and restore user access operations. LOCAL_GROUP_READ Allows reading local group information on a specific machine. Required to list all users in the local user database and for the lockout and restore operations. Network NETWORK_READ NFS exports permissions NFS_EXPORT_READ Grants permission to read NFS export settings and allows writing or modifying NFS export settings. Required for ransomware detection. Relevant in environments using NFS for file sharing. NFS_EXPORT_WRITE Quota QUOTA_READ Permits reading quota settings for storage or user accounts which is required for the Disaster Recovery feature. Replication permissions REPLICATION_REVERSE_RELATIONSHIP These permissions are essential for managing and configuring replication processes. REPLICATION_SOURCE_READ REPLICATION_SOURCE_WRITE REPLICATION_TARGET_READ REPLICATION_TARGET_WRITE S3_BUCKETS_READ SMB permissions SMB_SESSION_READ Required for the user lockout and restore user access operations. SMB_SESSION_WRITE Snapshots SNAPSHOT_POLICY_READ Required for snapshot taking when an event is detected and for the recovery manager to work correctly. SNAPSHOT_POLICY_WRITE SNAPSHOT_READ SNAPSHOT_WRITE -
Add an Active Directory account for name resolution service
This account is solely used to query Active Directory for retrieving a list of AD users to display correctly in the events list.
In most environments, being part of the "Authenticated Users" group is sufficient for basic querying.
The user should have at least read permissions on the user objects within the AD.-
Command:
igls ad addserver set --server=<AD.domain> --basedn=CN=Users,DC=<distinguished_name>,DC=<domain_controller>--logindn=CN=Administrator,CN=Users,DC=<distinguished_name>,DC=<domain_controller>--domain=<AD.domain> --loghost=<ad_server_ip> --ssl=false --port=<port_number>--password=<password>
-
-
The Security Guard appliance requires a dedicated AD user account named "igls-securityguard"
and a network share where that AD user has the necessary access permissions. The network share is created automatically. -
Audit settings for Data Security
To enable Data Security events, enable syslog for Qumulo.
Go to Cluster → Audit and add a new syslog. Enter the IP address of ECA node 2, and save the changes. -
Eyeglass must be operational on the cluster.
Qumulo Deployment and Configuration
Add a cluster using UI
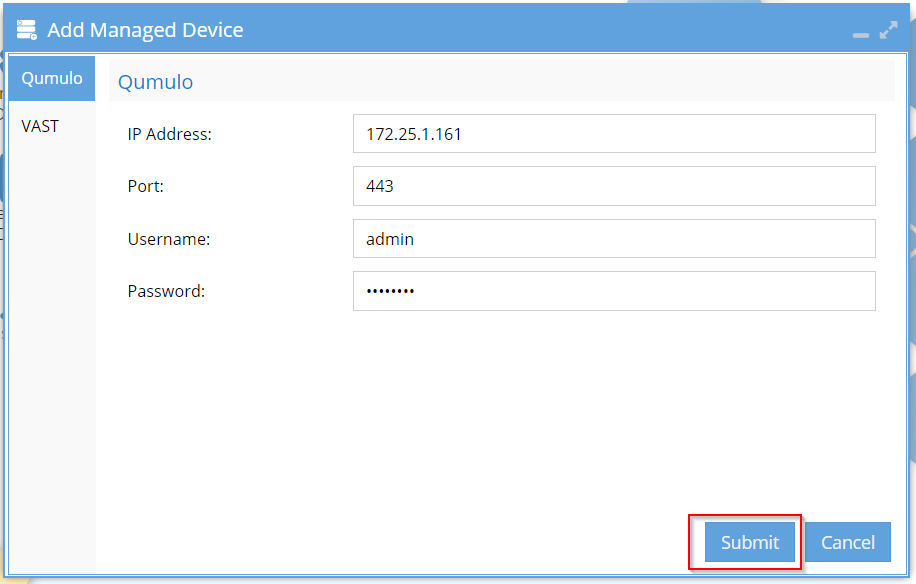
When the cluster is successfully added, the confirmation window will appear.
Open the Jobs menu to check Running Jobs. Wait until the add job is complete, and validate that the cluster can be browsed in the inventory view:
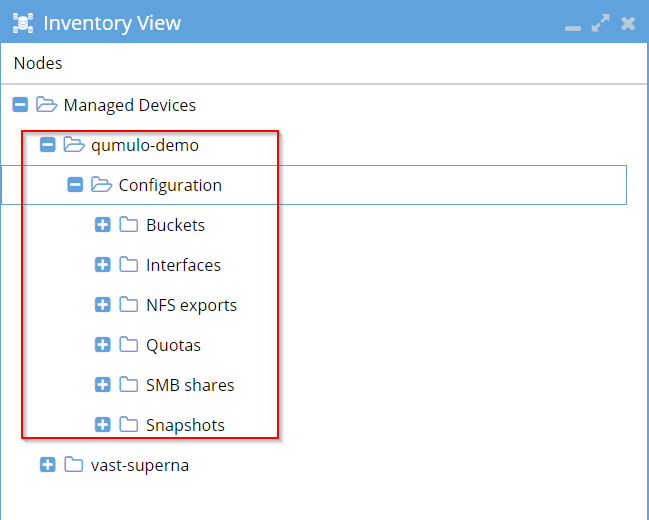
Configuration
To launch Qumulo, use the IP address or open it from the Inventory View.

