Installation
- Qumulo
- VAST
Qumulo Installation and Configuration
Deploy the most recent Eyeglass and ECA OVF. Download and install the Qumulo installer for each, and run the installation. The current supported versions and links to the support portal for download are below:
| Package | Link |
|---|---|
| Eyeglass OVF | Use Support Portal for download |
| ECA OVF | Use Support Portal for download |
| Eyeglass Installer | Use Support Portal for download |
| ECA Installer | Use Support Portal for download |
Prerequisites - Qumulo
The Security Guard appliance requires a dedicated AD user account, and a network share where that AD user has access permissions.
Eyeglass must be operational on the cluster.
Eyeglass Configuration
Licensing
Log in to Superna Eyeglass and open License Management.
Where Qumulo type licenses are displayed.
Add a Qumulo type license to the system
In order for the UI functionality to be displayed, a Qumulo license must be added via the eyeglass UI. The License Devices tab displays all added devices to the system.
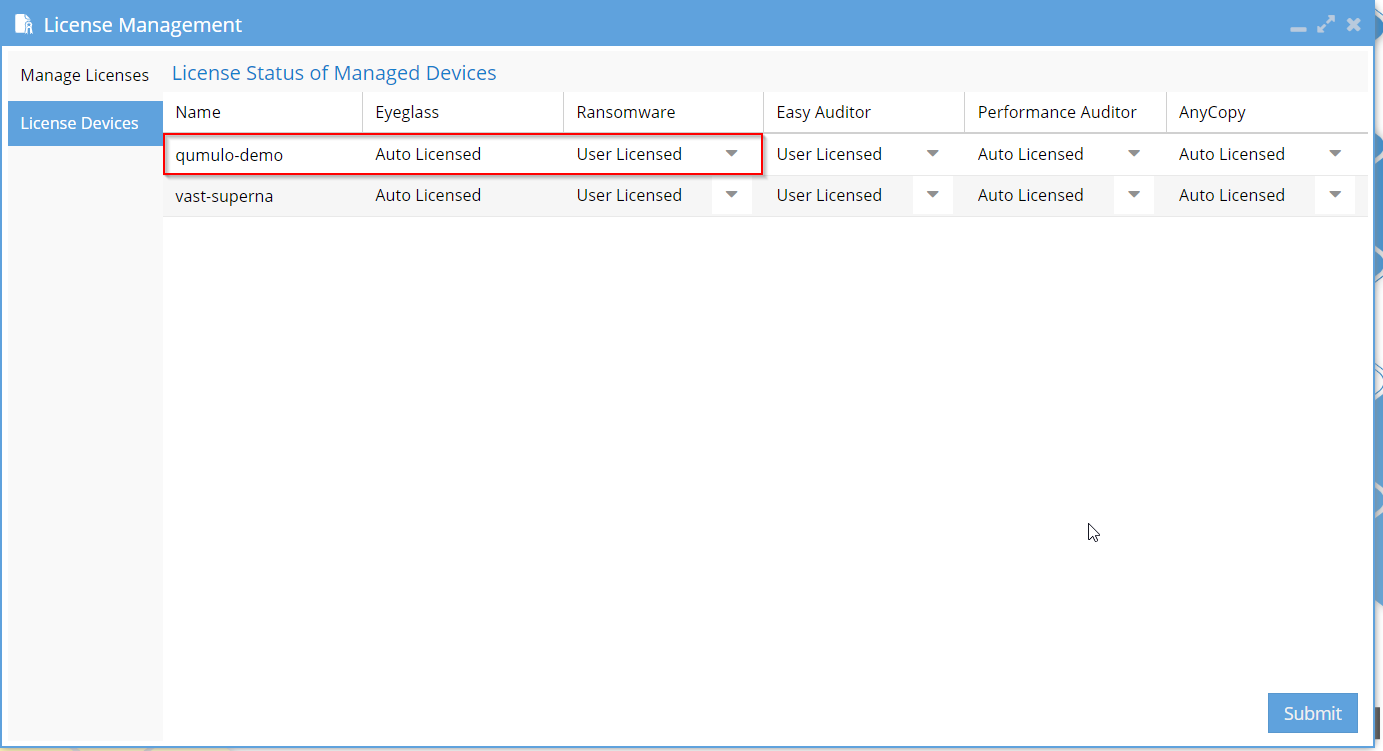
Add a Qumulo cluster via the eyeglass UI
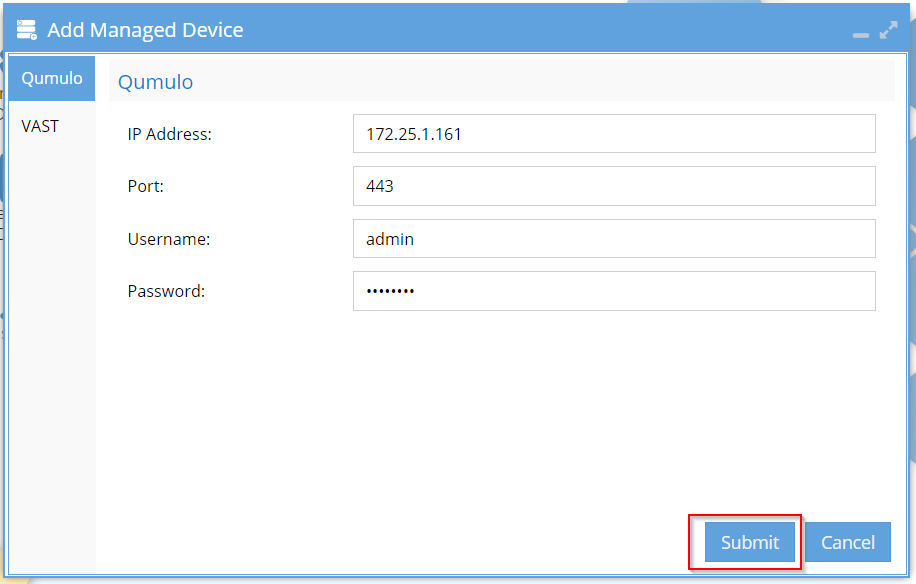
When the cluster is successfully added, the confirmation window will appear.
Open the Jobs menu to check Running Jobs. Wait until the add job is complete, and validate that the cluster can be browsed in the inventory view:
