Minimum Permissions
Introduction
Below are the minimum permissions for VAST and Qumulo for Disaster Recovery.
Minimum Permissions
Minimum Permissions for VAST - Disaster Recovery
Below is a table summarizing the minimum VAST permissions required to perform DR/DS operations (e.g., creating security guard shares, snapshots, and managing S3 policies).
-
In the VAST Web UI, navigate to Administrators > Roles:
- Create a new role or edit an existing one.
- Assign the required permissions (Logical, Security, Hardware, Support) as needed.
-
Next, go to Administrators > Managers:
- Select or create the manager account.
- Assign the role created/updated in the previous step.
-
Use this manager account when adding your VAST cluster to Eyeglass.
| Realm | Needed Permissions | Reason |
|---|---|---|
| Logical | Create, View, Edit, Delete | Required to create “security guard” shares or snapshots |
| Security | Create, View, Edit, Delete | Required to manage S3 policies (replication) and generate/remove access keys. |
| Hardware | View (Read) | Required to collect LDAP, NIS, Active Directory, and S3 policy configuration details. |
| Support | View (Read) | Required to collect license inventory from infrastructure. |
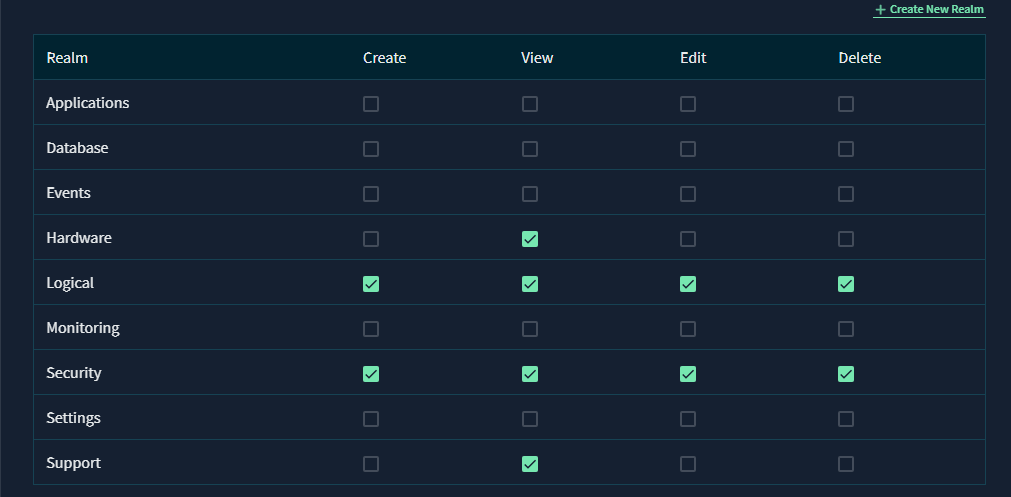
All of the above permissions are needed for both Disaster Recovery (DR) and Data Security (DS).
Minimum Permissions for Qumulo - Disaster Recovery
SSH into the Qumulo cluster using the admin username and password. Run the following commands:
qq auth_create_role --role Eyeglass-Admin --description "Eyeglass-Admin role"
qq auth_add_user --name eyeglassuser --password Gosuperna!
qq auth_assign_role --role Eyeglass-Admin --trustee eyeglassuser
Run the following commands to establish minimum privileges for Disaster Recovery:
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_AD_READ
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_AD_USE
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_LOCAL_GROUP_READ
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_LOCAL_USER_READ
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_NETWORK_READ
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_NFS_EXPORT_READ
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_NFS_EXPORT_WRITE
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_QUOTA_READ
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_REPLICATION_REVERSE_RELATIONSHIP
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_REPLICATION_SOURCE_READ
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_REPLICATION_SOURCE_WRITE
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_REPLICATION_TARGET_READ
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_REPLICATION_TARGET_WRITE
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_SMB_SHARE_READ
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_SMB_SHARE_WRITE
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_SNAPSHOT_POLICY_READ
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_SNAPSHOT_POLICY_WRITE
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_SNAPSHOT_READ
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_TENANT_READ
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_S3_BUCKETS_READ
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_FS_ATTRIBUTES_READ
In customer environments, we have observed that the following additional privilege may be required to successfully run config replication during Disaster Recovery (DR):
qq auth_modify_role --role Eyeglass-Admin --grant PRIVILEGE_FILE_FULL_ACCESS
Be sure to verify this in your specific deployment scenario.