Enable audit stream
On the Qumulo interface, go to Cluster -> Audit.
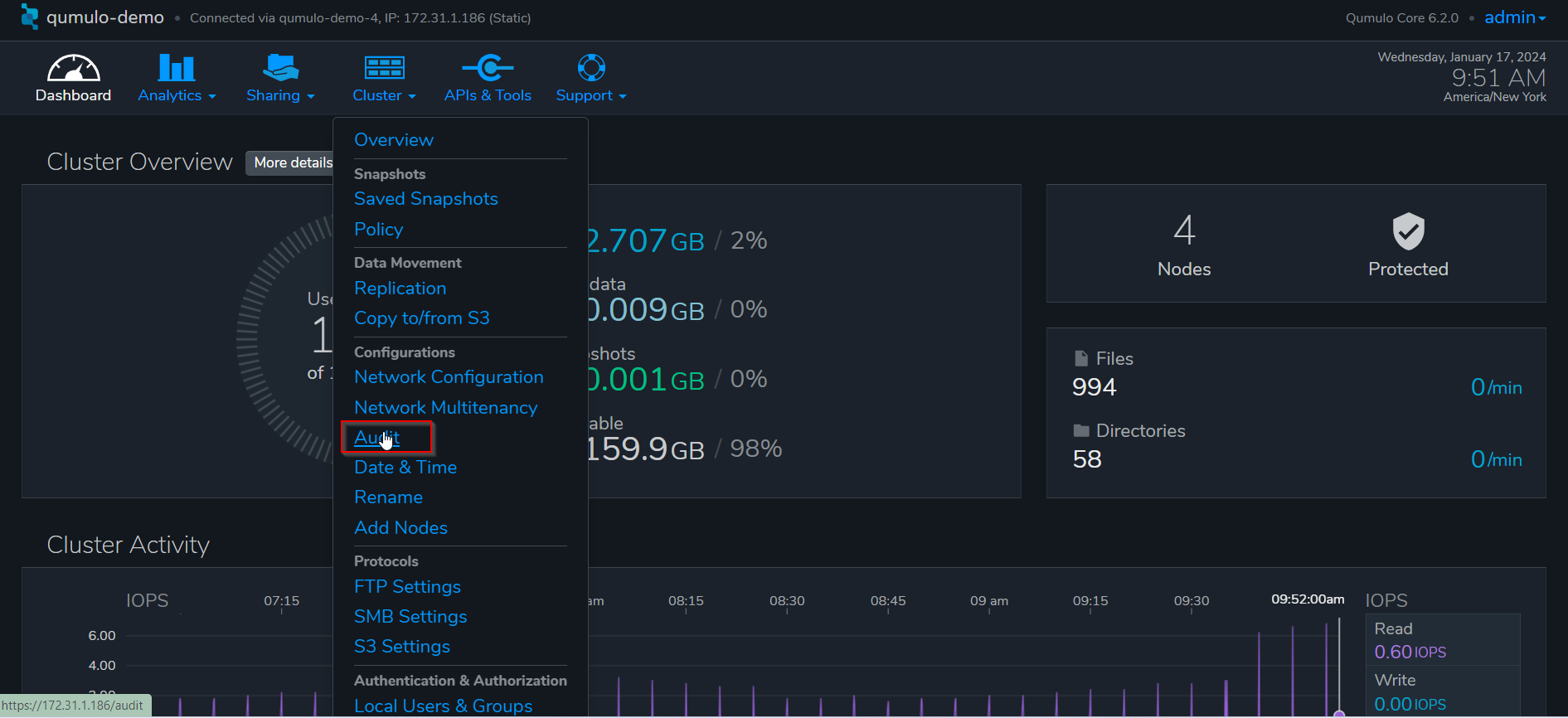
Enter the IP address of ECA node 2, and save
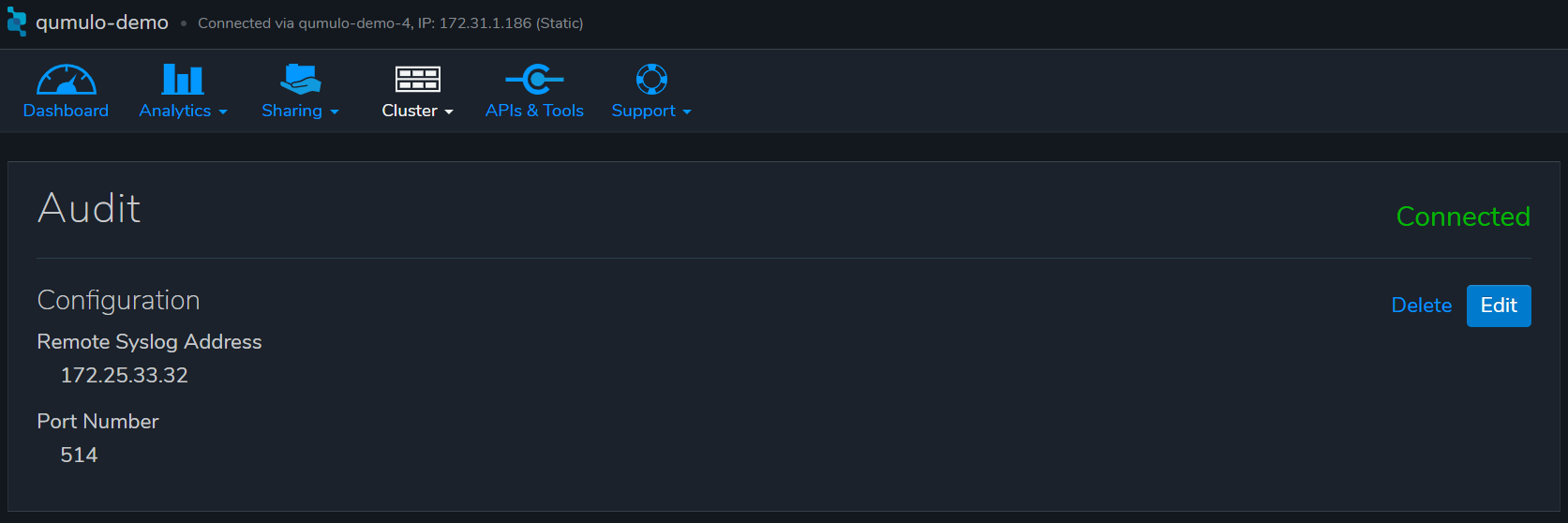
ECA configuration
Add the following parameter to /opt/superna/eca/eca-env-common.conf before cluster up:
export TURBOAUDIT_QM_SERVER_ENABLED=true
Configure the following setting in /opt/superna/eca/eca-env-common.conf to start in Ransomware Only mode:
export RSW_ONLY_CFG=true
After setting up Easy Auditor, this setting will need to be changed to false. Please review your specific requirements to determine if a Ransomware Only configuration is necessary for your environment.
Configure as false to continue cluster up even if no NFS mount (expected because Qumulo uses Syslog):
export STOP_ON_AUTOMOUNT_FAIL=false
Add Eyeglass IP and API token:
export EYEGLASS_LOCATION=
export EYEGLASS_API_TOKEN=
Additional configuration
Kafka Additional Memory:
Additional memory needs to be allocated to the Kafka docker container.
Do the following:
- SSH to ECA1 (user: ecaadmin, password: 3y3gl4ss).
- Open the
docker-compose.overrides.ymlfile for editing:
vim /opt/superna/eca/docker-compose.overrides.yml