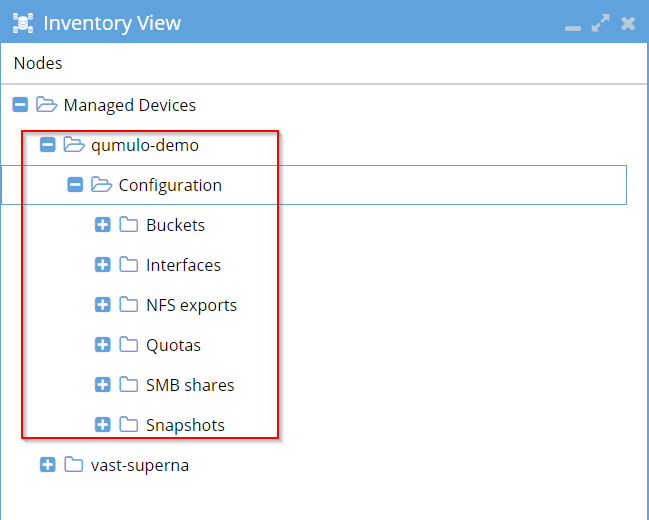
ECA Configuration
Configure Active Directory on Eyeglass
See here for a guide on Eyeglass CLI Commands
Enable Qumulo functionality on ECA
Add the following parameter to /opt/superna/eca/eca-env-common.conf before cluster up:
export TURBOAUDIT_QM_SERVER_ENABLED=true
Configure the following setting in /opt/superna/eca/eca-env-common.conf to start in Ransomware Only mode:
export RSW_ONLY_CFG=true
Configure as false to continue cluster up even if no NFS mount (expected because Qumulo uses Syslog):
export STOP_ON_AUTOMOUNT_FAIL=false
Add Eyeglass IP and API token:
export EYEGLASS_LOCATION=
export EYEGLASS_API_TOKEN=
Kafka Additional Memory
Additional memory needs to be allocated to the kafka docker container.
Do the following:
-
SSH to ECA1 (user: ecaadmin, password: 3y3gl4ss).
-
vim /opt/superna/eca/docker-compose.overrides.yml
-
Add the following lines. IMPORTANT: Maintain the spacing at the start of each line.
services: kafka:
mem_limit: 2048MB
mem_reservation: 2048MB
memswap_limit: 2048MB
Save changes with: ESC + wq!
Zookeeper Retention
We will be implementing the following changes to prevent zk-ramdisk exhaustion from occurring. When zk-ramdisk reaches 100% utilization, this causes event processing to halt.
Do the following:
- SSH to ECA1 (user: ecaadmin, password: 3y3gl4ss).
- vim /opt/superna/eca/conf/zookeeper/conf/zoo.cfg.template
- Add the following configurations to the bottom of the file:
snapCount=1000
preAllocSize=1000
- Save changes with: ESC + wq!
Cron Jobs
Cron job needs to be created to restart the fastanalysis docker container on a schedule. Do the following:
- SSH to ECA1 (user: ecaadmin, password: 3y3gl4ss).
ecactl cluster exec "sudo -E USER=ecaadmin ecactl components restart-cron set fastanalysis 0 0,6,12,18 \'*\' \'*\' \'*\'"
- Validate cron job added:
ecactl cluster exec 'cat /etc/cron.d/eca-*'
Cluster up from ECA1 (must be done before configuring auditing):
- ecactl cluster up
Qumulo Configuration
To launch Qumulo, use the IP address or open it from the Inventory View.

Add ECA node 2 as syslog consumer
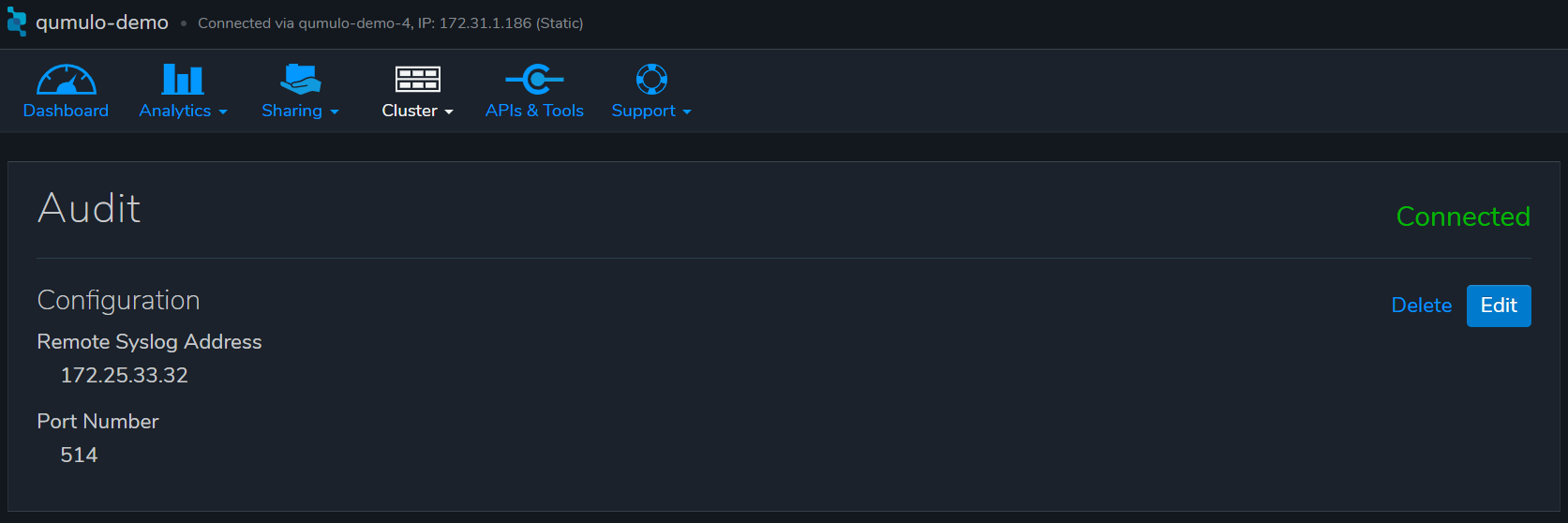
On the Qumulo interface, go to Cluster -> Audit.