- Add the following lines. IMPORTANT: Maintain the spacing at the start of each line.
version: '2.4'
#services:
# cadvisor:
# labels:
# eca.cluster.launch.all: 1
services:
kafka:
mem_limit: 2048MB
mem_reservation: 2048MB
memswap_limit: 2048MB
- Save changes with: ESC + wq!
Zookeeper Retention:
We will be implementing the following changes to prevent zk-ramdisk exhaustion from occurring. When zk-ramdisk reaches 100% utilization, this causes event processing to halt.
Do the following:
- SSH to ECA1 (user: ecaadmin, password: 3y3gl4ss).
_vim /opt/superna/eca/conf/zookeeper/conf/zoo.cfg.template_- Add the following configurations to the bottom of the file:
snapCount=1000
preAllocSize=1000
- Save changes with: ESC + wq!
Cron Jobs:
Cron job needs to be created to restart the fastanalysis docker container on a schedule. Do the following:
- SSH to ECA1 (user: ecaadmin, password: 3y3gl4ss).
ecactl cluster exec "sudo -E USER=ecaadmin ecactl components restart-cron set fastanalysis 0 0,6,12,18 \'*\' \'*\' \'*\'"
- Validate cron job added:
ecactl cluster exec 'cat /etc/cron.d/eca-*'
Cluster up from ECA1 (must be done before configuring auditing):
_ecactl cluster up_