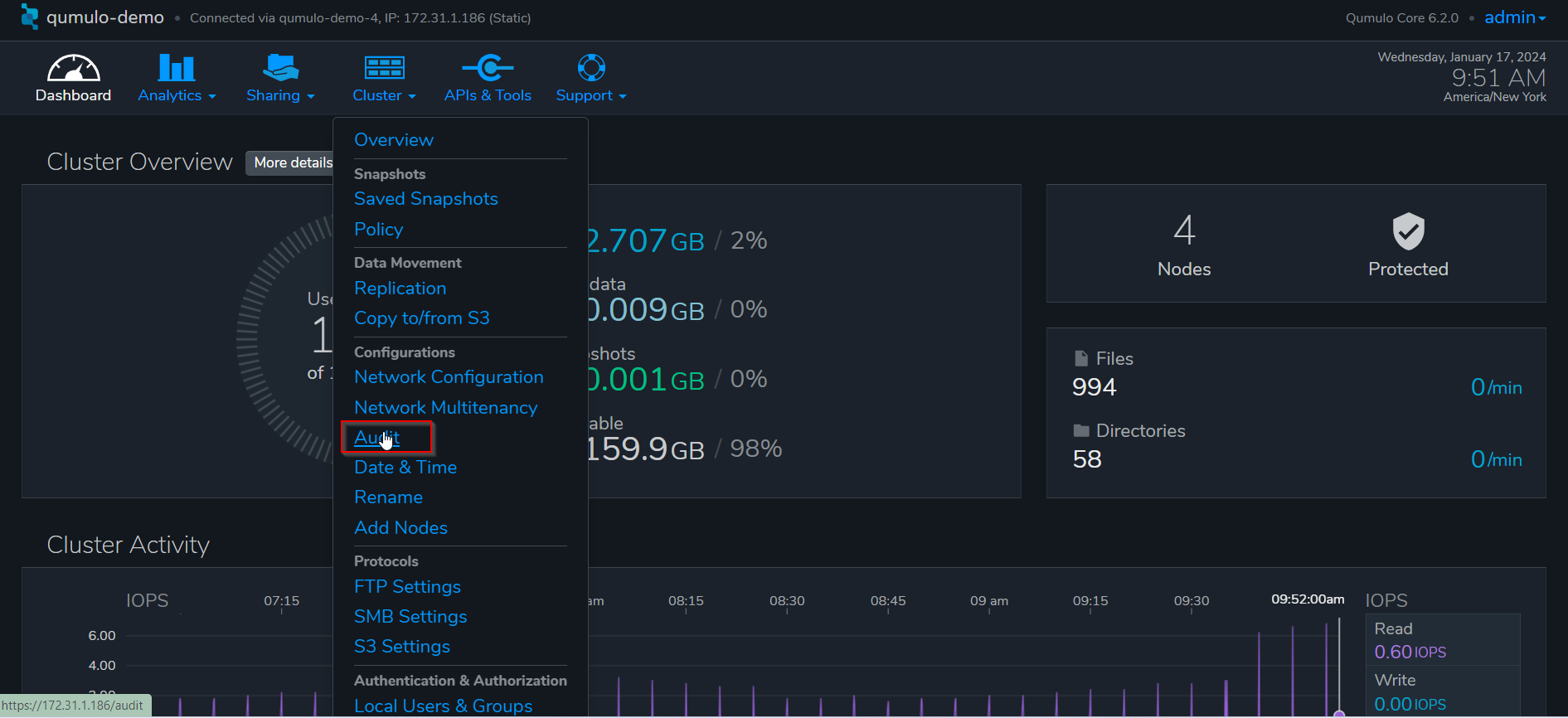
Enter the IP address of ECA node 2, and save
We are in the process of rebuilding our documentation.
For now, see the table below for links to Data Security feature guides from our legacy documentation.
| Feature | Feature description |
|---|---|
| Security Guard (Automated self-test set up) | Security Guard Support |
| Ransomware detection | Detection of ransomware is supported. This includes: - Behavioral analysis - File-extension based analysis - Honeypot file monitoring |
| Protection levels | Determine threat response settings to meet your Company’s Risk Profile |
| Ignored and Monitored List | Ignored or Monitored Paths - Ignored or Monitored Users - Ignored or Monitored Client IPs |
| Snapshots taking | Support for snapshots taking (NFS exports and SMB shares) and critical path snapshots |
| User lockouts | The lockout process identifies all shares the user has access permissions. |
| Recovery Manager | Recovery Manager support |
| Webhooks and Zero Trust API | Outbound webhooks for third-party integrations |
VAST Installation and Configuration
Deploy the most recent Eyeglass and ECA OVF. Download and install the VAST installer for each, and run the installation. The currently supported versions and links are below:
| Package | Link |
|---|---|
| Eyeglass OVF | Use Support Portal for download |
| ECA OVF | Use Support Portal for download |
| Eyeglass Installer | Use Support Portal for download |
| ECA Installer | Use Support Portal for download |
Prerequisites - VAST
Install the latest version of Eyeglass. Request a valid license from Superna.
The Security Guard appliance requires a dedicated AD user account, and a network share where that AD user has access permissions.
Eyeglass must be operational on the cluster.
Adding a VAST Cluster
To add a VAST cluster, select Add Managed Device in the Eyeglass Main Menu at the bottom left corner:

This will open a new view where the management IP address of the cluster and the AD user account authentication data is entered:
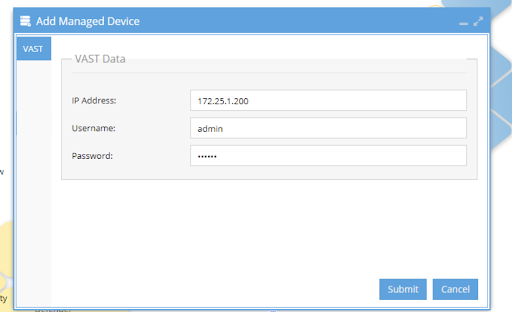
Once the data is added, click the Submit button, and the cluster information will appear in the inventory view:

Deleting a VAST Cluster
To delete a VAST cluster, open the Inventory View, select the cluster to be deleted, open the context menu by clicking the right mouse button and select the entry Delete from the menu.
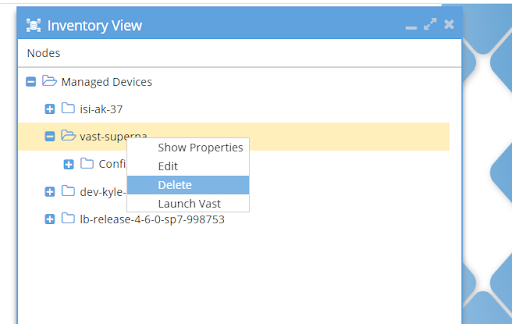
Updating VAST Cluster Properties
To update the properties, select the cluster, open the context menu by clicking the right mouse button and select the entry Edit from the menu.
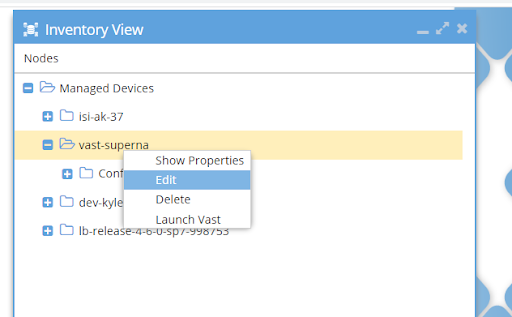
Inventory Collection
The collected inventory from a VAST cluster is shown on the inventory view in Eyeglass; for example: Vast Cluster with a single view
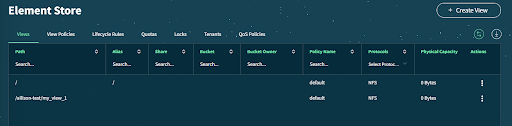
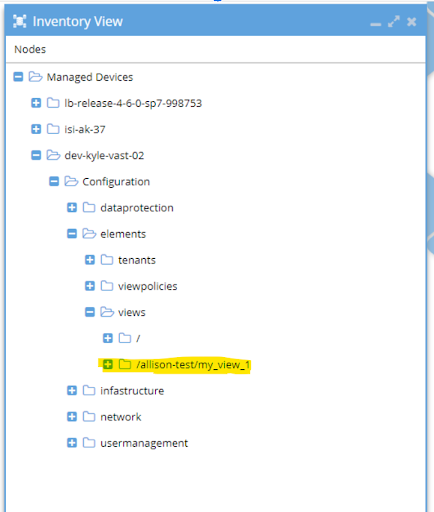
The views from the Vast Cluster displayed in Inventory
Enabling VAST on ECA
The initial step in configuring Vast auditing involves verifying that the Auditing feature is enabled on the Vast machine.
Step 1: Auditing must be enabled on VAST, and root user added to read-access user
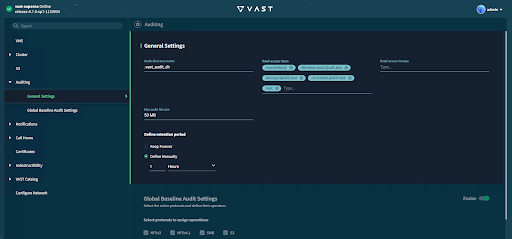
Global audit settings set, OR specific view policy auditing set
In ECA:
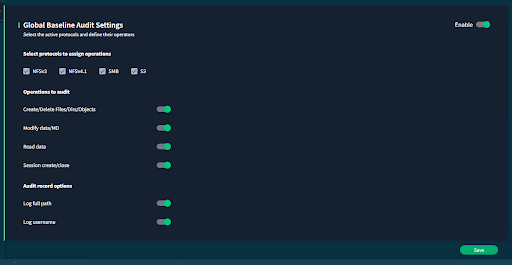
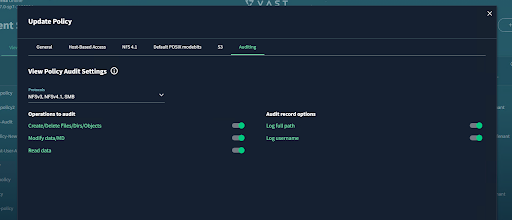
In eca-env-common.conf:
export TURBOAUDIT_VAST_ENABLED=true
export VAST_LOG_MOUNT_PATH="/opt/superna/mnt/vastaudit"
In /opt/superna/eca/data/audit-nfs/auto.nfs:
/opt/superna/mnt/vastaudit/vast-superna/vast-superna --fstype=nfs <vip-pool>:/.vast_audit_dir
After that do ecactl cluster up
Step 2: Create a view for the audit directory
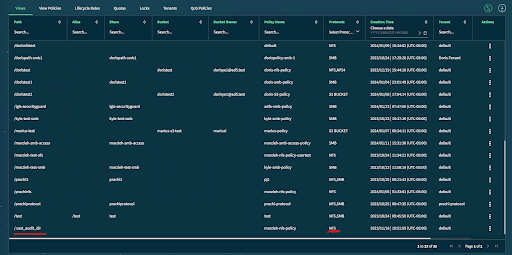
Mount the Audit Path to the ECA node
To establish the connection between the Audit Path and the Turboaudit-equipped ECA node (e.g., node 2), follow these steps:
Before you begin, ensure you have the following information:
- VAST cluster name (Infrastructure → Clusters)
- IP address from the Vip Pool created earlier
- SSH into ECA node 2
- Execute the command sudo su -
1.Create the necessary directory:
mkdir -p /opt/superna/mnt/vastaudit/<cluster_name>/<cluster_name> - Change the current directory to
/opt/superna/mnt/vastaudit/<cluster_name> - Mount the audit path using the following command:
mount -t nfs <protocols_vip>:/.vast_audit_dir <cluster_name> - Confirm the successful mounting of the path by checking the status with:
df -h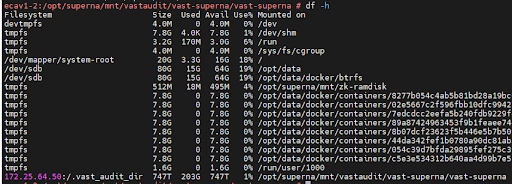
Update Eyeglass
Updating Parameters in /opt/superna/eca/eca-env-common.conf
To incorporate the latest configurations, add and modify the following parameters in the /opt/superna/eca/eca-env-common.conf file:
Enable Turboaudit for VAST
export TURBOAUDIT_VAST_ENABLED=true
Set the VAST Log Mount Path
export VAST_LOG_MOUNT_PATH="/opt/superna/mnt/vastaudit/"
Use RSW-only Configuration
export RSW_ONLY_CFG=true
By making these adjustments, you ensure that the specified parameters are correctly defined within the configuration file, contributing to the effective functioning of the ECA environment.
Configure Recovery Manager
Follow the steps listed in the Recovery Manager for VAST article.
We are in the process of rebuilding our documentation.
For now, see the table below for links to Data Security feature guides from our legacy documentation.
| Feature | Feature description |
|---|---|
| Security Guard (Automated self-test set up) | Security Guard Support |
| Ransomware detection | Detection of ransomware is supported. This includes: - Behavioral analysis - File-extension based analysis - Honeypot file monitoring |
| Protection levels | Determine threat response settings to meet your Company’s Risk Profile |
| Ignored and Monitored List | Ignored or Monitored Paths - Ignored or Monitored Users - Ignored or Monitored Client IPs |
| Snapshots taking | Support for snapshots taking (NFS exports and SMB shares) and critical path snapshots |
| User lockouts | The lockout process identifies all shares the user has access permissions. |
| Recovery Manager | Recovery Manager support |
| Webhooks and Zero Trust API | Outbound webhooks for third-party integrations |